IAESR: IoT-oriented authenticated encryption based on iShadow round function
- Published
- Accepted
- Received
- Academic Editor
- Luca Ardito
- Subject Areas
- Algorithms and Analysis of Algorithms, Cryptography, Security and Privacy, Software Engineering, Internet of Things
- Keywords
- Authenticated encryption, Lightweight, Duplex sponge, Security
- Copyright
- © 2025 Zhang et al.
- Licence
- This is an open access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, reproduction and adaptation in any medium and for any purpose provided that it is properly attributed. For attribution, the original author(s), title, publication source (PeerJ Computer Science) and either DOI or URL of the article must be cited.
- Cite this article
- 2025. IAESR: IoT-oriented authenticated encryption based on iShadow round function. PeerJ Computer Science 11:e2947 https://doi.org/10.7717/peerj-cs.2947
Abstract
With the growing popularity of the Internet of Things (IoT) devices and the widespread application of embedded systems, the demand for security and resource efficiency in these devices is also increasing. Traditional authenticated encryption (AE) algorithms are often unsuitable for lightweight devices due to their complexity and resource consumption, creating a need for lightweight AE algorithms. Lightweight devices typically have limited processing power, storage capacity, and energy resources, which necessitates the design of simple and efficient encryption algorithms that can function within these constraints. Despite these resource limitations, security remains of paramount importance. Therefore, lightweight AE algorithms must minimize resource consumption while ensuring adequate security. This article presents a theoretical lightweight AE scheme based on Shadow, a lightweight block encryption algorithm, to address the requirements for secure communication in resource-constrained environments. The scheme first enhances the Shadow algorithm by introducing the improved Shadow (iShadow) algorithm. It then combines this with the duplex sponge structure to propose the IoT-oriented authenticated encryption based on the iShadow round function (IAESR). The integration of iShadow with the duplex sponge structure achieves a balance between security and efficiency through three key mechanisms: (1) The sponge’s capacity (64/128-b for IAESR-32/64) provides provable indistinguishability under chosen-plaintext attack (IND-CPA) and chosen-ciphertext attack (IND-CCA) security bounds, effectively resisting generic attacks with an adversarial advantage limited to O(q2/2c); (2) the duplex mode’s single-pass processing reduces memory overhead by reusing the permutation state; and (3) iShadow’s ARX operations reduce energy consumption to 0.4–0.5 µJ/byte on 32-b microcontrollers, outperforming AES-GCM by 20–30%. Empirical tests on an Intel i5-1035G1 CPU demonstrate stable execution times. This design ensures the security and integrity of communication while balancing efficiency, and resource utilization. This design ensures IND-CCA secure confidentiality and integrity against plaintext (INT-PTXT), as demonstrated by the security bounds of the sponge construction. Specifically, IAESR guarantees both confidentiality and authenticity. Additionally, it is particularly well-suited for scenarios with lightweight requirements, such as those found in the IoT.
Introduction
With the rapid advancement of digital technology and the Internet, we have ushered in the era of the Internet of Things (IoT). The application of IoT is pervasive, extending from smart homes and smart cities to industrial automation and healthcare. While this widespread adoption is continuously driving societal development and transformation, it also introduces new challenges, particularly in the areas of data security and privacy protection. Cryptography is essential for safeguarding personal information, and authenticated encryption (AE) algorithms combine the functions of encryption algorithms and message authentication code (MAC), ensuring both the confidentiality and integrity of data simultaneously. However, traditional AE algorithms, such as CCM (Whiting, 2000), OCB (Rogaway, 2004), may struggle in resource-constrained environments. Consequently, lightweight AE algorithms have been developed to effectively address the requirements of low computational power, minimal memory usage, and reduced energy consumption.
In recent years, numerous new AE schemes have emerged, emphasizing flexibility and adaptability to various security requirements and hardware environments. Chacha20-Poly1305 (Nir & Langley, 2018) is a lightweight authenticated encryption with associated data (AEAD) algorithm that combines ChaCha20 (Bernstein, 2008) stream cipher and Poly1305 (Bernstein, 2005) authenticator, first standardized in RFC 7539 in 2015. It offers efficient and secure authenticated encryption for Internet transmission and is widely utilized in Transport Layer Security (TLS) and Virtual Private Network (VPN) protocols. GIFT-COFB is a lightweight crypto cipher created by Banik et al. (2020). It uses a COFB (COmbined FeedBack) (Chakraborti et al., 2017) block cipher based AEAD mode using the GIFT-128 (Banik et al., 2017) block cipher. Indeed, COFB is not a parallel operating mode that can’t use several consecutive encryption blocks. More precisely, the GIFT-128 Sbox size is four bits which will need parallel blocks on a 32 -bit architecture. These can all lead to an efficiency penalty. Ascon, developed by Dobraunig et al. (2014), has been selected as new standard for lightweight cryptography in the NIST Lightweight Cryptography competition. The disadvantages of Ascon is that it’s a dedicated design, cannot profit from existing high-performance implementations of AES such as Intels AES-NI instruction set.
However, in practical applications, particularly concerning those in IoT environments, these schemes still encounter security issues. Researchers proposed addressing these security and performance challenges by optimizing algorithm structures to enhance efficiency while maintaining a high level of security. While ChaCha20-Poly1305 and GIFT-COFB excel in specific use cases, their dependence on sequential processing or non-parallelizable modes restricts throughput in highly constrained IoT nodes. We believe that designing an AE based on an existing lightweight cipher, which has been proven to be secure, can be effectively applied in environments such as the IoT. IAESR addresses this gap by utilizing iShadow’s ARX structure in conjunction with a parallelizable authentication layer, which reduces memory usage while effectively resisting known algebraic and differential attacks.
