A novel multi-stage distributed authentication scheme for smart meter communication
- Published
- Accepted
- Received
- Academic Editor
- Haider Abbas
- Subject Areas
- Cryptography, Emerging Technologies, Security and Privacy
- Keywords
- Smart meter, Authentication, Security, Smart grid, Cybersecurity
- Copyright
- © 2021 Hegde et al.
- Licence
- This is an open access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, reproduction and adaptation in any medium and for any purpose provided that it is properly attributed. For attribution, the original author(s), title, publication source (PeerJ Computer Science) and either DOI or URL of the article must be cited.
- Cite this article
- 2021. A novel multi-stage distributed authentication scheme for smart meter communication. PeerJ Computer Science 7:e643 https://doi.org/10.7717/peerj-cs.643
Abstract
Smart meters have ensured effective end-user energy consumption data management and helping the power companies towards network operation efficiency. However, recent studies highlighted that cyber adversaries may launch attacks on smart meters that can cause data availability, integrity, and confidentiality issues both at the consumer side or at a network operator’s end. Therefore, research on smart meter data security has been attributed as one of the top priorities to ensure the safety and reliability of the critical energy system infrastructure. Authentication is one of the basic building blocks of any secure system. Numerous authentication schemes have been proposed for the smart grid, but most of these methods are applicable for two party communication. In this article, we propose a distributed, dynamic multistage authenticated key agreement scheme for smart meter communication. The proposed scheme provides secure authentication between smart meter, NAN gateway, and SCADA energy center in a distributed manner. Through rigorous cryptanalysis we have proved that the proposed scheme resist replay attack, insider attack, impersonation attack and man-in-the-middle attack. Also, it provides perfect forward secrecy, device anonymity and data confidentiality. The proposed scheme security is formally proved in the CK—model and, using BAN logic, it is proved that the scheme creates a secure session between the communication participants. The proposed scheme is simulated using the AVISPA tool and verified the safety against all active attacks. Further, efficiency analysis of the scheme has been made by considering its computation, communication, and functional costs. The computed results are compared with other related schemes. From these analysis results, it is proved that the proposed scheme is robust and secure when compared to other schemes.
Introduction
The smart grid is one of the critical infrastructures for any nation. The traditional energy system equipped with advanced sensing, communication and control technologies transforms the decades old power system into a smart grid. While the smart grid provides a wide range of utilities and help the end-users to improve their lifestyle and minimize the cost of energy, new types of cyber-threats have emerged. According to a recent report published by Kaspersky, a noticeable number of cyber incidents were reported in the energy control centres (In H1 2020, ICS computers blocked 32.6% malicious contents) that has raised a major concern (Kaspersky ICS CERT, 2020). For example, a ransomware attack on a large Portuguese energy company was claimed to have stolen around 10TB of sensitive information. As per the report, the major categories of the cyber attacks experienced by the industrial control centre (ICS) of the energy system are worms, spyware and cryptocurrency miners. If not detected, these cyber attacks and new sophisticated threats can cause significant damage to the physcial assets, financial losses, and may even create catastrophic cascading failures. Hence, a good number of research is going on towards the investigation of emerging attacks and threat models (Anwar, Mahmood & Pickering, 2016; Anwar, Mahmood & Pickering, 2017; Anwar, Mahmood & Ahmed, 2015) for the energy system and possible countermeasures (Yang et al., 2014; Anwar, Mahmood & Tari, 2015).
In recent years, smart meters (SM) have been widely deployed to monitor energy usages of the end-user’s consumption data. For example, smart meters have been installed in all residential homes across Victoria, which is one of the major Australian states (DELWP, 2020). SMs have provided the customers insights on their consumption profile and opened the door for data driven informed decision making and control energy at a household level. However, SM data communication is based on wireless medium and making the use of internet technologies. Wireless communication model for SM data transmission may allow malicious attackers to perform various attacks if they do not have a robust security system (Gope & Sikdar, 2018). If the system is compromised by an adversary, the attacker can eavesdrop and modify the communication data. This kind of attack is data privacy and confidentiality attack. Also, the attacker can interrupt the transmitted messages or cause a Denial of Service (DoS) and/or jamming attack against the system that may lead to a data availability attack. Moreover, a new type of attack has emerged where the attacker can inject malicious or false information into the smart meter data payloads and corrupt the original information (Anwar, Mahmood & Tari, 2015). This kind of attack is known as a data integrity attack against smart meters within an advanced metering infrastructures. Hence, attacks on smart meter can impact on the Confidentiality, Integrity and Availability (CIA) triad of an energy systems demand side management. Therefore, the security issues have been highlighted as a major concern of today’s smart grid smart meter communication and data management (Aziz et al., 2019; Ni & Paul, 2019; Anwar, Mahmood & Tari, 2017). Hence, it is necessary to build a powerful security framework for the smart grid system.
