Dynamic coefficient symmetric polynomial-based secure key management scheme for Internet of Things (IoT) networks
- Published
- Accepted
- Received
- Academic Editor
- Joanna Rosak-Szyrocka
- Subject Areas
- Computer Networks and Communications, Network Science and Online Social Networks, Internet of Things
- Keywords
- IoT, Key management, Security, Dynamic coefficient, Connectivity rate, Resource overhead
- Copyright
- © 2023 Liu and Luo
- Licence
- This is an open access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, reproduction and adaptation in any medium and for any purpose provided that it is properly attributed. For attribution, the original author(s), title, publication source (PeerJ Computer Science) and either DOI or URL of the article must be cited.
- Cite this article
- 2023. Dynamic coefficient symmetric polynomial-based secure key management scheme for Internet of Things (IoT) networks. PeerJ Computer Science 9:e1726 https://doi.org/10.7717/peerj-cs.1726
Abstract
Background
With the extensive application and continuous expansion of the Internet of Things (IoT), the access of a large number of resource-limited nodes makes the IoT application face a variety of security vulnerabilities and efficiency limitations, and the operating efficiency and security of IoT are greatly challenged. Key management is the core element of network security and one of the most challenging security problems faced by wireless sensor networks. A suitable key management scheme can effectively defend against network security threats. However, among the key management schemes that have been proposed so far, most of them do not take into account the efficiency in terms of connectivity rate and resource overhead, and some of them even have security risks.
Methods
In this article, based on the symmetric polynomial algorithm, a dynamic coefficient symmetric polynomial key management scheme is proposed to better solve the IoT security problem. In this scheme, the nodes’ IDs are mapped into the elements of the shared matrix M by the identity mapping algorithm, and these elements are used to construct polynomials P(x,y) to generate pairwise keys. The communicating nodes have their own coefficients of P(x,y) and thus have higher connectivity.
Results
The overall performance evaluation shows that the scheme significantly improves the resilience against node capture and effectively reduces the communication and storage overheads compared to the previous schemes. Moreover, the scheme overcomes the λ-security of symmetric polynomial key management scheme, and is able to provide a large pool of polynomials for wireless sensor networks, facilitating large-scale application of nodes.
Introduction
In the network architecture of the Internet of Things (IoT), some new distributed models (Bouarourou, Boulaalam & Nfaoui, 2021; Labib et al., 2021) and multi-hop clustering scheme (Muthukkumar et al., 2022) for heterogeneous wireless sensor networks (WSNs) to efficiently deal with heterogeneous sensors in a dynamic IoT environment, it greatly increases the service life and communication efficiency of node networkst. In the security architecture of the IoT, (Alansari et al., 2023) presents a novel lightweight system for anomaly detection of grayhole, blackhole, and selective forwarding attacks, and a survey (Osamy et al., 2022) reviews and analyzes the research trends related to the utilized artificial intelligence (AI) methods for IoT and the potential enhancement of IoT. In terms of key management, due to the complexity of the structure and high mobility of the IoT structure, the key management strategy based on static implementation cannot be directly applied to the IoT environment. In order to deal with the drawbacks of security and efficiency of the Internet of Things, the design of key management scheme has become one of the key breakthroughs to provide a secure and efficient IoT environment for key negotiation and secure communication between users. At the same time, compared with the common computer network key management model, the key management model oriented to IoT must meet the integrity, reliability, privacy and anonymity, non-repudiation and other characteristics, security and efficiency become the basic standards to measure its availability. Therefore, the IoT needs to design a more appropriate security key management technical solution to solve the security problem.
In order to reduce the energy overhead of wireless sensor networks in the IoT environment and improve network security, several security solutions have been proposed in the literature. Blundo et al. (1998) proposed a scheme in which all nodes use a common polynomial to establish a pairwise key. This simplifies the process of establishing a shared key and has a high connectivity rate between sensor nodes. In Liu, Ning & Li (2003), the authors presented a protocol using grid-based key predistribution and random subset assignment. This scheme further extends the idea of a polynomial to establish pairwise keys. In random subset assignment, nodes select a set of polynomials from a pool and use the same polynomials in selected polynomials to establish pairwise keys. Das & Sengupta (2008) proposed a deterministic group-based key pre-distribution scheme based on a hierarchical wireless sensor network using bivariate polynomials over a finite field. Zhang, Li & Li (2018) developed another key predistribution for pairwise key establishment, which fuses polynomial pool-based and random key predistribution.