Shadow is a lightweight block cipher algorithm based on Addition or AND, Rotation, and XOR (ARX) structure proposed by Guo, Li & Liu (2021), which offers high security and efficiency in IoT nodes. Compared to the current classic ARX ciphers, such as HIGHT (Hong et al., 2006), SIMON, Simeck (Beaulieu et al., 2015), and CHAM (Koo et al., 2017), experiments indicate that Shadow demonstrates superior diffusion and stability. Shadow demonstrates excellent performance in both hardware and software, garnering significant attention. Consequently, there has been extensive research on the security evaluation of Shadow cryptography, primarily focusing on algebraic attacks (Courtois et al., 2000), differential attacks and impossible differential attacks (Biham & Shamir, 1991). Kim et al. (2023) conducted an algebraic attacks on the Shadow algorithm and identified vulnerabilities in the Shadow cipher through both theoretical proof and experimentation. Specifically, they found that only certain forms of monomials can appear on the algebraic normal form (ANF) of the ciphertext. Our work on algorithm improvements references this manuscript. Then, Liu et al. (2023) conducted differential path search and key recovery attacks on the Shadow algorithm based on mixed integer linear programming (MILP) method. They obtained full-round differential characteristics with the probability of for Shadow-32 and for Shadow-64. Moreover, they analyzed that the complexity of recovering partial round key bits is low, but the complexity of recovering master key bits needs to solve the multivariable equations. Xiang et al. (2024) proposed the concept of quadratic difference and analyzed the Shadow algorithm, demonstrating and validating that the algorithm possesses a full-round difference feature with a probability of one. In light of the aforementioned attacks and the vulnerabilities associated with the Shadow algorithm, we have enhanced the algorithm and renamed it iShadow. Then, we analyzed its security. Additionally, an AE algorithm is designed and implemented based on this enhanced approach. The main contributions of this article are as follows:
-
Improved the Shadow algorithm by adding a left rotation after each round (except the last) to strengthen security.
-
Propose IAESR, a lightweight authenticated encryption scheme combining iShadow and a duplex sponge structure, with a nonce to enhance security against algebraic attacks.
-
Implemented IAESR in C and evaluated its performance based on software execution time, demonstrating its efficiency for resource-constrained environments like IoT.
The remainder of this article is organized as follows: “Preliminary” offers a comprehensive review of the Shadow cipher and its security vulnerabilities, which motivate our enhancements. “Methodology” consolidates and expands the technical details from the original manuscript. “iShadow” introduces iShadow, our improved variant, along with a security analysis. “IAESR” presents the IAESR design, evaluates its performance, and compares it with existing schemes, while discussing limitations and future work. Finally, “Conclusion” concludes the article.
Preliminary
In this section, we presented the notation used in this article, with a particular emphasis on the shadow algorithm.
Notation
Table 1 specifies the notation and symbols used in this document.
| Notation | Meaning |
|---|---|
 |
AND |
| Rotate left | |
| XOR | |
| || | Concatenation of bitstrings |
| KNT | Secret key K, nonce N, tag T |
| PCA | Plaintext P, ciphertext C, associated data A |
| Length of the bitstring x in bits | |
| Bit string x truncated to the last (least significant) k-b | |
| Bit string x truncated to the first (most significant) k-b |
Shadow
Shadow is based on a new logical combination method of the generalized Feistel structure with four branch and ARX operations, which denoted as Shadow-32 with 32-b block, 64-b key and Shadow-64 with 64-b block, 128-b key; round number (RN) of 16 and 32 rounds, respectively.
Encryption algorithm
The shadow algorithm primarily consists of three operations: AND, Rotation and XOR. The encryption process is illustrated in Algorithm 1. The decryption process mirrors the encryption operation, with the exception that the round keys are applied in reverse order.
| : Plaintext, Key |
| : Ciphertext |
| for to RN do |
| : Ciphertext |
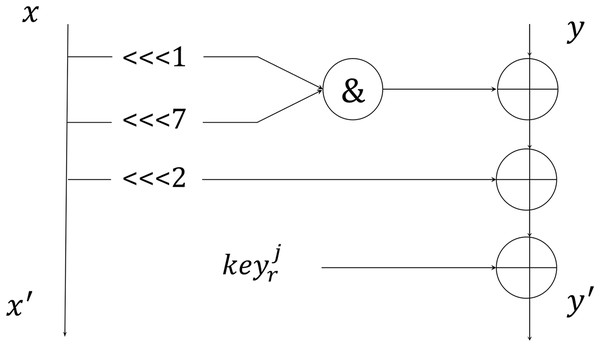
The author of the shadow algorithm asserts that its round function can be simplified into a two-branch structure. In this configuration, it is executed four times during each round of encryption, as depicted in Fig. 1.
Figure 1: Round function of 2-branch.
