Joint user grouping and power control using whale optimization algorithm for NOMA uplink systems
- Published
- Accepted
- Received
- Academic Editor
- Ayaz Ahmad
- Subject Areas
- Artificial Intelligence, Computer Networks and Communications
- Keywords
- Whale optimization algorithm, Grey wolf optimization, Particle swarm optimization, Wireless communication, Uplink, NOMA, 5G
- Copyright
- © 2022 Rehman et al.
- Licence
- This is an open access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, reproduction and adaptation in any medium and for any purpose provided that it is properly attributed. For attribution, the original author(s), title, publication source (PeerJ Computer Science) and either DOI or URL of the article must be cited.
- Cite this article
- 2022. Joint user grouping and power control using whale optimization algorithm for NOMA uplink systems. PeerJ Computer Science 8:e882 https://doi.org/10.7717/peerj-cs.882
Abstract
The non-orthogonal multiple access (NOMA) scheme has proven to be a potential candidate to enhance spectral potency and massive connectivity for 5G wireless networks. To achieve effective system performance, user grouping, power control, and decoding order are considered to be fundamental factors. In this regard, a joint combinatorial problem consisting of user grouping and power control is considered, to obtain high spectral-efficiency for NOMA uplink system with lower computational complexity. To solve the joint problem of power control and user grouping, for Uplink NOMA, we have used a newly developed meta-heuristicnature-inspired optimization algorithm i.e., whale optimization algorithm (WOA), for the first time. Furthermore, for comparison, a recently initiated grey wolf optimizer (GWO) and the well-known particle swarm optimization (PSO) algorithms were applied for the same joint issue. To attain optimal and sub-optimal solutions, a NOMA-based model was used to evaluate the potential of the proposed algorithm. Numerical results validate that proposed WOA outperforms GWO, PSO and existing literature reported for NOMA uplink systems in-terms of spectral performance. In addition, WOA attains improved results in terms of joint user grouping and power control with lower system-complexity when compared to GWO and PSO algorithms. The proposed work is a novel enhancement for 5G uplink applications of NOMA systems.
Introduction
Multiple access approaches are increasingly gaining importance in modern mobile communication systems, primarily due to the overwhelming increase in the communication demands at both the user and device level. Over past few years, non-orthogonal multiple access (NOMA) (Ding et al., 2017a; Ding et al., 2014; Ding et al., 2017b; Benjebbovu et al., 2013) schemes have earned significant attention for supporting the huge connectivity in contemporary wireless communication systems. The NOMA schemes are currently considered to be the most promising contender for the 5G and beyond 5G (B5G) wireless communications, which are capable of accessing massive user connections and attaining high spectrum performance. Moreover, a report has been published recently regarding the Third Generation Partnership Project for determining the effectiveness of NOMA schemes for several applications or development scenarios, particularly for ultra-reliable low latency communications (URLLC), enhanced mobile broadband (eMBB), and massive machine type communications (mMTC) (Benjebbour et al., 2013). Contrary to the classic orthogonal multiple access (OMA) approaches, the NOMA schemes can offer services to multiple users in the same space/code/frequency/time resource block (RB). The NOMA schemes are also capable of differentiating the users that have distinct channel settings. These schemes are mainly inclined at strengthening connectivity and facilitating users with an efficient broad-spectrum (Islam et al., 2016; Dai et al., 2015).
Some recent studies (Chen, Wang & Zhang, 2018; Wang et al., 2019; Shahini & Ansari, 2019) have discussed the effective use of the NOMA approach in standard frameworks for Internet of Things (IoT) systems and Vehicle-to-Everything (V2X) networks. The successive interference cancellation (SIC) technique, which is pertinent for multi-user detection and decoding is implemented for the NOMA scheme at the receiver end. The SIC technique operates differently for the downlink and uplink scenarios. In the downlink NOMA scenario, SIC is applied at the receiver end, where high energy is consumed during processing when a lot of users are considered in the NOMA group. For that reason, two users are typically considered in a group for optimum grouping/pairing of users in the case of the downlink NOMA system (Al-Abbasi & So, 2016; He, Tang & Che, 2016). Whereas in the uplink NOMA systems, it is possible to employ SIC at the base station (BS) that has a higher processing capacity. Moreover, in uplink NOMA, multiple users are allowed to transmit in a grant-free approach that leads to a significantly reduced latency rate.
From a practical perspective, the user-pairing/grouping and power control schemes in uplink/downlink NOMA systems are critically required to achieve an appropriate trade-off between the performance of the NOMA system and the computational complexity of the SIC technique. Over the past few years, several studies have discussed different prospects regarding the maximization of sum rate (Zhang et al., 2016a; Ding, Fan & Poor, 2015; Ali, Tabassum & Hossain, 2016), the transmission power control approaches (Wei et al., 2017), and fairness (Liu, Mähönen & Petrova, 2015; Liu et al., 2016) for user pairing/grouping NOMA systems. Regarding the maximization of sum rate, a two-user grouping scheme based on a unique channel gain is demonstrated in Ding, Fan & Poor (2015) whereas another study (Ali, Tabassum & Hossain, 2016) presented a novel framework for pertinent user-pairing/grouping approaches to assign the same resource block to multiple users.