Authentication is one of the primary and recommended approaches to address smart grid smart meter communication security issues. In this paper, we have proposed a novel distributed multi-stage authentication scheme for smart grid smart meter communication. There are numerous authentication schemes for smart grid are proposed in recent years. The need for the proposed authentication scheme is that there are drawbacks identified in most of the recently proposed schemes and they fail to achieve security requirements (Zhang et al., 2019). We have listed the potential vulnerabilities which restrict to the providing of secure authentication in the smart grid smart meter communication. Some of the notable drawbacks are: (i) Anonymity and untraceability which is one of the hurdles to achieve the secure authentication. It enables to reveal the identity of the smart meter which holds the partial information of the login message. Also, an unauthorized user may compromise a meter from the physical box and control the home appliances (Kumar et al., 2019). (ii) The smart meter sends unit consumption data periodically: 15/30/60 minutes. The participants involved in the smart grid smart meter communication are connected via the network Kumar et al. (2018). Since the communication has been done through the open channel, the adversary can intercept the network to leak, modify or delete data (Wang & Lu, 2013). Communication interception may leads towards man in middle attack, replay attack and so on.
In smart energy networks, power transmission and distribution system is separated from the data communication network (Fouda et al., 2011). In power transmission and distribution system, electricity is delivered from the power plant to end-users. In this paper, we described the network from the data communications point of view. The detailed system design is illustrated in the “System Model”. Traditionally, the Supervisory Control and Data Acquisition (SCADA) system has been used to monitor and control the power grid. The SCADA system is a centralized system, where the substations are connected to a control center. The centralized structure of the SCADA system limits its scalability and makes its applicability only for local monitoring. But, an extended SCADA system makes it to Wide-area monitoring, protection, and control system (Shin, He & Zhang, 2014; Eder-Neuhauser, Zseby & Fabini, 2016). Here, smart grid topology is split into a number of networks (Zhong, Chim & Hui, 2015). The active participants in the communication are the smart meter (SM), home area network (HAN), neighbourhood area network gateway (NANG) and the SCADA control center/server. These participants are organized in a hierarchical structure for smart grid communications. To implement the mutual authentication between the active participants, several schemes depending upon the trusted third party (Li et al., 2013; Li et al., 2017; Wu et al., 2019). Dependency on the third party always a bottleneck for the system efficiency when it is too busy on handling of large incoming requests (Odelu et al., 2017). Also, a trusted third party should be suitable to adopt communication environment (Irshad et al., 2020). The authentication schemes independent of the trusted third party assumed that the network between NANG and SCADA control server is secure (Li et al., 2019; Kumar et al., 2019). Since the communication between NANG and SCADA control center/server will be done in an open channel, there will be the chances for network interception. Therefore, it is necessary to propose a novel distributed authentication scheme, which is independent from the third party and authenticate all active participants involved in the communication. Hence, the contributions of the proposed scheme are:
-
We have proposed a novel distributed dynamic multistage authenticated key agreement scheme to achieve the illustrated security problems. The proposed scheme provides secure authentication between SM, NANG, and SCADA control server in a distributed manner, which means the authentication of SM, NANG, and SCADA control server does not depending upon any third party.
-
The proposed scheme achieves the authentication in a fully hierarchical manner which is suitable for smart grid smart meter communication architecture.
-
The proposed security scheme is formally proved in the CK - model. The scheme is simulated using AVISPA tool to verify the security against all active attacks.
-
The proposed scheme’s efficiency analysis has been made, considering its computation, communication, and functional costs. The computed results are compared with the other related schemes.