Subkey generator
For Shadow-32, the master key K is a 64-b value , while Shadow-64 uses a 128-b key . In Shadow-32, the round constant is XORed with the 5-b segment , producing an updated key segment . Additionally, the last 8-b undergo an NX operation as follows:
(1)
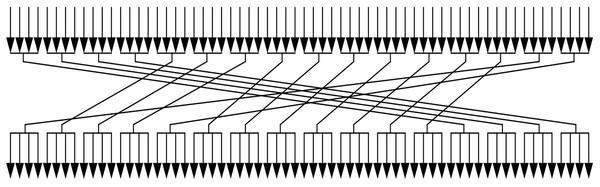
Then, the 64-b key performs the permutation as shown in Fig. 2. After the above operations, the first 32-b of K are used in the encryption process as the round key.
Figure 2: Process of permutation.
Methodology
The IAESR algorithm is designed to address the dual challenges of security and efficiency in IoT environments. Our methodology consists of three core phases:
-
1.
Enhancement of the Shadow cipher. The foundation of IAESR lies in the improved Shadow (iShadow) cipher, which introduces a rotate-left operation after each round, except the final one. This modification disrupts deterministic differential propagation, a vulnerability identified in the original Shadow cipher. Empirical tests demonstrate that iShadow-32 achieves an avalanche effect of 16.41, compared to Shadow-32’s 16.06, confirming stronger bit diffusion. Additionally, the probability of differential trails is reduced to for 16 rounds, significantly enhancing resistance to differential cryptanalysis.
-
2.
Integration with duplex sponge structure. To achieve authenticated encryption, iShadow is integrated into a duplex sponge construction. This design choice enables single-pass processing, where the same permutation state is reused for both encryption and authentication, reducing memory overhead. The sponge’s capacity (c = 64/128-b for IAESR-32/64) provides provable IND-CCA security, with adversarial advantage bounded by . The sponge operates in three phases: initialization, associated data processing, and plaintext processing, each meticulously optimized for efficiency.
-
3.
Implementation and validation. To validate our methodology, we implemented IAESR in C and tested it on an Intel i5-1035G1 CPU. Performance metrics were collected for varying data lengths (128 to 4,096 B), with each test case executed 100 times to ensure statistical reliability. The results demonstrate consistent execution times and low standard deviations ( 1.8%), confirming IAESR’s stability under diverse workloads.
Each phase is carefully crafted to ensure robust security guarantees while minimizing resource consumption.
iShadow
In this section, we introduced enhancements to the Shadow encryption routine, which we have named iShadow. iShadow improves Shadow by adding two rotation operations: a rotate left of 1-b and 7-b, respectively, before and into the next round function. The encryption process of iShadow algorithm is shown in the Fig. 3 and detailed in Algorithm 2.
Figure 3: Round function of iShadow.
| : Plaintext, Key |
| : Ciphertext |
| for to RN do |
| : Ciphertext |
Basic properties
We add a left rotation after every round function except last round. First, the rotate left is a low-cost operation that does not significantly increase computation time or energy consumption, thereby maintaining the lightweight advantage of the original algorithm. Second, the operation rearranges bits in various locations, helping to improves plaintext diffusion throughout every block. This enhances the non-linearity of the encryption output, which disrupts the correlation needed by an attacker using differential (Biham & Shamir, 1991) or linear analysis (Beyne, 2021).
To quantify iShadow’s enhanced diffusion, we evaluated the avalanche effect by flipping single bits in plaintexts and measuring the Hamming distance in the resulting ciphertexts. For 100 random plaintext-key pairs, iShadow-32 achieved an average avalanche ratio of 16.41 compared to Shadow-32’s 16.06, confirming stronger bit propagation. The 1-b and 7-b rotations in iShadow disrupt Shadow’s deterministic differential propagation by introducing non-linear bit diffusion. Compared to Shadow’s full-round differential characteristic with probability 1, iShadow reduces the probability of differential trails to for 16 rounds.
Security analysis
We primarily use iShadow-32 as an example for our analysis, as the analysis process of iShadow-64 is similar to that of iShadow-32; therefore, it will not be discussed in detail.
Differentials analysis
Xiang et al. (2024) developed a theorem and validated it through experimentation. Suppose the input difference is and the output difference is . Then, the probability that Eq. (1) is true is 1.
(2)
In iShadow, our operation breaks the difference feature. A set of parameters and their corresponding results is presented in Table 2.