In reference to the user pairing schemes (Sedaghat & Müller, 2018) used the Hungarian algorithm with a modified cost function to investigate optimum allocation for three distinct cases in the uplink NOMA system. Furthermore, several matching game-based (Liang et al., 2017) user-pairing/grouping approaches are discussed in Xu et al. (2017) and Di, Song & Li (2016), wherein the allocation of users and two sets of players are modeled as a game theory problem. Numerous recent studies (Zhai et al., 2019; Zhu et al., 2018; Nguyen & Le, 2019) have also investigated different user-pairing/grouping schemes for NOMA systems. A novel algorithm named Ford Fulkerson (Zhai et al., 2019) has been introduced for D2D cellular communication to address the user-pairing issue in NOMA systems. In addition to that, optimal user paring is achieved in Zhu et al. (2018) by taking two users with appropriate analytical conditions into consideration. A new framework (Song et al., 2014) is also presented for optimum cooperative communication networks. Besides that, a lookup table (Azam, Shahab & Shin, 2019) is introduced by performing comprehensive calculations to highlight the significance of power allocation and uplink user pairing in obtaining high sum-rate capacity while fulfilling the demands of user data rates. For the uplink case, a cumulative distributive function (CDF)-based resource allocation scheme (Zhanyang, Toor & Jin, 2018) is presented where for each time slot, the selection of two users is dependent on the highest value of the CDF. Moreover, a few dynamic power allocation and power back-off schemes are also discussed in few studies (Zhang et al., 2016b; Yang et al., 2016) for scrutinizing the performance of the system to obtain high sum rates and meet the service quality requirements.
In the context of overlapping, a generic user grouping approach (Chen et al., 2020a) is presented for NOMA, which involves the grouping of many users with a limitation on maximum power. The authors also formulated a problem for generalized user grouping and power control to achieve an optimized user grouping scheme based on the machine learning approach. Furthermore, another study (Chen et al., 2020b) proposed a framework in which an overlapping coalition formation (OCF) game is used for overlapping user grouping and an OCF-based algorithm is also introduced that facilitated the self-organization of each user in an appropriate overlapping coalition model. Besides that, a joint problem is examined in Guo et al. (2019) for user grouping, association, and power allocation in consideration of QoS requirements for enhancing the uplink network capacity. Zhang et al. (2019) also discussed a joint combinatorial problem for obtaining a sub-optimal and universal solution for user-pairing/grouping to boost the overall system performance. Additionally, the authors in Wang et al. (2018) considered a user association problem by using an orthogonal approach for grouping users and employing a game-theoretic scheme for the allocation of a resource block to multi-users in a network. It has been observed that there are certain limitations associated with the game-theoretic schemes that are typically employed in user association techniques. However, the evolutionary algorithms (EAs) are universal optimizers that exhibit exceptional performance irrespective of the optimization problems being studied. The problem formulation is done as a sum rate utility function for the network and a parameter is presented that depicts the intricacy for power control problems. Therefore, the parameters for power control remain constant for all the systems. Moreover, NOMA-based mobile edge computing (MEC) system (Zheng, Xu & Tang, 2020) has been investigated to improve the energy efficiency during task offloading process. Further, a matching coalition scheme has been used to address the issue of power control and resource allocation. In addition, a matching theory (Panda, 2020) approach is proposed to enhance the operational system’s user patterns and resource management.
Meta-heuristics are high-level processes that combine basic heuristics and procedures in order to provide excellent approximation solutions to computationally complex combinatorial optimization problems in telecommunications (Martins & Ribeiro, 2006) . Furthermore, the key ideas connected with various meta-heuristics and provide templates for simple implementations. In addition, several effective meta-heuristic approaches to optimization problems have been investigated in telecommunications.
Several meta-heuristic algorithms (Sharma & Gupta, 2020) have been proposed to address localization problems in sensor networks. Some of the meta-heuristic algorithms used to solve the localization problems include the bat algorithm, firework algorithm and cuckoo search algorithm. For wireless sensors networks (Wang, Li & Pedrycz, 2020), routing algorithm has been developed based on elite hybrid meta-heuristic optimization algorithm.
On the other hand, swarm intelligence (SI) algorithms, in addition to game theory and convex optimization, has recently emerged as a promising optimization method for wireless-communication. The use of SI algorithms can resolve arising issues in wireless networks such as power control problem, spectrum allocation and network security problems (Pham et al., 2020b). Furthermore, two SI algorithms, named grey wolf optimizer (GWO) and particle swarm optimizer (PSO) are also used in literature for solving the joint problem regarding user associations and power control in NOMA downlink systems to attain maximized sum-rate (Goudos et al., 2020). Additionally, an efficient meta-heuristic approach known as multi-trial vector-based differential evolution (MTDE) (Nadimi-Shahraki et al., 2020) has been implemented for solving different complex engineering problems by using multi trial vector technique (MTV) which integrates several search algorithms in the form of trial vector producers (TVPs) approach. Recently, an updated version of GWO i.e., Improved-grey wolf optimizer (I-GWO) (Nadimi-Shahraki, Taghian & Mirjalili, 2021) has been investigated for handling global optimization and engineering design challenges. This modification is intended to address the shortage of population variety, the mismatch between exploitation and exploration, and the GWO algorithm’s premature convergence. The I-GWO algorithm derives from a novel mobility approach known as dimension learning-based hunting (DLH) search strategy which was derived from the natural hunting behaviour of wolves. DLH takes a unique method to creating a neighbourhood for each wolf in which nearby information may be exchanged among wolves. This dimension learning when employed in the DLH search technique improves the imbalance between local and global search and preserves variation. A parallel variant of the Cuckoo Search method is the Island-based Cuckoo Search (IBCS) (Alawad & Abed-alguni, 2021) using extremely disruptive polynomial mutation (iCSPM). The discrete iCSPM with opposition-based learning approach (DiCSPM) is a version of iCSPM has been proposed to schedule processes in cloud computing systems focusing on data communication expenses and computations. Moreover, for scheduling dependent tasks to virtual machines (VMs), this work offers a discrete variant of the Distributed Grey Wolf Optimizer (DGWO) (Abed-alguni & Alawad, 2021). In DGWO, the scheduling process is considered as a problem of minimization for data communication expenses and computation.