Related work
Authentication is a fundamental security solution and it has been extensively studied in various application areas. In smart grid smart meter communication, several authentication schemes have been proposed by numerous researchers. Even after the schemes are developed for specific architecture or application, there may be some similarities observed in terms of authentication factors, cryptographic operation, and message communication (Abbasinezhad-Mood, Ostad-Sharif & Nikooghadam, 2019). In this article, we only reviewed recent and relevant literatures, for the most part, authentication which focuses on the network architecture which includes SM, NAN, and SCADA control server. Wu & Zhou (2011) proposed an anonymous key distribution scheme for the smart grid. This scheme mainly combines the symmetric key and elliptic curve public key techniques. In the scheme, the symmetric key was based on the Needham-Schroeder authentication protocol. Wu & Zhou (2011) claimed that the proposed scheme effectively resists the man-in-the-middle attack and the replay attack. Later, Xia & Wang (2012) analysed Wu & Zhou’s (2011) scheme and identified the scheme is vulnerable to man-in-the-middle attack. To overcome the identified attack, Xia & Wang (2012) proposed a key distribution scheme. Here, the authors used a trusted third party to manage the key distribution for the smart meter and the service provider.
Nicanfar et al. (2013) proposed an efficient mutual authentication scheme. This scheme was developed to authenticate the entities that present outside of the home area network. Nicanfar et al. (2013) assumed that the authenticating participants are a smart meter and authentication server. From this literature, Nicanfar et al. (2013) also proposed a key management protocol based on identity cryptography for secure smart grid communications using the public key infrastructure. Li et al. (2013) proposed a Merkle-Tree-Based authentication scheme for secure smart grid communication. This article is more focused on eliminating message injection, message analysis, message modification, and replay attacks during communication.
Tsai & Lo (2015) reviewed Xia & Wang’s (2012) authentication scheme and identified that Xia & Wang (2012) scheme does not support smart meter anonymity and perfect forward secrecy. To overcome the identified weaknesses, Tsai & Lo’s (2015) proposed a key distribution scheme for smart grid environments. The scheme was proposed including properties of bilinear pairings. Importantly, Tsai & Lo’s (2015) scheme needed a trusted third party to distribute the private keys for smart meters and smart grid during registration. Later, Odelu et al. (2016) reviewed Tsai & Lo’s (2015) scheme and found that the scheme can reveal the smart meter’s secret credentials when the secret key has been revealed. To overcome the identified security weakness, Odelu et al. (2016) proposed a new authenticated key agreement scheme based on bilinear pairings for the smart grid. Like Tsai & Lo (2015) scheme, Odelu et al. (2016) utilized trusted third party to handle the private keys.
Further, Mahmood et al. (2016) proposed a hybrid Diffie-Hellman based lightweight authentication scheme using AES and RSA cryptography. This scheme was focused on achieving authentication between building area networks (BAN) and smart meters. The objective of the scheme was to avoid replay attack during authentication. Wazid et al. (2017) proposed a three-factor user authentication scheme for a renewable energy-based smart grid environment. Here, the objective was to authenticate vehicle user who wants to charge his/her electric vehicle battery. In this scheme, even though there are multiple authorities involved, authentication can be possible only between user and smart meter. Also, Wazid et al.’s (2017) scheme is dependent on trusted authority for smart meter registration.
Mahmood et al. (2018) proposed a lightweight ECC-based authentication scheme for smart grid communication. The aim of the scheme is to authenticate two registered users communicating in the environment. In this scheme, the trusted third party was responsible to generate preliminary parameters like selecting elliptic curve, random base point, one-way hash functions, secret key, and so on. Mahmood et al.’s (2018) scheme was also aimed to eliminate the trade-off between performance and security in smart grid communication where the scheme should provide high security with high performance. Further Abbasinezhad-Mood & Nikooghadam (2018) analyzed Mahmood et al.’s (2018) scheme and identified that the scheme cannot provide the perfect forward secrecy. Also identified that the private key of users and shared session keys can be easily compromised with an adversary. To overcome the identified weaknesses, Abbasinezhad-Mood & Nikooghadam (2018) proposed elliptic curve cryptography based lightweight authentication scheme for smart grid communications. Mahmood et al.’s (2018) scheme was also reviewed by Chen et al. (2019) and identified that the scheme could not provide the perfect forward secrecy and private key privacy. Also, the authors analyzed Abbasinezhad-Mood & Nikooghadam’s (2018) scheme and identified that the scheme is vulnerable to the replay attack. To withstand the identified weaknesses, Chen et al. (2019) proposed a bilinear map pairing-based authentication and key establishment scheme.