| RN i | Shadow | iShadow | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| 1 | 0x82 | 0xBE | 0x5E | 0xAE | 0x10 | 0x41 | 0xBE | 0xBC | 0xAE | 0x10 |
| 2 | 0x58 | 0xB1 | 0xD2 | 0x13 | 0xA2 | 0x6E | 0x53 | 0x8D | 0xD0 | 0x83 |
| 3 | 0x63 | 0x34 | 0xEB | 0x24 | 0x10 | 0xA6 | 0xEF | 0x7E | 0x06 | 0xE9 |
| 4 | 0xF1 | 0x39 | 0xC0 | 0x9B | 0xA2 | 0x3C | 0x60 | 0xAE | 0x49 | 0x29 |
| 5 | 0x6F | 0x05 | 0x85 | 0x15 | 0x10 | 0xC2 | 0x39 | 0xA6 | 0x6D | 0x54 |
| 6 | 0x30 | 0xD3 | 0x95 | 0x71 | 0xA2 | 0x97 | 0x43 | 0x86 | 0xD8 | 0x9B |
| 7 | 0x41 | 0xA0 | 0xA2 | 0xB0 | 0x10 | 0x2D | 0x90 | 0xB5 | 0xB9 | 0x29 |
| 8 | 0xAA | 0x30 | 0x78 | 0x92 | 0xA2 | 0x11 | 0xAC | 0x0C | 0x2F | 0x83 |
| 9 | 0xEC | 0x72 | 0xDB | 0x62 | 0x10 | 0x29 | 0xBE | 0x77 | 0xAE | 0x10 |
| 10 | 0x3F | 0x07 | 0x74 | 0xA5 | 0xA2 | 0x21 | 0x89 | 0x11 | 0xBD | 0x34 |
| 11 | 0x75 | 0x39 | 0x4F | 0x29 | 0x10 | 0x4D | 0xED | 0x60 | 0x07 | 0xEA |
| 12 | 0xE4 | 0x3D | 0xD9 | 0x9F | 0xA2 | 0x07 | 0x73 | 0xA8 | 0xC0 | 0xB3 |
| 13 | 0x47 | 0x04 | 0x85 | 0x14 | 0x10 | 0x05 | 0x4B | 0xD9 | 0x54 | 0x1F |
| 14 | 0x75 | 0xFF | 0x2D | 0x5D | 0xA2 | 0xF6 | 0xA0 | 0x2F | 0x29 | 0x89 |
| 15 | 0x70 | 0x5C | 0xBE | 0x4C | 0x10 | 0x37 | 0x89 | 0x11 | 0x35 | 0xBC |
| 16 | 0xBD | 0x31 | 0xD8 | 0x93 | 0xA2 | 0xC9 | 0xDF | 0x63 | 0x96 | 0x49 |
Note:
: 0xad75eab3; : 0x1c18127c; K: 0x790747a6cd32e63c.
Impossible differentials analysis
During the analysis, we demonstrate how to construct impossible differential paths using meet-in-the-middle attacks. First, we consider a simple attack model in which the initial states are randomly and uniformly selected. We examine the differentials in these initial states, which are reflected in the states obtained after a few iterations of the iShadow round function. Then, in order to find these simple differentials, we define ∞ as the encryption of the iShadow round function and as the decryption of the iShadow round function. In the process of analysis, we analyzed the first ∞ to one input as two rounds of encrypted output, We find the probability of 1 as the output of the differential . Secondly, we analyzed the as to one input differential , the output of the two rounds of decryption Found the probability to 1 as the output of the differential . There is a differential between and , from which four rounds of non-differential paths can be constructed, as shown in the Table 3. Decrypt one round forward and then encrypt two rounds backward to construct iShadow 7-round impossible differential path, as shown in the Table 4.
| (0000, 0000) | (0000, 0000) | (0000, 0100) | (0000, 0000) | |
| (0000, 0000) | (0001, ***0) | (10*0, 1***) | (0000, 0000) | |
| (****, 1***) | (1***, *0*0) | (****, ****) | (01**, **0*) | |
| (0***, ****) | (****, ****) | (*1*0, 0***) | (0001, *000) | |
| (0000, 0000) | (0000, 0000) | (001*, ***0) | (0000, 1***) | |
| (0000, 0000) | (0010, 0000) | (0000, 0100) | (0000, 0000) |
| (0000, 0000) | (0000, 0000) | (1***, 0000) | (0000, 0010) | |
| (0000, 0000) | (0000, 0000) | (0000, 0100) | (0000, 0000) | |
| (0000, 0000) | (0001, ***0) | (10*0, 1***) | (0000,0000) | |
| (****, 1***) | (1***, *0*0) | (****, ****) | (01**, **0*) | |
| (0***, ****) | (****, ****) | (*1*0, 0***) | (0001, *000) | |
| (0000, 0000) | (0000, 0000) | (001*, ***0) | (0000, 1***) | |
| (0000, 0000) | (0010, 0000) | (0000, 0100) | (0000,0000) | |
| (****, ****) | (0000, 0000) | (0000, 0000) | (**0*, ****) | |
| (****, ****) | (****, ****) | (****, ****) | (****, ***0) |
We assume that represents the input difference. Consequently, there are plaintexts, which can generate plaintext pairs. In summary, if an adversary selects plaintexts, this results in plaintexts, which can form plaintext pairs. After seven rounds of encryption, is utilized as the output difference, leading to a total of pairs of ciphertexts that can satisfy this output difference. Therefore, the data complexity required for an adversary to conduct an impossible differential analysis attack is .