In this paper, a joint combinatorial problem of user pairing/grouping, power control, and decoding order are considered for every uplink NOMA user within the network. To solve this problem, we propose a recently introduced meta-heuristic algorithm known as whale optimization algorithm (WOA) (Mirjalili & Lewis, 2016) that is inspired by the hunting approach of the humpback whale. Furthermore, a grey wolf optimizer (GWO) (Mirjalili, Mirjalili & Lewis, 2014) and particle swarm optimization (PSO) (Kennedy & Eberhart, 1995) algorithms are also employed in this research study. The results obtained through the algorithms proposed in Sedaghat & Müller (2018), WOA, GWO and the popular PSO are exclusively compared in this study. The acquired results indicate that the WOA outperformed the existing algorithm (Sedaghat & Müller, 2018), GWO and PSO in- terms of spectral-efficiency with lower computational complexity.
The rest of the paper is structured as follows: the ‘System Model and Problem Formulation’ describes the mathematical representation and research problem of NOMA uplink system. The solution is provided in the ‘Solution of Proposed Problem’ section where an efficient decoding order, power control scheme and user grouping approach are employed for NOMA uplink System. A concise analysis on the simulation is provided in ‘Simulation Results’ section. The ‘Conclusion’ section presents the summary of this research work.
System Model and Problem Formulation
System model
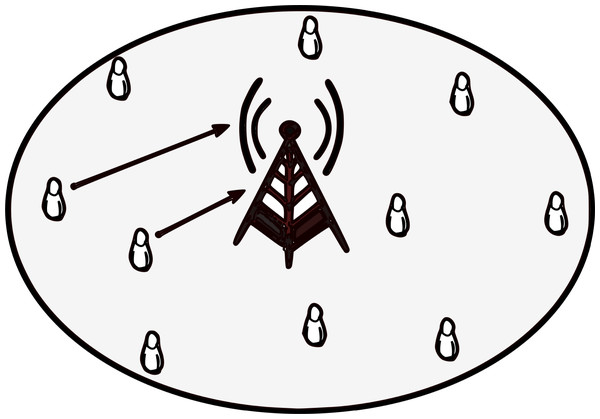
As illustrated in Fig. 1, we consider an uplink NOMA transmission with a single-cell denoted by C. The number of users M served by a single base station (BS) placed at the centre of the cell. To obtain the signal/information requirements of several users, the number of physical resource block (PRB) denoted by N are assigned to multiple-users in a cell.
Figure 1: NOMA uplink transmission.
For uplink transmission, users in almost in same PRB/group maintaining same PRB execute NOMA operation while users belong to different PRB/group assigned different PRB execute OMA operation. Hence, the received signal zn at the BS can be represented as: (1)
where υn,m ∈ {0, 1} is the user n indicator assigned to the n − th group. The transmission path between user m and BS is represented by gm which is Guassian distributed. The power control coefficients is denoted by αm(0 ≤ αm ≤ 1). For each user m, the transmission power and the signal is denoted by P and sm, where 𝔼(|sm|2 = 1). The additive white Gaussian noise (AWGN) power is denoted by ωn with an average power σ2. Therefore, the maximum spectral efficiency of user M and the received signal to interference plus noise ratio (SINR) on n − th PRB can be expressed as: (2) (3)
The SIC operation is carried out at the BS for each PRB/group to decode the users signal. The decoding order of a user n is represented by δn,m in a cell, where δn,m = a > 0 assumes that any user m in a group is the i − th one in the n − th PRB is to be decoded. Thus, the maximum spectral efficiency of user n can be represented as: (4)
where δn,j > δn,m represents the decoding order of users in a PRB/group. If users m and j are in the same group, then it implies that user m is decoded first. The transmission power to noise ratio is represented by γ, where γ = P/σ2. Assuming that, channel-state-information (CSI) is known by BS of each user within coverage area.
To attain effective user-pairing/grouping and power control for NOMA uplink system, each user M in a cell transmit their power control coefficient αm along with user indicator υn,m. Hence, the maximum spectral-efficiency in the n − th PRB/group can be expressed as follows: (5) (6)
Eq. (6) clearly shows that the spectral efficiency in each group has not been affected by the order of decoding but has an impact on each user.
Problem formulation
In this paper, we propose an efficient method for power-control, decoding order and user-pairing/grouping to increase the spectral-efficiency under their required minimum rate constraint. Therefore, a joint combinatorial problem of power control, decoding order and user pairing/grouping is formulated to maximize the spectral-efficiency. The minimum spectral-requirement of each user in the network is sm. Therefore, the spectral efficiency maximization problem (Sedaghat & Müller, 2018; Zhang et al., 2019) can be formulated as: (7a) (7b) (7c) (7d) (7e)
where δn,m represents the decoding order and π indicates all possible combinations of users decoding orders in a network. C1 indicates the upper bound of transmission power. C2 guarantees the minimum rate of a user. C3 and C4 ensures the user indicator and m users assigned to PRB/group.