Zhang et al. (2019) proposed a lightweight anonymous authentication and key agreement scheme for the smart grid. This scheme allows the smart meter and the service provider to authenticate each other. The authentication scheme does not follow any hierarchical network architecture which minimizes the system applicability. Ma et al. (2019) proposed the eye-movement and iris recognition based portable remote authentication for the smart grid. It was a biometrics-based remote operator authentication scheme that uses the record of eye-movement trajectory and randomly selected iris image for authentication.
Recently, Moghadam et al. (2020) proposed a lightweight key management protocol for secure communication between substation and data center in smart grids. The scheme was based on hash functions and private keys. Irshad et al. (2020) proposed a message authentication scheme for secure communications between HAN gateway and BAN gateway in smart grids. Aghapour et al. (2020) proposed a broadcast authentication scheme for smart grid communications which uses hash functions and private key. Here, the authentication was to be done between the NAN gateway and the smart meter. Sadhukhan et al. (2020) proposed a privacy-preserving authentication scheme for smart-grid communication using elliptic curve cryptography. Here, the scheme can authenticate HAN gateway and BAN gateway in smart grids. This scheme needs a trusted third party to generate credentials, keys, and hash functions. Wu et al. (2021) reviewed Chen et al.’s (2019) scheme and identified the known session-specific temporary information attack where adversary can get the information of random nonce which needed to compute the session key. Also, Wu et al. (2021) identified that Chen et al.’s (2019) scheme is vulnerable to impersonation attack. To overcome identified weaknesses, Wu et al. (2021) proposed an improved pairing-based authentication scheme. The proposed scheme, depended upon a trusted third party to generate secret keys, cyclic groups, and hash functions.
From the above literature study we can observe that (i) most of the authentication schemes have security flaws and their improvements are also show some possible attacks. (ii) Many schemes can perform authentication either between the smart meter and NAN gateway or gateway and SCADA center. (iii) Also, the authentication schemes that implemented to the hierarchical network are dependent upon a trusted third party. Therefore, It is vary much necessary to propose an authentication scheme that can mutually authenticate smart meter, NAN gateway, and SCADA center without involvement of any third party. Hence, we have proposed a novel multistage distributed authentication scheme for smart grid communication.
The rest of the article is assembled as follows. “System Model” presents the system model used to propose the authentication scheme. “Cryptographic Preliminaries” discusses the necessary cryptographic preliminaries to understand the scheme. “The Proposed Scheme” illustrates the proposed multi-stage authentication scheme for smart meter communication. This section includes a detailed explanation of the steps of authentication in each phase. Further, “Cryptanalysis of the Proposed Scheme” presents the cryptanalysis of the proposed scheme. Here, we proved the data confidentiality, sensitivity and the security provided in the proposed scheme. The formal security verification of the proposed scheme based on the CK adversary model is illustrated in “Formal Security Proof”, followed by the results of formal security verification using AVISPA are presented in “Result of Formal Security Verification Using Avispa Tool”. “Efficiency Analysis” discusses the proposed scheme’s efficiency analysis by comparing result computation cost (“Computation Cost Analysis”) and communication cost (“Communication Cost”) of the proposed scheme with the other related schemes. This section also gives the comparison result of the essential functionalities (“Functional analysis”) in smart meter communication. Finally, the article depicts the concluding remarks.