Reegan & Baburaj (2017) have proposed a triple key distribution scheme based on polynomial and multivariate mapping, aiming at the problem that the security performance of previous schemes decreases with the increase of the number of damaged nodes. And an improved energy-saving key distribution and management scheme has been proposed by Chakavarika, Gupta & Chaurasia (2017). This scheme is scalable in terms of storage cost and computation cost. The security of network is improved by introducing encrypted random numbers in the key updating stage. In order to solve the memory overhead problem of q-composite scheme, Gandino, Ferrero & Rebaudengo (2017) proposed a new protocol q-s-composite to improve the efficiency of memory management. Albakri & Harn (2019) proposed a group key pre-distribution scheme based on probabilistic polynomials. Which significantly reduces the probability of sensor being attacked by node capture, and improves the security of wireless sensor networks. Li et al. (2020) proposed a secure random key distribution scheme aiming at the shortcomings of q-s-composite scheme in literature (Gandino, Ferrero & Rebaudengo, 2017), which could not resist node replication attacks, combining localization algorithm with voting mechanism. To support the detection and cancellation of malicious nodes, and further modify parameters to resist node replication attacks. In order to solve the security of key management and IoT security performance index optimization problems, Harn, Hsu & Xia (2021) proposed a novel key distribution scheme. The key distribution protocol only needs logical XOR operation, which is much faster than other schemes. Wang et al. (2020) proposed a WSN layer-cluster key management scheme based on quadratic polynomial and Lagrange interpolation polynomial is proposed. Nafi, Bouzefrane & Omar (2020) proposed a new lightweight matrix-based key management protocol for IoT network. Sharma & Purushothama (2022) proposed a new and efficient scheme (BP-MGKM) for secure multi-group key management based on bivariate polynomial. Najafi & Babaie (2023) proposed approach, a lightweight hierarchical key management approach, generating shorter and more secure keys due to the use of a hierarchical structure based on the position and remaining energy of nodes. Msolli et al. (2023) proposed the key management scheme with pool-hash for the establishment, which exposes a new key pool contains original keys and other hashed admit the same identities thus new session keys transmitted in sensors nodes are established during the discovery and path key phases. Taurshia et al. (2022) presented a novel Group Key Management scheme for Low-Resource Devices (GKM-LRD) to offer key management service to groups in IoT applications. Nafi et al. (2022) proposed a new key management protocol aiming to secure communications before and after key establishment, used hash and one–one functions to achieve security during the key establishment process. Rezaeipour & Barati (2022) presented a key management protocol that delivers services such as message confidentiality, integrity, and authenticity to wireless sensor networks by handling keys generation, distribution, and maintenance. Kandi et al. (2022) proposed a novel decentralized blockchain-based protocol for the IoT, balanceing the loads between nodes according to their capabilities. Wei et al. (2021) proposed two space-efficient Bitcoin-compatible key management schemes for the lighting network, based on the hash function and trapdoor one-way function, respectively.
However, for all these solutions, there are shortcomings in the overall performance of connectivity, energy consumption, and security. Especially, a small number of compromised nodes may affect the majority of pairwise keys. This greatly restricts the maximum number (nodes’ limitation number) of nodes the sensor network can hold if the polynomial is unconditionally secure. While increasing the safety threshold λ of the polynomial f(x,y), these schemes are able to make the nodes’ limitation number λ a little enlarged. But it will make nodes suffer from some more serious problem, such that polynomials can extremely enhance the computation and storage overhead at the same time.
Making node communication of these schemes more secure requires a new mechanism to address the λ-secure problem. In addition, we should also consider the following questions: as some nodes are captured, the communication security of other nodes will be directly affected, and all nodes could even be compromised. It should be noted that the energy, storage and communication overhead of sensor nodes are limited. The proposed scheme should maintain high node connectivity and low energy consumption.
Our scheme has better resilience to node capture attacks, a high connectivity rate between nodes, and can considerably reduce the communication and storage overhead. The contributions of this article are summarized as follows:
Offers more effective resilience to node capture attacks for the λ-secure problem and has better resistance than other key management schemes.
The wireless sensor network has a high connectivity rate. Our scheme uses an identity mapping algorithm to map a series of coefficients of , and each pair of communication nodes is able to establish a pairwise key.
Low computational overhead. Even though the phase of pairwise key establishment consumes more energy than the other key management schemes, the node’s chip is sufficient to deal with polynomial and hash algorithms.
Low communication overhead. All communication nodes exchange identity information with each other, and the sensor network directly implements the identity mapping algorithm with the identity information of sensor nodes to get pairwise keys. There are no extra communication streams, except for identity information, during the process of pairwise key establishment, which can greatly reduce communication overhead.
Low storage overhead. With a value of λ = 7, our scheme in pairwise key establishment generates quite a small amount of code. The shared matrix M can generate a series of coefficients of according to the sensor node’s ID, and the sensor network of a head-cluster node is able to hold 1.75 × 105 nodes, which meets the requirements of many scenarios.
The structure of the article is as follows. “Preliminaries” describes the preliminaries. “Overview of Proposed Scheme” proposes our scheme with dynamic coefficient symmetric polynomials including key pre-distribution and key agreement phase. In “Theoretical Analysis”, we analyze some classical security. “Performance Analysis” presents a comparative study and simulation results. “Conclusions” presents the conclusion of this article.
Preliminaries
In this section, we introduce the network model and background, as well as explain the symbols used and their descriptions in this article.