Solution of Proposed Problem
To achieve the global optimal solution for problem (Eq. (7a)), the optimization variables υn,m, δn,m, and αm are strongly correlated, which makes the problem complex. In connection of the fact that user-pairing variables δn,m are combinatorial integer programming variables. Hence, first solve the combinatorial problem of power control and decoding order instead and compute the optimum user-pairing/grouping solution. In case of any fixed scheme of user-grouping, the value of υn,m are independent among all distinct group regarding both decoding order and power control. (8a) (8b) (8c)
where indicates set of all possible combination in the n − th PRB.
Optimal decoding for optimal user-pairing/grouping
In order to apply the SIC operation, all users signals/information are decoded by the receiver in the descending order based on channel condition. In the uplink NOMA system (Ali, Tabassum & Hossain, 2016), the users with better channel condition is decoded first at the BS while the user with worse channel conditions is decode last. As a result, the user with better channel condition experiences interference from all the users in the network, while the users with poor channel condition experiences interference free transmission.
To attain an efficient decoding (Zhang et al., 2019) for NOMA uplink users, the decoding order for M users in a cell concern to same group/PRB, based upon the value of Jn, where different decoding order of each user in a network depend on power control (Zhang et al., 2019) scheme regarding different feasible region can be represented as: (9)
where (10)
Based on Eq. (9), the user with higher value of Jm in a cell is decoded first. Also applies that the decoding-order does not affect the spectral efficiency of each PRB/group.
Power control
The nature of the problem in Eq. (8a) is a mixed integer non-linear programming (MINLP). Hence, we have achieved the optimal solution for decoding order δn,m. Therefore, it is required to find all the possible group of combination for user pairing/grouping.
For this purpose, k users in a single cell C are considered. Without loss of generality, it is needful to reduce the complexity and simplify the mathematical procedure regarding optimal decoding order δn,m. The users are listed in a C based on the decreasing order Jm, for example 1, 2, 3, …, K. Therefore, Eq. (8a) can be represented as: (11a) (11b) (11c)
where {αk} represents power control-variables. Equations (11a) and (11b) show linearity and translated to SNR formulations respectively.
As shown in Eq. (11a), αk is increasing. Therefore, the optimal solution for power control will always be upper bound. To determine the lower bound of power control (Zhang et al., 2019), the following equation can be solved as: (12)
where (13)
which signifies that the spectral efficiency requirements is equal to the sum of spectral efficiencies of all the users. If , exceeds the limit of upper bound and hence, no feasible solution for Eq. (11a). If , Eq. (11a) has the feasible solution due to bound of αk variables. Therefore, for all users M in a cell, the optimal solution (Zhang et al., 2019) of the αk variables can be illustrated as (14)
where (15)
In reference to Eqs. (14) and (15), the optimal power control variables mentioned in problem Eq. (11a) is achieved. Specifically, if , for other users, the optimal power control variables are for j > k.
User grouping
An efficient and low computational time algorithm for user-pairing/grouping is one of the key concern for an effective NOMA uplink system. In this regard, three different meta-heuristic algorithms are proposed to solve the issue of complexity. The WOA is investigated for an efficient optimal and sub-optimal solution for user-pairing/grouping problem as a result to enhance the system performance. Further, the user pairing/grouping problem that exploits the channel-gain difference among different users in a network and the objective is to raise system’s spectral-efficiency. To determine the optimum user-pairing/grouping, a specific approach of solving user pairing/grouping problem is by using the search approach. For fixed user-pairing/grouping scheme, the optimal solution is obtained (Zhang et al., 2019). Then, list all the users in the decreasing order of Jm accordingly. The proposed algorithm for user pairing/grouping problem is illustrated in Algorithm 1. Initially, define the feasible solution of user grouping for exhaustive and swarm based algorithm. An exhaustive search explores each data points within the search region and therefore provides the best available match. Furthermore, a huge proportion of computation is needed. Particularly a discrete type problem where no such solution exists to find the effective feasible solution. There may be a need to verify each and every possibility sequentially for the purpose of determining the best feasible solution. The optimal solution using exhaustive search algorithm (Zhang et al., 2019) is getting obdurate because the number of comparison increases rapidly. Hence, the system complexity of WOA for user grouping scheme is O(MN), where as O(NM) represent the complexity of the exhaustive search algorithm. Therefore, a WOA approach is employed to reduce the complexity and provide efficient results. In addition, GWO and PSO algorithms are also proposed for the same problem.
Whale optimization algorithm (WOA)
To enhance the spectral-throughput and reduce the system complexity, an innovative existence meta-heuristic optimization technique named whale optimization algorithm (WOA) (Mirjalili & Lewis, 2016) is proposed in this paper. The algorithm WOA is resembles to the behaviour of the humpback whales, which is based on the bubble-net searching approach. Three distinct approaches are used to model the WOA is described as
Encircling prey
In this approach, the humpback-whales can locate the prey-location of the prey and en-circle that region. Considering that, the location of the optimal design in the search region is not known in the beginning. Hence, the algorithm WOA provides the best solution that is nearer to the optimal value. First determine the best solution regarding location and then change the position according to the current condition of the other search agents concerning to determine the best solution. Such an approach is described mathematically and can be expressed as: (16) (17) (18)
where, and represents the coefficients-vectors, t defines the initial iteration and X∗ and both describes the position- vector where X∗ includes the best solution so far acquired. || and . defines the absolute and multiplication. Noted that the position vector X∗ is updated for each iteration until to find the best solution. The coefficients vector vectors and can be determined as: (19) (20)
where indicates random vector 0 ≤ r ≤ 1 and represent a vector with a value between 2 and 0, which is decreasing linearly during the iteration.