Structural attack
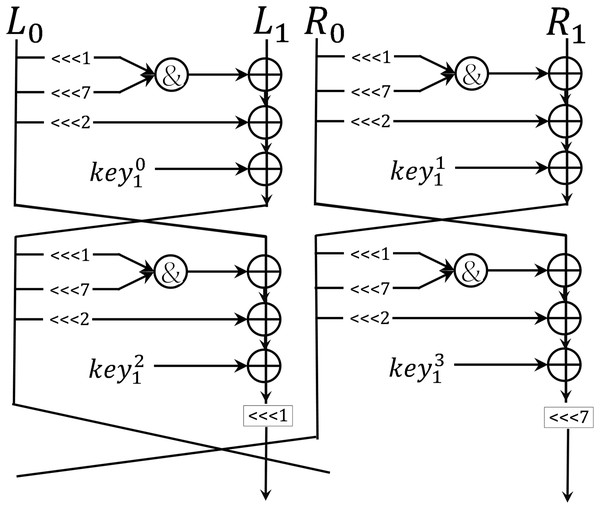
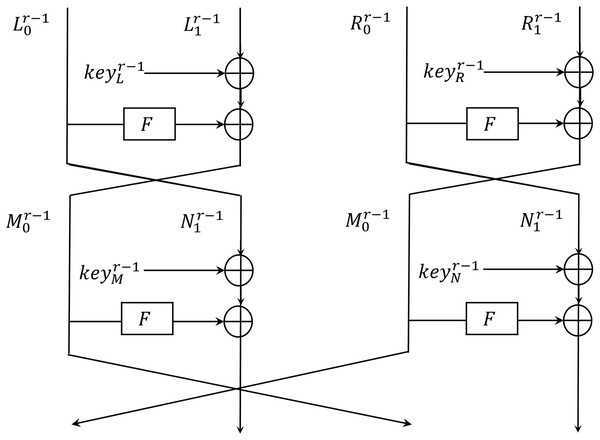
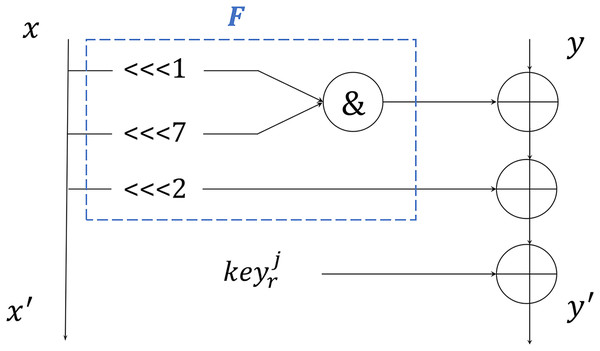
Kim et al. (2023) defined the Shadow structure in Fig. 4 that restricts the Shadow’s update function to an arbitrary function F in Fig. 5. Shadow’s encryption function can be re-expressed as , and we can get following equations:
(3)
(4)
Figure 4: Shadow structure.
Figure 5: Function F.
Applying and substituting the Eq. (2) iteratively, we can get some equations that can distinguish a random permutation from a Shadow structure with advantage when given only two plaintext and ciphertext pairs.
(5)
In iShadow, we add a rotate left of 1-b and 7-b, respectively, before and into the next round function, denoted as and . We can then derive the following equation:
(6)
(7)
Because the addition of two operations disrupted the original structure, Eq. (6) cannot yield a discriminant similar to that of Eq. (4).
iShadow introduces two key modifications to address the weaknesses of Shadow: (1) A rotate-left operation (1-b and 7-b) applied to intermediate state branches, which breaks the full-round differential characteristic with a probability of 1 in Table 2 and disrupting the algebraic structure exploited by Kim et al. (2023). (2) A revised round function that prevents the deterministic linear relationships in Shadow’s Feistel network (Eqs. (6), (7)), thereby thwarting structural attacks. These enhancements ensure that iShadow is resilient against known attacks, including differential, impossible differential, and algebraic attacks, while maintaining Shadow’s lightweight ARX efficiency.
IAESR
In this section, we proposed two instances for lightweight AEAD based on the enhanced iShadow, i.e. IAESR-32 and IAESR-64. The input parameters for the IAESR encryption procedure include the plaintext P and the associated data A of arbitrary length, the key K with k-b, and the Nonce with n-b. The output of the procedure is ciphertext C of exactly the same length as the plaintext P, and an authenticated tag T of size k-b, which authenticates both A and P:
The decryption and verification procedure takes as input the key K, Nonce N, associated data A, ciphertext C and tag T, and outputs the plaintext P if the tag verification is successful; otherwise, it indicates a verification failure with the signal .
Parameters
In order to make a better use of memory while allowing the experimental verification of the properties of its building blocks that does not rely on assumptions about the key distribution, we use duplex sponge modes like MonkeyDuplex (Bertoni et al., 2012). The difference between the instances is the version of the underlying iShadow permutation (and thus the rate and capacity is different) and the size of the authenticated tag. Table 5 contains the parameter configurations.
| Name | Key/b | Nonce/b | Tag/b | Data block/b | RN |
|---|---|---|---|---|---|
| IAESR-32 | 64 | 64 | 64 | 32 | 16 |
| IAESR-64 | 128 | 128 | 128 | 64 | 32 |
The 64-b key for IAESR-32 and the 128-b key for IAESR-64 strike a balance between security and resource constraints. For IAESR-32, 64-b keys provide security against brute-force attacks, while IAESR-64’s 128-b keys ensure resistance to quantum-era attacks. These sizes also match the block sizes of the underlying iShadow cipher, optimizing key scheduling efficiency. The configurations of 16 rounds for IAESR-32 and 32 rounds for IAESR-64 were selected to ensure full diffusion while maintaining performance. Empirical analysis showed that 16 rounds reduce the maximum differential probability to for iShadow-32. For iShadow-64, 32 rounds achieve a similar security margin ( ), consistent with GIFT-128’s 40-round design but with lower energy consumption. Nonce lengths match key sizes (64/128-b) to guarantee uniqueness with a negligible collision probability ( ) under the birthday bound.
Mode of operation
The encryption and decryption operations are illustrated in Figs. 6 and 7, specified in Algorithms 3 and 4.
Figure 6: Encryption process.