Notation
Table 1 shows the notation used in the article.
| Notation | Description |
|---|---|
| IDNm | Identity of node Nm |
| Hash() | hash function |
| Klm | The pairwise key between nodes Nl and Nm |
| lk | The length of key. Note that each generated key takes the same storage as a coefficient of the λ-degree polynomial. |
| lID | The length of a node or key identifier |
| q | q is a prime number that is large enough to accommodate a cryptographic key, where lk = log2 q |
| |ω| | Size of polynomial pool |
| λ | The security threshold |
| N | The number of sensor nodes in a network |
| τ | The number of polynomials preloaded in each node |
| s | The number of keys preloaded in each node |
| XOR operation |
Network model
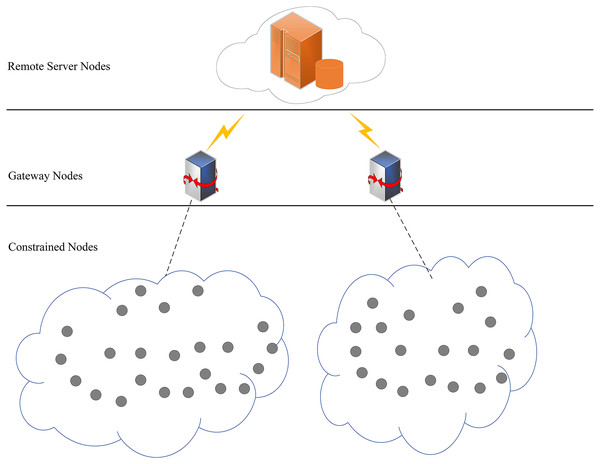
Our scheme is suitable for a distributed network architecture, which consists of remote server nodes, gateway nodes and sensor nodes. All sensor nodes in the network have the same resources with the functions of sensing, collecting and transmitting data. Moreover, these sensor nodes are able to communicate with each other. Figure 1 shows the network model we have assumed.
Figure 1: Network model.
Overview of proposed scheme
In this section, we describe the key management scheme of dynamic coefficient symmetric polynomial for IoT networks, which has two phases: pairwise predistribution phase and pairwise key agreement phase. In the following, we describe the details of each phase.
Key pre-distribution phase
(1) Before nodes are deployed, each node stores the information in advance, including a unique node ID and a hash function.
(2) Node Nl (l = 1, 2, , N) is preload the shared matrix M. N indicates the number of nodes in the network. The size of M is , and element ai,j (i, j = 0, 1, 2, , λ) is over a finite field F(q), where q is a prime number that is large enough to accommodate a cryptographic key.
(1)
Key agreement phase
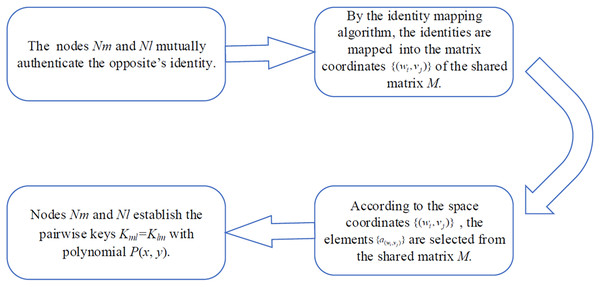
The pairwise key is used for end-to-end unicast communication. Communicating nodes authenticate each other’s identity, construct the matrix coordinates and coefficient set of , and establish a pairwise key, as shown in Fig. 2.
Figure 2: Pairwise key establishment.
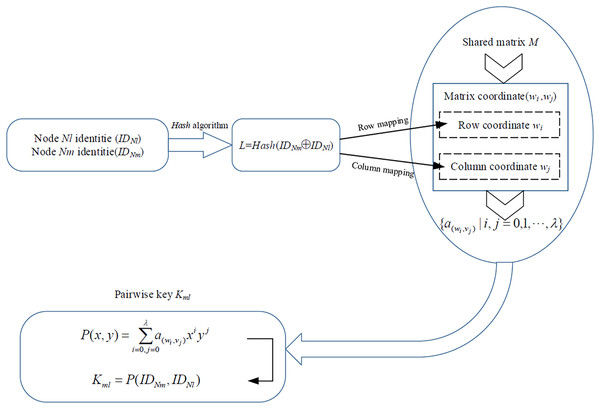
Construct matrix coordinate set Cml and coefficient set Aml. Nodes Nl and Nm map their identities to matrix coordinates (wi,vj) of M and obtained the element from M by the matrix coordinates (wi,vj). Figure 3 shows the identity mapping algorithm.
Figure 3: Identity mapping algorithm.
(1) Nodes Nl and Nm obtain the mapped identity,
(2)
(2) Nodes Nl and Nm output more than 2t (λ + 1) bits of fixed-length data.