Spiral bubble-net feeding maneuver
Two techniques are proposed to predict accurately the bubble-net activity of humpback-whales.
1. Shrinking en-circling
This type of techniques is achieved by decreasing the value of using Eq. (19). It is to be noted that the variation range of is also reduced by the value . Therefore, is a random value from [ − b, b], where the value of b is decreasing from 2 to 0 during the iterations.
2. Spiral updating position
In spiral method, a relationship between the location of prey and whale to impersonate the helix-shaped operations is represented in the form of mathematical equation of humpback-whales in the following manner: (21)
where , which represents the distance between prey and the i − th whale. l denotes the random number (−1 ≤ l ≤ 1).b represents logarithmic spiral, which is a constant number and . indicates the multiplication operation. It’s worth noting that humpback-whales swim in a shrinking-circle around their prey while still following a spiral-shaped direction. To predict this concurrent action, an equation is derived to represent the model can be expressed as: (22)
where d represents a random number (0 ≤ d ≤ 1). Further, the searching behaviour of humpback-whales for prey is randomly in the bubble-net approach. The following is the representation of mathematical model for bubble net approach.
Prey searching technique
To locate prey, same strategy based on the modification of the vector can be utilized (exploration). In reality, humpback-whales search at random based on their location. As a result, we select randomly with values or to compel the search-agent to step away from a target value. Comparison with exploitation, modify the location of every search- agent in the sample space, based on randomly selected process until to obtained a better solution. This operation and place an emphasis on the exploration phase and enable WOA to perform global-searching. This can be represented below: (23) (24)
where indicates a position-vector that is randomly selected from the existing space.
The algorithm WOA comprised of a selection of random samples. For every iteration, the search agents change their locations in relation to either a randomly selected search agent or the best solution acquired so far in this. For both cases exploitation phase and exploration the value of b is decreasing in the range from 2 to 0 accordingly. As the value of , a randomly searching solution is selected, while the optimal solution is obtained when for updating the search- location of the agents. Based on the parameter d, the WOA is used as a circular or spiral behaviour. Ultimately, the WOA is ended by the successful termination condition is met. Theoretically, it provides exploration and exploitation capability. Therefore, WOA can still be considered as a successful global optimizer. The WOA is described in Algorithm 1.
Data: Set the input control variables
M,N,γm,{gm},{sn}
Population initialization X1,X2,.........Xn
Result: X∗ (Best search agent for user- pairing/grouping).
List all the users with decreasing order of Jm.
while t < (total iterations)
for every search user
Initialize b,B,A,q and d
if1(d < 0.5)
if2(|B| < 1)
Existing search user position is updated using equation (16)
else if2(|B|≥ 1)
Randomly selected a search user (Xrand)
Existing position of search user is updated using equation (23)
end if2
else if1(d ≥ 0.5)
Exiting position of search user is updated using equation (21)
end if1
end for
Examine the position of every search user in the search region if above the search
region then modify it.
Determine the position of every search user
If a best solution becomes available, update X*
t=t+1
end while
return X∗
Algorithm 1: WOA Grey wolf optimizer (GWO)
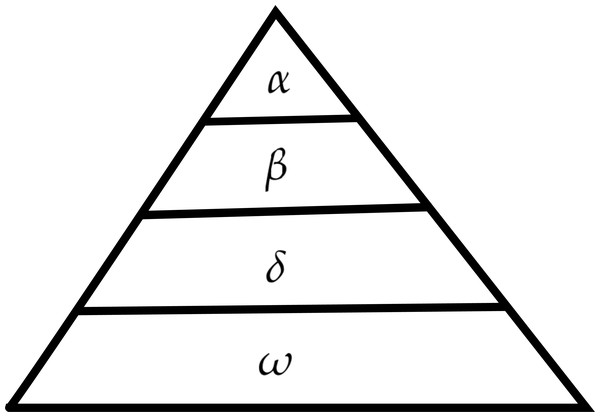
A popular meta-heuristic algorithm, which is influenced by the behaviour of grey-wolves (Mirjalili, Mirjalili & Lewis, 2014). This algorithm is based on the hunting approach of grey wolves and their governing- hierarchy. Grey wolves represent predatory animals, which means these are heading up in the hierarchy. Grey wolves tended to stay in groups. The wolves in a group is varying between 5 to 12. The governing-hierarchy of GWO is shown in Fig. 2, where several kinds of grey wolves have been used particularly α, β, δ, and ω.
Figure 2: Grey wolf hierarchy (Mirjalili, Mirjalili & Lewis, 2014).