System model
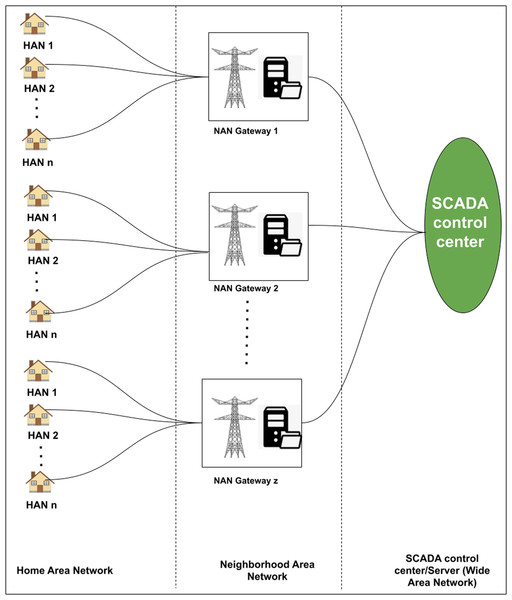
In this section, we present the system model which involves key components towards a smart meter communication between the consumers and SCADA control centres. As discussed in the “Introduction”, the system model described in the article is from the data communications point of view. The active participants are Smart Meter (SM), Home Area Network (HAN), Neighborhood Area Network Gateway (NANG) and SCADA control center/Server. These participants are well connected in a hierarchical manner. In the considered system architecture, HAN has been considered as the bottom layer. Within a HAN, home appliances are connected to a Smart Meter (SM). The purpose of SM is to collect the aggregated consumption (e.g., dishwasher, electric oven, etc) and generation (e.g., solar PV) profiles of the home devices. The collected data can be transferred to the SCADA control center/Server or smart grid (SG) for data storage and analysis. The communication happens via NANG that has been considered as the middle layer of the system. The complete system architecture is presented in Fig. 1.
Figure 1: Proposed architecture of the system model.
Cryptographic preliminaries
This section discusses the cryptographic preliminaries necessary to understand the proposed scheme. The necessary encryption/decryption operations are done using Elliptic Curve Cryptography (ECC). The security strength of ECC relies heavily on the hardness of solving the elliptic curve discrete logarithm problem (ECDLP). Compared to any other public-key cryptosystems, ECC can provide significant security strength to any communication system with less key size (Hancock, 2001). This property reduces the algorithmic computational cost and makes the protocol more lightweight.
Elliptic curve cryptography: The equation of the elliptic curve Ep(a, b) over Fp (p > 3 and is a large prime number) is defined as y2 mod p = (x3 + ax + b) mod p where (4a3 + 27b2) mod p = 0; x, y, a, b ∈ [0, p − 1]. Any points (x, y) ∈ Ep(a, b) are denoted as E(Fp) = {(x, y) : x, y in Fp satisfy where is a point at infinity. The point multiplication is computed by repeated addition as k.P = P + P + P + ….. + P K times (Koblitz, 1987).
Elliptic Curve Discrete Logarithm Problem(ECDLP): An elliptic curve E defined over a finite field GF(q) and two points P, Q ∈ E, it is hard to find an integer x ∈ Zp* such that Q = xP.
Elliptic Curve Diffie Hellman (ECDH): Elliptic Curve Diffie Hellman (ECDH) key exchange is the the classical Diffie-Hellman key exchange which exchanges secret information or secure keys between two parties. The keys are exchanged between A and B as follows.
System selects an elliptic curve Ep over the prime finite field Fp where p is a large prime number and select a point on elliptic curve P of order n. The algorithm is as follows.
-
A generates a random number kA in the interval [1, n − 1] and performs a scalar multiplication QA = kA × P Then, sends QA to B
-
B also generates a random number kB and computes QB = kB × P by scalar multiplication in the same way as described above and sends QB to A.
-
After receiving QB from B, A computes K1 = kA × QB. Similarly, B receives QA from A and computes K2 = kB × QA.
-
A and B shares K1 and K2 between them. Thus, two entities exchanges the keys securely.
The proposed scheme
This section presents the proposed novel distributed dynamic multistage authenticated key agreement scheme for the smart grid. The proposed scheme contains three phases (1) Initialization phase, (2) Registration phase and (3) Authentication phase. The notations used throughout the scheme are presented in Table 1.
| Notations | Descriptions |
|---|---|
| SGi | SCADA control center/server |
| SMi | Smart meter |
| Ep | Elliptic curve of order p |
| Fp | Finite field |
| NANGi | Neighborhood area network gateway |
| P | Point on elliptic curve Ep |
| s, Ppub | Private/public key pair of SGi where Ppub = s.P |
| PWi | Password of Ui |
| + | Bitwise XOR operator |
| || | Concatenation operator |
| h0(.), h1(.), h2(.) | One-way hash functions |
| T1, T2, T3, T4 | Timestamps generated by SMi, NANGi, SGi |
Initialization phase
To fully describe the proposed scheme, the process of system initialization is explained first. The initialization has to be done while deploying the system. It includes selecting an elliptic curve, hash functions, public and private keys necessary to perform encryption/decryption, and hashing operation throughout the entire scheme.