(3)
(3) The first t(λ + 1) bits in L are mapped to the row coordinate wi of M as
(4)
The length of wi (0 ≤ i ≤ λ) is fixed at t bits with , indicating the row coordinates of M. The output L of the hash function is binary and must be converted to decimal form. For instance, can be expressed in decimal form as w1 = 0 × 24 + 1 × 23 + 0 × 22 + 1 × 21 + 1 × 20 = 11.
(4) The next t(λ + 1) bits in L are mapped to column coordinate vj of M as
(5)
The length of vj (0 ≤ j ≤ λ) is fixed at t bits with , indicating the column coordinates of M. Like wi, vj is binary and must be converted to decimal form.
(5) Nodes Nl and Nm generate the matrix coordinate set Cml of symmetric polynomial P(x,y), with row coordinates wi and column coordinates vj,
(6)
The coefficient set Aml of P(x,y) is established by Cml, and then used as coefficients of P(x,y),
(7)
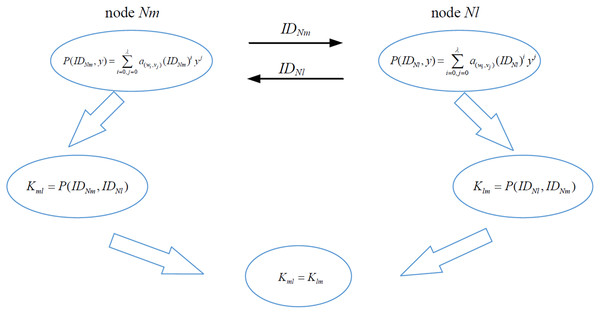
The communication nodes establish pairwise keys with P(x,y). Nodes Nm and Nl respectively construct the pairwise keys Kml and Klm, as shown in Fig. 4, according to the elements of M, as
Figure 4: Pairwise key establishment of nodes Nl and Nm.
(8)
(1) When node Nm executes P(x,y), the input terms of the variable x and y are x = IDNm, y = IDNl,
(9)
(2) When node Nl executes , we input x = IDNl, y = IDNm, and
(10)
(3) Since the polynomial P(x,y) is symmetric, Kml is equal to Klm, and
(11)
So that nodes Nl and Nm have established a pairwise key, i.e., when node Nm communicates with node Nl, they have a common coefficient set Aml for P(x,y). The coefficient sets A of P(x,y) are different in distinguishing pairs of communicating nodes. For example, when communicating, two pairs of nodes (Nm, Nl) and (Nm, Nd) in sensor network have different coefficient sets Aml and Amd, i.e., the attacker cannot use Lagrange interpolation to reconstruct P(x,y).
Theoretical analysis
In this section, we evaluate the λ-secure of symmetric polynomial and size of polynomial pool. Theoretical analysis shows that the proposed scheme can effectively address the λ-secure, and also has a large enough size of polynomial pool to resist brute force attacks.
λ-security of symmetric polynomial
The key management scheme based on a symmetric polynomial uses the polynomial.
(12)
For Formula (12), when we obtain more than IDs and its pairwise keys, this information can form a matrix equation.
(13)
The coefficient matrix W and augmented matrix are seen as Eqs. (14) and (15). When , Eq. (19) has a unique solution, known from related theorems of linear equations.
(14)
(15)
For a hierarchical network with d nodes sharing one polynomial P(x,y), every pair of communication nodes shares the same (λ+1)2 coefficients selected from M, thus establishing d pairwise keys. In theory, reconstructing P(x,y) in λ-degree by Lagrange interpolation requires at least (λ+1) nodes’ information containing (λ+1) polynomial values and (λ+1) IDs. Lagrange interpolation is formulated as
(16)
Obviously, with fewer than λ sensor nodes, the attacker obtains insufficient information to reconstruct P(x,y) by Lagrange interpolation. The proposed key management scheme maps the IDs of communication nodes to different elements aij (i, j = 0, 1, , λ) in M by identity mapping algorithm, and uses these elements aij (i, j = 0, 1, , λ) as coefficients of P(x,y). Since every node has a unique ID, the selected elements aij (i, j = 0,1, , λ) are also different. Hence it is difficult for attackers to reconstruct P(x,y) by Lagrange interpolation.