Both wolves (male and female) are the founders known as αs. The α is mainly in favour of producing decision making regarding hunting, sleeping and waking time, sleeping place etc. The group is governed by the αs actions. Even so, some egalitarian behaviour has been observed, such as an alpha wolf following other wolves in the group. The whole group respects the α by keeping their tails towards ground at gatherings. The α wolf is also regarded as superior since the group must obey his/her orders. The group’s α wolves are the only ones that can mate. Usually, the α is not always the biggest member of the group, but rather the best at handling the batch. Which illustrates that a group’s structure and discipline are often more critical than its capacity. β is the second phase of the grey wolf hierarchy. The β’s are the sub-ordinate wolves who assist the α in taking decision. The β wolf (male or female), is most likely the better choice to be the α wolf in the event that one of the α wolves dies or gets very old. Therefore, β wolf would honour the α while still commanding all other lower-level wolves. It serves as an adviser to the α and a group disciplinarian. Throughout the group, the β confirms the αs orders and provides guidance to the α. The grey wolf with the lowest rating is ω. The ω serves as a scapegoat. ω wolves must still respond towards other dominant wolves in a group. They are the last wolves permitted to feed. While it might seem that the ω is not a vital member of the group, it has been found that when the ω is lost, the entire group experiences internal combat and problems. This would be attributed to the ω venting his anger and resentment on both wolves (s). This tends to please the whole group while still preserving the dominance system. In certain circumstances, the ω is also the group’s babysitter. Whenever a wolf should not be an α, β, or ω, he or she is referred to as a subordinate also called δ. where δ wolves must yield to αs and βs, however they rule the ω. This group contains scouts, sentinels, elders, hunters, and caregivers. Scouts are in charge of patrolling the area and alerting the group if there is any threat. Sentinels defend and ensure the group’s safety. Furthermore, the mathematical model of GWO is described as:
Social hierarchy
For mathematical representation of GWO, we assume that α is fittest alternative solution used to mimic the social hierarchy. As a result, the second and third best solutions are designated as β and δ, respectively. The remaining member approaches are now considered to be ω. For algorithm, the hunting (optimization) is led by α, β and δ. These three wolves are accompanied by the ω.
Encircling prey
Grey wolves encircle prey during the hunting. The following equations are presented to mathematical model the encircling actions. (25) (26) (27)
where and represents coefficient vectors, t is the exiting iteration, and defines the position vector of a grey wolf and prey.
The vectors and are computed in the following manner: (28) (29)
where 0 ≤ d1 ≤ 1 and 0 ≤ d2 ≤ 1 indicates random vector and component decreasing linearly over the entire iteration from 2 to 0.
Hunting
Grey wolves do have capability to detect and encircle prey. The α normally leads the chase. The β and δ can also engage in hunting. However, in an arbitrary search space, we have no idea that where is the optimal (prey) location. Hence, first acquired the three best solutions so far and then search other agents (containing ω’s) in accordance with the best search agent’s location. In this respect, the following equations are provided. (30) (31) (32) (33) (34) (35) (36)
Attacking prey
The wolves complete the chase by hitting the target once it cease running. The mathematical model of attacking prey approach can be achieve by decreasing the value of . It’s worth mentioning that the variance range of is also limited by .
That is in the range of [ − b, b], which is a random value and decreasing over the entire iteration from 2 to 0. If any random values ranges between [ − 1, 1], then new location of a search-agent lies between exiting and prey location.
Search for prey
Grey wolves primarily hunt depending on the locations of the α, β, and δ. At the starting they diverge from other wolves to hunt and then combine to hit prey. The mathematical model of divergence can be achieved by utilizing the value of . For divergence, random values of or is used by the search agent. This process enables the GWO algorithm to search globally. In nature, the D vector can even be assumed as the impact of barriers to pursuing prey. In general, natural barriers arise in wolves’ hunting paths and discourage them from approaching prey effectively and easily. This is precisely depend on the vector D. It will arbitrarily give the prey a weight to find it tougher and farther to catch for wolves, depending on location of the wolf, or likewise.
The suggested social hierarchy supports GWO algorithm in sustaining the best solutions achieved so far through iteration. By using hunting approach, it enables agents to search the likely location of prey. The GWO is described in Algorithm 2.
Data: Set the input control variables
M,N,γm,{gm},{sn}
Population initialization X1,X2,.........Xn
Initialization of B,b and D
Result: Xα (Best search agent for user- pairing/grouping).
List all the users with decreasing order of Jm.
Determine fitness of every search agent
Xα,Xβ and Xδ.
while t < (total iterations)
for every search user
Update the existing location of search agent by using equation (36)
Update B, b and D
Determine fitness of search agent
UpdateXα, Xβand Xδ
t=t+1
end for
end while
return Xα
Algorithm 2: GWO Particle swarm optimization (PSO)
Kennedy & Eberhart (1995) introduced PSO as an evolutionary computation method. It was influenced by the social behaviour of birds, which involves a large number of individuals (particles) moving through the search space to try to find a solution. Over the entire iterations, the particles map the best solution (best location) in their tracks. In essence, particles are guided by their own best positions, which is the best solution same as achieved by the swarm. This behaviour can modelled mathematically by using velocity vector (u), dimension (S), which represents the number of parameters and position vector (x). In the entire iterations, the position and velocity of the particles changing by the following equation: (37) (38)
where v(0.4 ≤ v ≤ 0.9) represents the inertial weight, which control stability of the PSO algorithm. cognitive coefficient e1(0 < e1 ≤ 2), which limits the impact of the individual memory for best solution. Social factor e2(0 < e2 ≤ 2), which limits the motion of particles to find best solution by the entire swarm, rand indicates a random number in the range between 0 and 1, attempt to provide additional randomized search capability to the PSO algorithm and two variables pbest and gbest, used to accumulate best solutions achieved by each particle and the entire swarm accordingly. The PSO is described in Algorithm 3.