SGi choose an elliptic curve Ep over the finite field Fp where p is a large prime number. SGi also selects an elliptic curve point P of order n and one way hash functions . Further SGi picks the private key x and computes the public key Ppub = x.P. Finally, SGi publishes the parameters {Ep, P, Fp, h0(.), h1(.), h2(.), Ppub}.
Registration phase
The registration phase includes steps to register participants (e.g., SMi, NANGi, etc.), which take part in the system. This phase includes the registration of Neighborhood Area Network gateway NANGi and smart meter SMi. The details of NANGi and SMi registration have been presented below.
NAN gateway registration phase
In the proposed scheme, NANGi registration is done with a SCADA control center/server. The steps involved in the NANGi registration have been illustrated as follows:
-
NANGi selects NIDi, bj and computes Ai = h0(NIDi ||bj)
-
Sends the registration request message {NIDi, Ai} to the SGi.
-
SGi receives the request message, generates the random number e and computes
mi = h0(s ||e),
Vn = h0(mi ||Ai).Ppub and
Hn = h0(Vn|| NIDi)
-
SGi stores Hn into the database and sends Vn to the NANGi. NAN gateway receives Vn and stores {NIDi, bj, Vn} into its database. The registration phase of NAN gateway has been presented in the Table 2.
| NAN gateway | SCADA control center/server |
|---|---|
| Selects NIDi, bj | |
| Computes Ai = h0(NIDi|| bj) | |
| Sends {NIDi, Ai} | |
| {NIDi,Ai} −−−−→ |
|
| Receives message and generates the random number e | |
| Computes mi = h0(s|| e) | |
| Vn = h0(mi ||Ai).Ppub and | |
| Hn = h0(Vn ||NIDi) | |
| Stores Hn into the database and sends Vn to the NANGi | |
| {Vn} ←−− |
|
| Receives Vn and stores {NIDi, bj, Vn} |
Smart meter registration phase
The registration of the SMi is with NANGi. The registration of SMi has been presented below:
-
SMi selects MIDi, bi, computes Aj = h0(MIDi ||bi) and sends the registration request message {MIDi, Aj} to the NAN gateway.
-
NANGi receives the request message and computes
Hn = h0(Vn ||NIDi),
Vm = h0(Hn ||Aj).Ppub and
Hm = h0(Vm|| MIDi)
-
NANGi stores Hm into the database and sends Vm to the SMi. Smart Meter receives Vm and stores {MIDi, bi, Vm} into SMi. The Smart meter registration phase has been presented in Table 3.
| Smart meter | NAN gateway |
|---|---|
| MIDi, bi | |
| Computes Aj = h0(MIDi bi) | |
| Sends {MIDi, Aj} | |
| {MIDi,Aj} −−−−−→ |
|
| Receives message | |
| Computes Hn = h0(Vn ||NIDi), | |
| Vm = h0(Hn ||Aj).Ppub and | |
| Hm = h0(Vm|| MIDi) | |
| Stores Hm into its database and sends Vm to the SMi. | |
| {Vm} ←−− |
|
| Receives Vm and stores {MIDi, bi, Vm} into SMi. |
Authentication phase
The authentication phase is performed between SMi, NANGi, and SGi. Here, SMi and SGi mutually authenticate through NANGi. Table 4 presents the authentication phase of the proposed scheme. The steps involved in this phase are as follows:
-
Smart meter SMi generates a random number w and computes
Csm = w.Ppub ⊕ h0(Vm ||MIDi)
CIDi = h1(w.Ppub|| T1) ⊕ bi
C1 = h1(CIDi ||bi ||w.Ppub)
-
Further SMi send login request message M1 = {Csm, CIDi, C1, T1} to NAN gateway.
-
NANGi receives the message M1 sent by SMi and checks the validity. To verify the freshness of the received message, NANGi takes its current timestamp T2 and checks that whether T2 − T1 ≤ δ T or not. Also, NANGi confirms that between the time (T1 + δ T) and (T1 − δ T) there were no other requests which contains same parameters of M1 has not received. If these conditions are not true, then the system rejects the request message and drops the session.