Size of polynomial pool with different λ
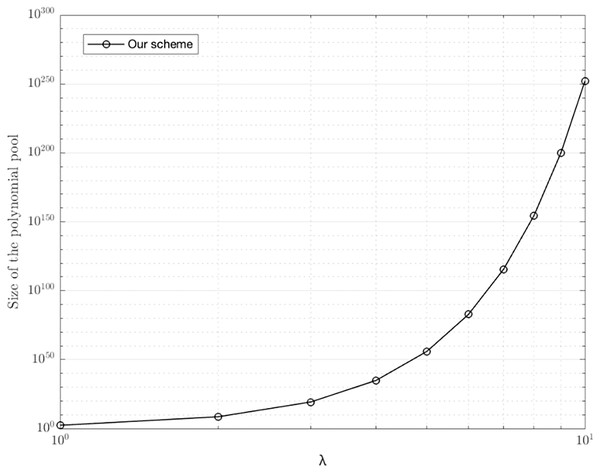
Due to the limitation of λ and t, our scheme uses the hash function of length is 2t(λ +1) bits, which makes coefficients to be combined polynomials. That is, our key management scheme generates a polynomial pool ω containing large polynomials, and each node selects a polynomial from the polynomial pool. In other words, every node in the network has the probability to carry a polynomial from the polynomial pool. Given the security, our scheme should put a limit on the maximum nodes. Figure 5 shows the size of polynomial pool |ω| with different λ. When λ = 3, our scheme can generate a polynomial pool holding 1.84 × 1019 polynomials, allowing our scheme to be used in most scenarios. In addition, our scheme is able to well resist brute force attacks. If someone wants to obtain a pairwise key, they should obtain the coefficients of P(x,y) from the shared matrix M. There are a total of possibilities for an attacker to repeat. When λ = 3, our scheme can generate a polynomial pool holding 1.84 × 1019 polynomials, where it's hard for an attacker to repeat so many times.
Figure 5: Size of polynomial pool with different λ.
Performance analysis
We have conducted a comparative study of a number of related schemes, carried out scientific research, collected data through compliant methods, and evaluated the performance of our scheme through realistic simulations, including the resilience of node capture, connectivity, and resource overhead (energy, memory, and computation) in the pairwise key establishment process.
Resilience against node capture
A proper key management scheme should resist attacks while the network continues its normal operation. The main security threat to the proposed solution is the λ-secure. The security analysis of the new scheme proposed in this section mainly analyzes its resilience to node capture. Resilience is computed as the fraction of links compromised in non-compromised nodes. When the number of nodes is large enough in the network, the output values of hash functions will collide, and communication nodes will hold the same output value L of the hash function and P(x,y). Security analysis shows that our scheme not only offers more effective resilience to node capture attacks for the λ-secure, but has better resistance to node capture attacks compared with the other key management scheme.
Probability of at least one matrix being broken
Denote that Si is an event in the ith polynomial P(x,y) is cracked . All coefficients aij (i, j = 0, 1, , λ) selected from M can be combined into |ω| different kinds of polynomials. The probability that one of these polynomial P(x,y) occurrence in a node is . Cx is an event that x nodes are compromised in a network.
(17)
We have,
(18)
It is obtained by union bound,
(19)
It is equal probability for each P(x, y) to be broken. That is,
(20)
Therefore,
(21)
The total number of terms in P(x,y) is . Because every coefficient aij (i, j = 0, 1, , λ) in P(x,y) is different, the safety threshold of the proposed scheme is . We have,
(22)
Therefore we get the following upper bound:
(23)
The fraction of compromised network communication
c is a link that two uncompromised nodes establish a communication with a common key K. Bi is a event that one common key K of two nodes is derived by compromised key space Si.
(24)
Since the link c is built securely by one common key K that derived by a key space Si. Due to events are mutually exclusive and probability of occurrence in Bi is equally, therefore,
(25)
Note that represents an event that “key K was derived by Si.”
(26)
Event is independent of the events Cx and (S1 is compromised).
(27)
The probability of event is equal to the probability of event “the link c established by space Si”. Each key space appears randomly and uniformly in a node.
(28)
Therefore, the probability of event that one link is compromised when x nodes captured show as
(29)
Assume that w secure communication links do not involve any of the x compromised nodes. Denote R as the event “the rest of w secure communication links except x compromised nodes participating in”. That is,
(30)
The above equation indicates that, given that x nodes are compromised, the fraction of the compromised secure communication links outside of those x compromised nodes is the same as the probability of one P(x, y) being compromised.
Comparison to previous work
Although many key managements based on Blundo’s scheme can ensure that all nodes are able to be connected, they are faced with λ-secure. Security analysis shows that our scheme not only offers more effective resilience to node capture attacks for the λ-secure, but has better resistance to node capture attacks compared with other key management schemes. Table 2 lists some different schemes of comparison used in this article.