Data: Set the input control variables
M,N,γm,{gm},{sn}
Population initialization X1,X2,.........Xn
Result: pbest and gbest (Best search agent for user- pairing/grouping).
List all the users with decreasing order of Jm.
for each generation do
for each particle do
Update the position and vector by using equation (37) and equation (38)
Estimate the fitness of the particle
Update both pbest and gbest
t=t+1
end for
end for
return pbest, gbest
Algorithm 3: PSO Simulation Results
This section evaluates the performance of the proposed meta-heuristic algorithms, namely, WOA, GWO and PSO for joint problem of user-grouping, power control and decoding order for NOMA uplink systems.
Table 1 presents the simulation parameter values attained from the literature (Sedaghat & Müller, 2018; Zhang et al., 2019; Mirjalili & Lewis, 2016; Mirjalili, Mirjalili & Lewis, 2014; Kennedy & Eberhart, 1995) for WOA, GWO and PSO algorithms that involved in the simulation. Further, the Wilcoxon test and Friedman test (Abualigah et al. (2921)) are performed for experiments and the statistical analysis of GWO and PSO is also provided in Table 2. Based on the results of tests, the proposed WOA outperforms the other algorithms in comparison.
| Parameter | Value |
|---|---|
| C | 1 |
| M | 6 |
| N | 3 |
| sm | 1.1 bits/s/Hz |
| γ | 30 dB |
| Wilcoxon | GWO | PSO |
|---|---|---|
| p-value | 1.8E − 169 | 4.7E − 181 |
| Friedman | GWO | PSO |
|---|---|---|
| p-value | 4.5E − 161 | 1.2E − 164 |
Both channel of the users and location are allocated randomly in the simulation. Therefore, the range between the user and BS are uniformly distributed and considered that the channel response is Gaussian distribution (Zhang et al., 2019).
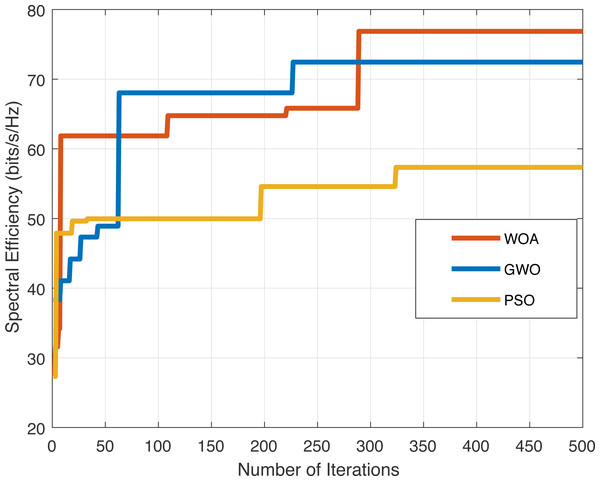
Figure 3 indicates the comparison of convergence of WOA (Mirjalili & Lewis, 2016) , GWO (Mirjalili, Mirjalili & Lewis, 2014) and PSO (Kennedy & Eberhart, 1995) algorithms proposed for NOMA uplink system. We may conclude that WOA, GWO and PSO algorithms converge at a comparable rate, hence WOA converges after a greater number of iterations than GWO and PSO. The proposed WOA attains significant performance in-terms of spectral efficiency as compare to GWO and PSO algorithms. The proposed WOA (Mirjalili & Lewis, 2016) provides stability and attains the minimum rate requirement without such a noticeable drop in the results.
Figure 3: Illustration of convergence of WOA, GWO and PSO.
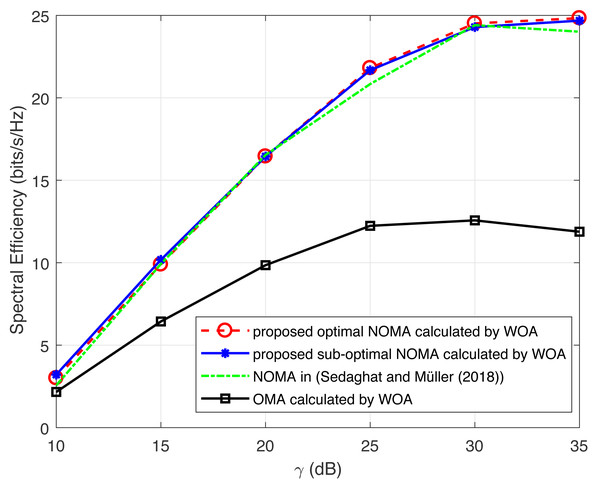
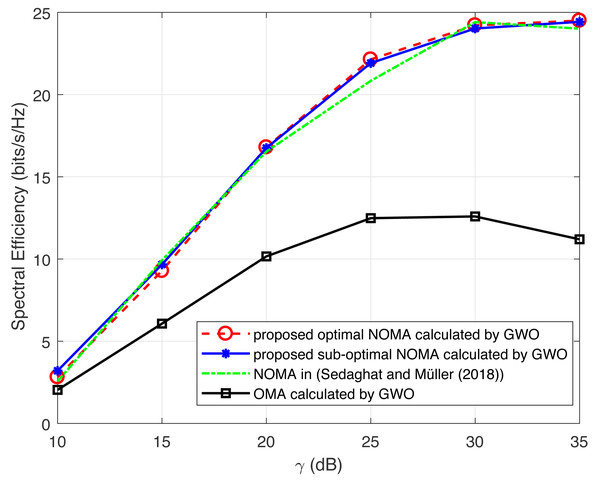
Figure 4 compares the spectral-efficiency of NOMA and OMA approaches with varying γ, respectively. It has been proved that the spectral-efficiency of NOMA scheme is considerably higher than those of scheme. Moreover, the spectral-efficiency of the proposed sub-optimal approach is nearer to the optimal value. The proposed WOA algorithm attains near optimal performance with minimal computational complexity. In addition, as the number of users increases the computational cost of the exhaustive-search algorithm increases as compared to WOA.