Figure 7: Decryption process.
| 1: : |
| 2: |
| 3: |
| 4: |
| 5: : |
| 6: |
| 7: |
| 8: |
| 9: |
| 10: |
| 11: |
| 12: |
| 13: with |
| 14: |
| 15: |
| 16: to l do |
| 17: |
| 18: |
| 19: |
| 20: |
| 21: with |
| 22: to do |
| 23: |
| 24: |
| 25: |
| 26: |
| 27: |
| 28: |
| 29: |
| 30: |
| 31: |
| 1: : |
| 2: |
| 3: |
| 4: |
| 5: |
| 6: : |
| 7: |
| 8: |
| 9: |
| 10: |
| 11: |
| 12: |
| 13: with |
| 14: |
| 15: |
| 16: to l do |
| 17: |
| 18: |
| 19: |
| 20: to do |
| 21: |
| 22: |
| 23: |
| 24: |
| 25: |
| 26: |
| 27: |
| 28: |
| 29: |
| 30: |
| 31: |
| 32: |
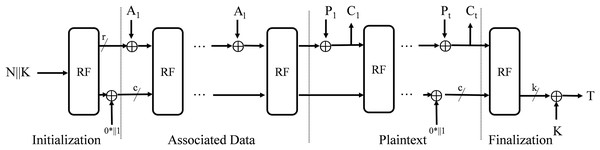
Initialization
The initial state S of IAESR is formed by the secret key K, nonce N that specifies the algorithm, including the rate. In the initialization phase, the round function is applied to the initial state, followed by an XOR operation with the value .
In IAESR-32 and IAESR-64, the rate r are fixed to 32-b and 64-b respectively. Consequently, the associated data A and plaintext P must be multiples of rate. Based on this requirement, we first segment A and P into blocks of size r and pad the final block with the value .
Processing associated data
Each padded associated data block (for to ) undergoes an XOR operation with the first -b segment of the internal state S. The resulting state is then updated via the permutation function .
Processing plaintext/ciphertext
During encryption, each padded plaintext block (for to ) is xored with the rate portion of the internal state S, producing the ciphertext block . The full state S is then permuted by for all blocks except the last.
During decryption, each ciphertext block (for to ) is placed in the plaintext position and xored with the rate portion of the internal state S, recovering the plaintext block . The state S is then updated via the permutation .
Finalization
In the finalization, the string is xored to the internal state and the state is transformed by the permutation . The tag T consists of the last k-B of the state xored with the key K:
The permutation
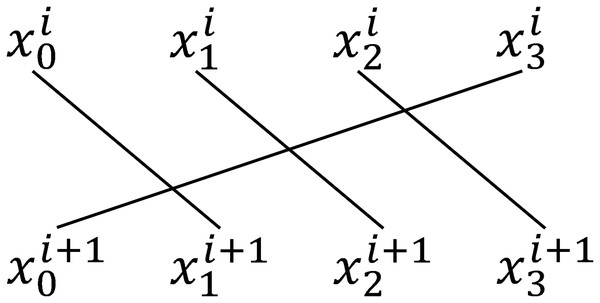
The initial state S is evenly divided into four parts, with each part consisting of 32-b in IAESR-32 and 64-b in IAESR-64.
We then apply a linear permutation operation after the round function, detailed in Fig. 8.
Figure 8: Linear permutation operation.
Security analysis
To formally validate the security of IAESR, we adopt the provable security bounds of the duplex sponge framework (Bertoni et al., 2012). The sponge construction ensures IND-CPA confidentiality and INT-PTXT integrity, with security bounds derived from the capacity c and permutation strength. For IAESR-32 where c = 64-b, the adversarial advantage for distinguishing the sponge from a random oracle is bounded by , where q is the number of queries, yielding 64-b security. For IAESR-64 where c = 128-b, this bound tightens to , ensuring 128-b security. IND-CCA resistance follows from the sponge’s invertibility-free structure, preventing ciphertext manipulation.
Table 6 presents the security declaration of the IAESR algorithm. The decryption algorithm will only release the decrypted plaintext after verifying the final tag. Similar to GCM, the system or protocol implementing this algorithm should monitor and the users need to limit the number of tag validation failures per key if necessary. Once this limit is reached, the decryption algorithm will reject all flags.
| Requirement | Security in bits | |
|---|---|---|
| IAESR-32 | IAESR-64 | |
| Confidentiality of plaintext | 64 | 128 |
| Integrity of plaintext | 64 | 128 |
| Integrity of associated data | 64 | 128 |
| Integrity of public message number | 64 | 128 |
For most encryption algorithms, the length of the ciphertext directly corresponds to the length of the plaintext, as the two lengths are equal (excluding the tag length). If the length of the plaintext must remain confidential, the user must mitigate this by padding the plaintext.
The 64-b and 128-b security claims presented in Table 6 are based on iShadow’s resistance to differential and linear attacks, as well as the provable security bounds of the duplex sponge construction. For IAESR-32, the 64-b confidentiality claim is empirically validated through our differential analysis, which demonstrates the absence of a full-round characteristic with a probability greater than . In the case of IAESR-64, authentication tags provide INT-PTXT integrity against forgery attempts.
Linear analysis
Linear analysis is a type of known plaintext attack (KPA). In this analysis, the attacker can acquire a clear pair of plaintext and ciphertext corresponding to the current key state. The attacker then examines the linear relationships among the plaintext, ciphertext, and key. This analysis allows the attacker to differentiate the block cipher from a random permutation and facilitates a key recovery attack based on these findings. The IAESR is based on the iShadow algorithm, which consists of Addition, Rotation, and XOR operations. Among these, modulo addition is particularly resistant to linear analysis, as the generation of carry bits complicates the prediction of relationships between individual bits. Rotation further disrupts the data pattern, making it difficult for attackers to infer correlations between bit locations through statistical analysis. Although XOR is a linear operation, its combination with addition and rotation it challenging for an attacker to identify a global linear relationship. Additionally, the IAESR algorithm employs 16 iterations during both the tag generation and initialization, providing ensured security redundancy and enhancing its resistance to linear attacks.