| Scheme | Liu, Ning & Li (2003) | q-composite scheme (Chan, Perrig & Song, 2003) | Our scheme | Zhang, Li & Li (2018) | |
|---|---|---|---|---|---|
| s | − | 20 | − | 12 | |
| |S| | − | 340 | 200 | − | − |
| q | − | 2 | 3 | − | − |
| τ (2 ≤ τ < |ω|) | 2 | − | − | 2 | |
| |ω| | 11 | − | − | 18 | |
| t | − | − | 1 | − | |
| λ | 18 | − | 1 | 18 | |
| N | − | − | − | 200 | |
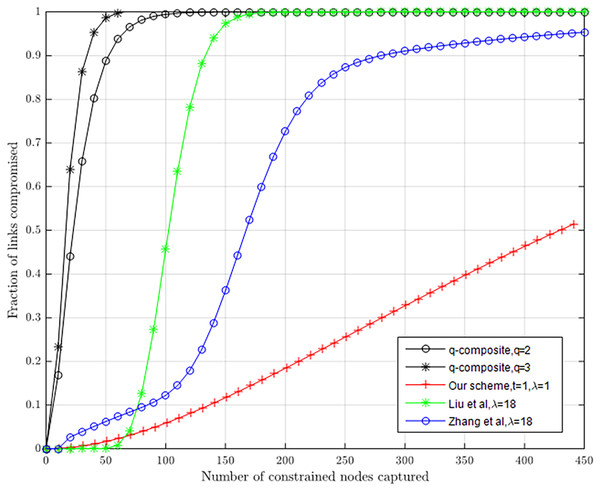
Our scheme offers better resilience to node capture attacks than q-composite, Liu, Ning & Li (2003) and Zhang, Li & Li (2018) in Fig. 6. If attackers capture 231 sensor nodes, about 22.8% of the pairwise keys, in our scheme with λ = 1 and t = 1, between non-compromised nodes will be compromised. If an attacker captures 401 nodes, about 46.5% of the pairwise keys between non-compromised nodes will be compromised. In Blundo et al. (1998), when captured nodes remain at 410, all pairwise keys between non-compromised nodes will be compromised. In Liu, Ning & Li (2003), when captured nodes remain at 500, all pairwise keys between non-compromised nodes will be compromised. In Zhang, Li & Li (2018), when captured nodes remain at 500, about 91.0% of pairwise keys between non-compromised nodes will be compromised. In q-composite (q = 2) and q-composite (q = 3), when captured nodes remain at 800, almost all pairwise keys between non-compromised nodes will be compromised.
Figure 6: Resilience to node capture attack.
Resilience to node capture in our scheme
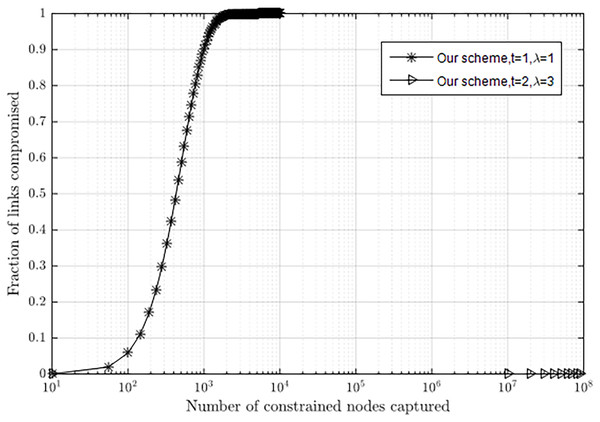
The relationship between λ and t can be described as in our scheme, i.e., λ and t affect the fraction of compromised links. Figure 7 shows the relationship between the fraction of compromised links for non-compromised sensors and the number of compromised nodes with different values of λ and t. If attackers capture 1,000 sensor nodes, about 90.2% of the pairwise keys between non-compromised nodes will be compromised when λ = 1 and t = 1. If attackers capture 1.0 × 108 sensor nodes, nearly no pairwise keys between non-compromised nodes will be compromised when λ = 3 and t = 2. Actually, with λ = 3 and t = 2, the sensor network can hold at least 1.0 × 108 nodes, which is enough to meet the requirements of many scenarios.
Figure 7: Resilience to node capture attack with different λ and t.
Connectivity rate
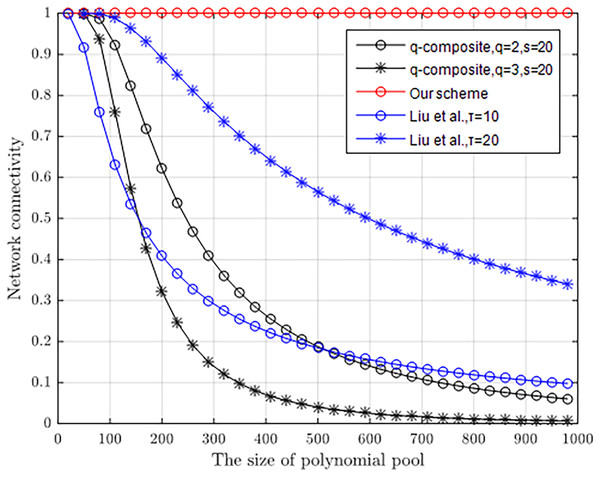
A higher connectivity rate of the node network can increase the communication efficiency of the node and reduce the loss of communication energy. Figure 8 compares the network connectivity of the proposed scheme with that of Liu, Ning & Li (2003) and q-composite (Chan, Perrig & Song, 2003). In the simulation, we assume that the q-composite preloaded s = 50 keys in each sensor, and τ = 10 and τ = 20 polynomials in Liu, Ning & Li (2003) are preloaded in each node. The result illustrates that the proposed scheme has 100% connectivity regardless of the size of polynomial pool.
Figure 8: Network connectivity with the different size of polynomial pool.