Figure 4: Illustration of spectral efficiency of WOA with increasing γ.
For NOMA uplink systems, the power control approach in Sedaghat & Müller (2018) is provided as a benchmark scheme, where the spectral efficiency are near to the optimal value. Noted that the approach used in Sedaghat & Müller (2018) is valid only for two user-pairing. Hence, the proposed scheme performs admirably in-terms of having efficient user grouping for multiple users.
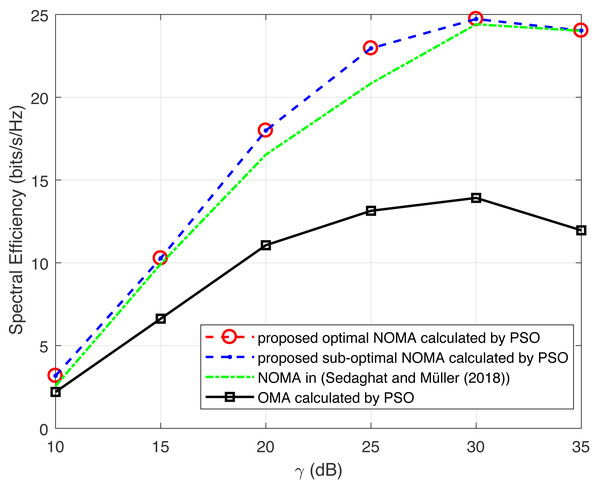
Figures 5 and 6 evaluates the performance of GWO and PSO algorithms in-terms of spectral-efficiency. For uplink NOMA system, the spectral-efficiency of NOMA scheme outperform OMA scheme with varying γ. Moreover, the spectral-efficiency of optimal and sub-optimal solutions are nearer to each other. The power control scheme for NOMA uplink system in Sedaghat & Müller (2018) is used as a benchmark. It has been observed that the spectral-efficiency of both GWO and PSO algorithms shows better results than power control (Sedaghat & Müller, 2018) and OMA scheme.
Figure 5: Illustration of spectral efficiency of GWO with increasing γ.
Figure 6: Illustration of spectral efficiency of PSO with increasing γ.
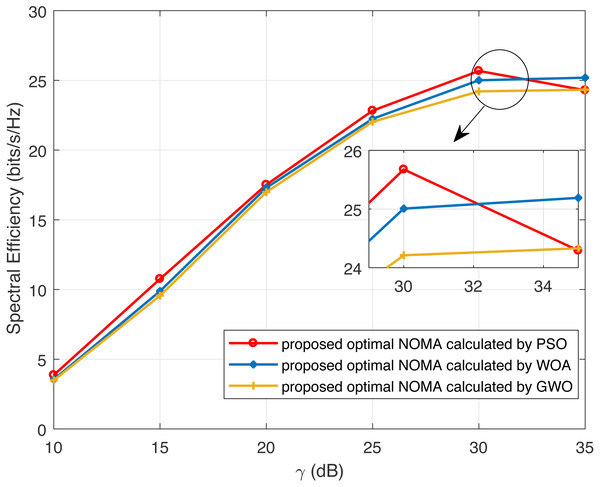
Moreover, a comparison of proposed optimal WOA, GWO and PSO has shown in Fig. 7. The performance of proposed optimal WOA, GWO and PSO are almost nearer to one another. Moreover, as the value of γ above 30 dB, the optimal WOA performs better in-terms of spectral-efficiency as compare to GWO and PSO.
Figure 7: Comparison of optimal solution of WOA, GWO and PSO.
Conclusion
NOMA systems have garnered a lot of interest in recent years for 5G cellular communication networks. The efficient user grouping and power control scheme play an essential role to enhance the performance of communication network. In this paper, we have examined for the first time up to authors knowledge, a joint issue of user-grouping and power control for NOMA uplink systems. we have solved this problem by proposing WOA with low complexity. Further, for comparison, GWO and PSO were adopted to solve the same problem. Simulations results show that the WOA proposed for this combine issue in uplink allows better performance than the conventional OMA in-terms of spectral-efficiency. Further, proposed WOA provides better result as compared to GWO, PSO and existing algorithm in literature with lower system complexity by considering same constraint regarding uplink NOMA systems.The acquired results also suggest that the combinatorial joint problem gets more difficult to solve as the number of users grows and needs additional network resources. In the future, the study might be expanded to include more performance parameters to the mentioned problem and implementation of multiple antennas combinations which leads to massive MIMO (Mulitiple-Input and Multiple-Output) scenario in order to further enhance the performance of the network.
Supplemental Information
Source Code
All related source code files to the WOA implementation for the given NOMA problem and all files related to the compared two GWO and PSO algorithms.