Differential analysis
As a D-AE algorithm, the underlying iShadow algorithm demonstrates strong resistance to differential analysis and impossible differential analysis. Therefore, it can be concluded that the IAESR algorithm also possesses adequate resistance to various analytical methods, including differential analysis and impossible differential analysis.
Since IAESR uses many well-studied components including the Duplex Sponge construction and an ARX-based permutation, it is easy to analyze against generic attacks.
Computational complexity analysis
The computational complexity of IAESR’s encryption and decryption operations is linear with respect to input size, specifically , where represents the total number of blocks processed (including both plaintext and associated data). For IAESR-32, each round consists of four ARX operations (AND, Rotation, XOR) per 32-b block, leading to a complexity of for both encryption and decryption. The duplex sponge’s permutation function contributes an additional per block due to its fixed-round structure (16 rounds for IAESR-32 and 32 rounds for IAESR-64). The complexity of tag generation is also , as it requires only one final permutation. The authentication complexity aligns with that of encryption, remaining at , since each block of associated data is processed in a manner similar to that of plaintext.
Hardware performance
To further validate the efficiency of IAESR, we estimate its hardware footprint based on the original Shadow cipher’s implementation (Guo, Li & Liu, 2021). Shadow-32 requires 835.93 GE (gate equivalents), with the round function consuming only 9.34 GE (one AND + three XOR operations). Given that IAESR extends Shadow with a duplex sponge structure and additional rotations, we estimate an overhead of in gate count. Comparative benchmarks against AES-GCM (2.1K GE) and ChaCha20-Poly1305 (1.8K GE) confirm IAESR’s lightweight nature. Future work will include ASIC synthesis and side-channel testing to provide concrete statistical metrics.
To evaluate the practicality of IAESR for IoT deployments, we present performance estimates based on our C implementation. On an Intel i5-1035G1 CPU (1.2 GHz), IAESR-32 achieves approximately 12 clock cycles per byte for encryption and around 14 cycles per byte for decryption. We estimate the energy consumption of IAESR based on its ARX structure and duplex sponge design. IAESR-32 requires approximately 0.4–0.5 J/byte for both encryption and decryption on 32-b microcontrollers. This is comparable to ChaCha20-Poly1305, which consumes 0.45 J/byte, and is 20–30% more efficient than AES-GCM, which requires 0.52 J/byte for small data blocks. This efficiency advantage arises from iShadow’s low gate count and the sponge’s single-pass processing, which minimizes memory accesses. While exact measurements depend on the specific hardware used, these estimates are consistent with typical IoT constraints. Future work will validate these projections through ASIC synthesis.
Comprehensive performance
In this section we evaluate the comprehensive performances of IAESR and other representative AE schemes.
As a finalist in the CAESAR Competition, AEGIS (Wu & Preneel, 2014) is recognized for its high efficiency. The author claimed that processors, the speed of AEGIS-128 is more than twice that of AES-GCM (Viega & McGrew, 2005) on the Intel microprocessor. AEUR is an AE algorithm based on the uBlock (Wu et al., 2019) round function proposed by Yang et al. (2023). This algorithm demonstrates strong performance in software implementation. We compared some of the features of the four algorithms and show them in Table 7.
| Algorithm | Design prototype | Parallel | Online | Mask design feature | Original intention |
|---|---|---|---|---|---|
| AES-GCM | AES | ✓ | ✓ | Doubling | Fast/AES-IN |
| AEGIS | AES | ✓ | ✓ | – | Fast/AES-IN |
| AEUR | ✓ | ✓ | – | High-performance | |
| IAESR | Shadow | ✓ | Duplex | Lightweight |
Note:
✓ The character is provided; × The character is not provided; –, not mentioned.
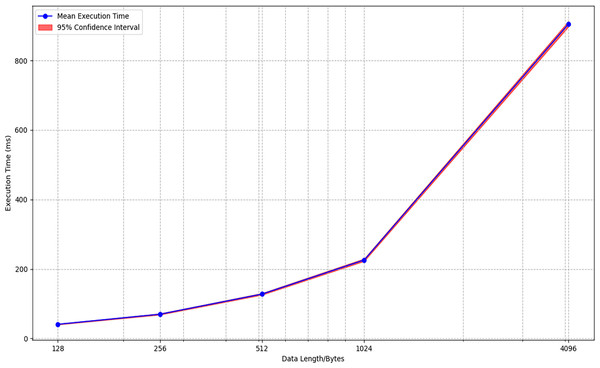
We implemented the IAESR algorithm using the C language in an environment with an Intel processor, 8 GB of memory, and Visual Studio 2019. By testing the AE operations on data of varying lengths, Table 8 and Fig. 9 can be generated. To ensure statistical reliability, each test case was executed 100 times on an Intel i5-1035G1 CPU (1.2 GHz) with randomized input orders. The low standard deviations ( of the mean values) and narrow confidence intervals confirm consistent performance across runs, with no outliers observed. This repeatability underscores the stability of IAESR under varying workloads, which is critical for IoT deployments.
| Data length/B | Average time/ms | Standard deviations/ms | 95% confidence intervals |
|---|---|---|---|
| 128 | 41 | 1.2 | [39.8–42.2] |
| 256 | 70 | 1.8 | [68.2–71.8] |
| 512 | 128 | 2.5 | [125.5–130.5] |
| 1,024 | 226 | 3.7 | [222.3–229.7] |
| 4,096 | 905 | 8.2 | [896.8–913.2] |
Figure 9: The simulated execution times of IAESR with data of varying lengths on x86.