Table 3 in more detail shows that our scheme offers a better connectivity rate of nodes than the other three schemes, and inherits that every node in a sensor network is able to establish a connection in Blundo et al. (1998). When three polynomials are selected from one polynomial pool holding 25 polynomials, about 33.0% of nodes in Liu, Ning & Li (2003) are connected. However, when still remaining 34.6% of nodes are connected, Liu, Ning & Li (2003) should select two polynomials from a polynomial pool with 11 polynomials. In q-composite (q = 2) (Chan, Perrig & Song, 2003), when 20 keys are selected from one key pool holding 340 keys, about 33.2% of nodes are connected. However, when still remaining 32.0% of nodes are connected, the q-composite (q = 3) scheme (Chan, Perrig & Song, 2003) should scale down the key pool size to 200. When three polynomials are selected from one polynomial pool holding 18 polynomials, about 57.8% of nodes in Zhang, Li & Li (2018) are connected. However, when two polynomials are selected from the same polynomial pool, only about 31.8% of nodes in Zhang, Li & Li (2018) are connected.
| Scheme | Connectivity P |
|---|---|
| q-composite (Chan, Perrig & Song, 2003) (q = 2, s = 20, |S| = 340) | 0.332 |
| q-composite (Chan, Perrig & Song, 2003) (q = 3, s = 20, |S| = 200) | 0.320 |
| Blundo et al. (1998) (λ = 18) | 1 |
| Blundo et al. (1998) (λ = 19) | 1 |
| Li et al. (2020) (λ = 18, τ = 2, |ω| = 11) | 0.346 |
| Li et al. (2020) (λ = 18, τ = 3, |ω| = 25) | 0.330 |
| Zhang, Li & Li (2018) (λ = 18, τ = 2, s =12, |ω| = 18, N = 200) | 0.318 |
| Zhang, Li & Li (2018) (λ = 18, τ = 3, s = 23, |ω| = 18, N = 200) | 0.578 |
| Our scheme (t = 2, λ = 3) | 1 |
| Our scheme (t = 3, λ = 7) | 1 |
Resource overhead
We selected several classic key management solutions for comparative study from the aspects of communication, computation, and storage overhead. For convenience, we only consider the polynomial P(x,y) cost. The lk represents the length of key. we assume that each generated key takes the same storage as the coefficient of a λ-degree polynomial. lID is the length of a node or key identifier. We assume that the node and key identifiers have the same length. τ are the number of polynomials selected for each node in Liu, Ning & Li (2003) and Zhang, Li & Li (2018). s is the number of keys preloaded in each sensor.
We estimate the computation, communication, and storage energy consumed by constrained nodes during pairwise key establishment. Owing to selecting a set of polynomials from a polynomial pool, we use the same amount of polynomials for Liu, Ning & Li (2003) and Zhang, Li & Li (2018) per node. There are the same λ-degree for a polynomial for the four schemes. Table 4 lists the comparative study in resource overheads.
| Scheme | Storage overhead | Communication overhead |
Computational overhead |
|---|---|---|---|
| Blundo et al. (1998) | (λ+1)lk + lID | lID | λ+1 |
| Liu, Ning & Li (2003) | [τ(λ+1)]lk + (τ+1)lID | (τ+1)lID | λ+1 |
| Zhang, Li & Li (2018) | [s+τ(λ+1)]lk + (2s+τ+1)lID | (2s+τ+1)lID | λ+1 |
| Our scheme | (λ+1)2 lk + lID | lID | λ+1 |
Computational overhead
The key management schemes with polynomials rely on the existence of the same polynomial between two nodes. In other words, the polynomial has an important impact on the computation cost in nodes, when the pairwise key is established. To evaluate the computational cost, we mainly consider the number of calculations in polynomial. Table 5 lists the computational overhead of the comparative study, which shows that these four schemes have the same consumption in computation. In fact, although these schemes owe the same computational overhead, our scheme has better advantages in applying to some field environments compared with the other three schemes, with better resilience against node capture and lower storage overhead.
| Scheme | Blundo et al. (1998) | Liu, Ning & Li (2003) | Zhang, Li & Li (2018) | Our scheme |
|---|---|---|---|---|
| Computational overhead | λ+1 | λ+1 | λ+1 | λ+1 |
Communication overhead
The information exchange of wireless sensor networks relies on the emission of electromagnetic waves, which depletes much energy carried by nodes. In other words, energy cost in communication is significantly impacted by the length of communication message and the number of data packets. The longer the data length, the more energy in communication is consumed. These schemes mainly send the identities of the node, the identities of the secret key and the identities of the polynomial when the pairwise key is established. τ is the number of polynomials selected for each node. Table 6 lists the communication overhead of the comparative study, where .