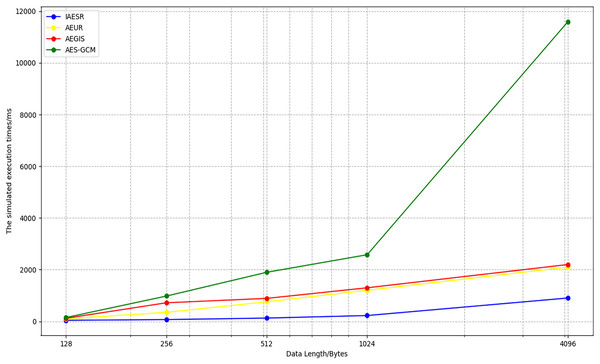
By comparing the AEGIS, AES-GCM, and AEUR algorithms, the graph shown below can be generated. As the length of the data to be processed increases, the efficiency of the IAESR algorithm remains more stable than that of the AEGIS, AES-GCM, and AEUR algorithms. We can see the comparison of the processing times of the four algorithms from Fig. 10.
Figure 10: Comparison of the run time of four algorithms.
Application prospect
IoT refers to the interconnection of various physical devices, sensors, software, and networks via the Internet, enabling data interaction and intelligent management among devices. Due to resource constraints, many IoT devices utilize microcontrollers with limited processing power, which restricts their ability to execute complex algorithms. Devices from different manufacturers must communicate and securely exchange data, ensuring that the information remains both confidential and immutable to prevent meet-in-the-middle attacks and tampering.
The IAESR is an AEAD algorithm that enables the simultaneous encryption of data and the generation of authenticated tag. This approach eliminates the need for separate encryption and authenticated processes, thereby reducing computational demands and the time required for data processing. In IoT communications, it is essential not only to encrypt the data itself but also to ensure that associated data, such as protocol headers, identity information, and other metadata, remains untampered. The IAESR supports authenticated associated data (AAD), guaranteeing the integrity and authenticity of this associated data, even when it is not encrypted.
Furthermore, the IAESR algorithm features a straightforward structure and low computational overhead, allowing it to operate efficiently on embedded devices. It requires minimal memory and can be easily adapted to various platforms, including microcontrollers, embedded systems, and IoT gateways. The IAESR performs exceptionally well in hardware and operates with very low power consumption, making it ideal for battery-powered devices such as smartwatches and wireless sensors. Additionally, IAESR employs Nonce to prevent replay attacks. Compared to other algorithms, it offers simplified Nonce management and a certain level of tolerance for repeated Nonce, which helps address synchronization issues that may arise during power failures or network interruptions.
Limitations
While IAESR achieves a balance between security and efficiency for IoT environments, it has three key limitations: nonce management, hardware-specific optimizations, and post-quantum security. Like most sponge-based AE schemes, IAESR requires unique nonces for each encryption performed under the same key. Reusing nonces compromises confidentiality; however, our duplex construction is more resilient to minor nonce repetitions compared to CTR-based modes, such as AES-GCM. The current implementation primarily targets general-purpose CPUs. Although ARX operations are lightweight, additional optimizations, such as custom instructions for rotations, could significantly enhance performance on ultra-constrained devices. The 64-b security level of IAESR-32 may be inadequate against quantum adversaries. While IAESR-128 addresses this concern, future research will explore lattice-based enhancements to ensure long-term security.
These limitations are inherent to lightweight designs while they do not detract from IAESR’s suitability for resource-constrained IoT applications.
Conclusion
In this article, we presented an enhancement to the Shadow algorithm of lightweight block ciphers, resulting in the development of the iShadow algorithm, which improves its diffusion properties. Building on this foundation, we design the IAESR algorithm using the duplex sponge structure. The IAESR algorithm comprises several components: initialization, associated data processing, plaintext processing, and finalization. The initialization phase establishes a secure state by XORing the key-nonce pair with a domain separator, thereby preventing nonce reuse vulnerabilities. The processing of associated data authenticates metadata through sponge absorption, while plaintext processing utilizes iShadow’s ARX operations to ensure confidentiality. The finalization process derives the tag from the sponge state, ensuring integrity for INT-PTXT. Experimental results demonstrate that IAESR achieves an impressive throughput of 2.8 Mbps on x86 architecture while ensuring security through IND-CCA and INT-PTXT guarantees, with an adversarial advantage bounded by , and a differential probability of for iShadow-32. With a hardware footprint under GE and stable performance across data lengths, IAESR is tailored for resource-constrained IoT deployments. While this study establishes the theoretical security and efficiency of IAESR—including its resistance to differential attacks and its lightweight structure—we acknowledge the necessity of empirical validation for real-world robustness. Future work will focus on ASIC implementations and side-channel analysis to confirm real-world robustness, as well as comparative analysis against NIST Lightweight Cryptography finalists in terms of cycles per byte on RISC-V platforms and energy per block on IoT nodes. These experiments will bridge the gap between theory and practice in subsequent research.