| Scheme | Blundo et al. (1998) | Liu, Ning & Li (2003) | Zhang, Li & Li (2018) | Our scheme |
|---|---|---|---|---|
| Communication overhead | lID | (τ+1)lID | (2τ+1)lID | lID |
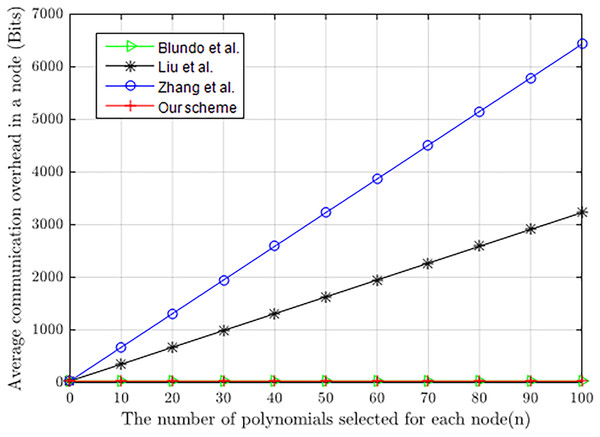
Note that both lk and lID are 32 bits. Figure 9 shows the comparison in communication consumption of our scheme with Blundo et al. (1998), Liu, Ning & Li (2003) and Zhang, Li & Li (2018), where the loss of energy in communication is represented by the length of information (bits). The figure clearly illustrates that the communication cost of our scheme is significantly lower than in Zhang, Li & Li (2018) and Liu, Ning & Li (2003), and equal to Blundo et al. (1998) during pairwise key establishment. As we know, our scheme, similar to Blundo et al. (1998), only needs nodes to pass their own identities to each other, which improves communication efficiency and reduces the energy consumption of nodes in communication.
Figure 9: Communication energy consumed by constrained nodes.
Storage overhead
Sensor nodes are highly constrained in terms of memory resources. When designing a key management scheme, we should reduce the memory overhead of nodes as much as possible. The storage overhead this scheme depends on the cost of the nodes’ dentities, the coefficients of the λ-degree polynomials and the dentities of polynomials, where lk = log2 q. Table 7 lists the storage overhead of the comparative study, in which τ = 50, s = 25.
| Scheme | Blundo et al. (1998) | Liu, Ning & Li (2003) | Zhang, Li & Li (2018) | Our scheme |
|---|---|---|---|---|
| Storage overhead | (λ+1)lk +lID | 50(λ+1)lk+51lID | [25+50(λ+1)]lk+101lID | (λ+1)2 lk +lID |
Note:
s = 25
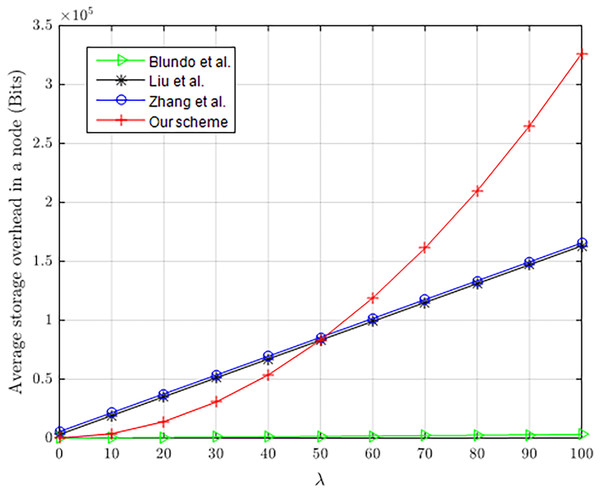
Assume that both lk and lID are 32 bits. Figure 10 shows the comparison in memory consumption (bits) of our scheme with Blundo et al. (1998), Liu, Ning & Li (2003) and Zhang, Li & Li (2018), which clearly shows the advantage of our scheme to some extent. As the λ no more than 50, the storage cost in our scheme is much smaller than in Zhang, Li & Li (2018) and Liu, Ning & Li (2003) during pairwise key establishment. The storage overhead in our scheme remains stable, not changing with the number of nodes. In fact, with a small λ, our scheme can still hold a large number of nodes and maintain better resilience to node capture. Our scheme, when λ = 3, can hold 5.53 × 1019 nodes in a network. However, Liu, Ning & Li (2003) (λ = 18, τ = 3, |ω| = 25) is only able to hold 158 nodes in a network. When 1.0 × 108 nodes are captured in a network, the capture rate of communication links in non-compromised nodes is still nearly close to 0. Therefore, our scheme has greater advantages in applying to large-scale networks, not only with lower storage overhead but also resilience to node capture attacks.
Figure 10: Average memory consumption of constrained nodes.
Conclusions
We proposed a key management scheme with a dynamic coefficient symmetric polynomial. The scheme allows every pair of communicating nodes to use their own IDs to map into the elements of the shared matrix M and assigns these elements to polynomial to establish pairwise keys. Different from other schemes, ours deterministically configures a different polynomial for each pair of communicating nodes by an identity mapping algorithm. This enables a high connectivity rate and solves the λ-secure problem of key management, when no hash collision occurs. Security analysis shows that the proposed scheme has stronger resilience to node capture from various types of attacks. It consumes less energy in storage and communication than other protocols.