-
NANGi computes the following after receiving the login request message:
w.Ppub = Csm ⊕ Hm
bi = h1(w.Ppub ||T1) ⊕ CIDi
Cnan = Csm ⊕ Hm ⊕ h0(Vn ||NIDi)
RIDs = h1(Cnan h0(Vn ||NIDi)) ⊕ bj
C2 = h1(C1 ||T2 ||Cnan bj)
-
NANGi Sends {CIDi, C2, Cnan, RIDs, T2, T1} to the server.
-
SGi receives the request message sent by NAN gateway and checks its validity to make sure that the request is made recently. SGi takes its present timestamp T3 and checks whether T3 − T2 ≤ δ T. If the condition does not satisfy, then SGi rejects the received message and drops the session. If not, SGi begins the authentication process.
-
Once the request message accepted by the sever, it starts authenticating it. To do that SGi computes the following: w.Ppub = Cnan ⊕ Hn
bi = h1(w.Ppub|| T1) ⊕ CIDi
bj = h1(Cn ||Hn) ⊕ RIDs
C1 = h1(CIDi ||bi ||w.Ppub)
C2 = h1(C1 ||T2 ||Cnan ||bj)
-
Server compares C2 with received C2. If both are equal then the server completes the authentication of SMi and begins the mutual authentication.
-
To perform mutual authentication, server first generates the random number y and computes Cs = y.Ppub ⊕ h2(Hn)
SKs = h2(y.Ppub ||w.Ppub ||bi ||bj )
C3 = h2(SKs ||t3 ||y.Ppub)
-
SGi sends a mutual authentication message M2 = {C3, Cs, T3} to NAN gateway. NANGi receives M2 and computes y.Ppub = Cs ⊕ h2(h0(Vn ||NIDi))
RIDm = h2(Cm|| Hm ) ⊕ bj
Cm = Cs ⊕ Hm ⊕ h0(Vn ||NIDi)
SKN = h2(y.Ppub|| w.Ppub ||bi ||bj )
C4 = h2(C3 ||T4 ||Cm ||bj)
Sends {Cs, T3, C4, Cm, T4, RIDm} to the SMi
-
Smart meter receives mutual authentication message from NAN gateway and computes
y.Ppub = Cs ⊕ h0(Vm ||MIDi)
bj = h1(Cm h0(Vm ||MIDi)) ⊕ RIDm
SKM = h2(y.Ppub ||w.Ppub ||bi ||bj )
C3 = h2(SKM ||T3 ||y.Ppub )
C4 = h2(C3 ||T4 ||Cm ||bj)
-
SMi Compares C4 with received C4 if both are equal smart meter, NAN gateway, and the server establishes the connection successfully.
-
Further communications will be done through the shared session keys. The session keys are For smart meter, SKM = h2(y.Ppub ||w.Ppub ||bi ||bj)
For NAN gateway SKN = h2(y.Ppub ||w.Ppub ||bi ||bj )
For Server SKs = h2(y.Ppub ||w.Ppub ||bi ||bj ).
| Smart meter | NAN gateway | SCADA control center/server |
|---|---|---|
| Generates w and computes | ||
| Csm = w.Ppub ⊕ h0(Vm ||MIDi) | ||
| CIDi = h1(w.Ppub|| T1) ⊕ bi | ||
| C1 = h1(CIDi ||bi||w.Ppub) | ||
| Sends M1 = {Csm, CIDi, C1, T1} to NAN gateway. | ||
| {M1 = Csm,CIDi,C1,T1} −−−−−−−−−−−−−−→ |
||
| Receives the message sent and checks T2 − T1 ≤ δ T. | ||
| Computes | ||
| w.Ppub = Csm ⊕ Hm | ||
| bi = h1(w.Ppub|| T1) ⊕ CIDi | ||
| Cnan = Csm ⊕ Hm ⊕ h0(Vn ||NIDi) | ||
| RIDs = h1(Cnan ||h0(Vn ||NIDi)) ⊕ bj | ||
| C2 = h1(C1|| T2|| Cnan ||bj) | ||
| Sends {CIDi, C2, Cnan, RIDs, T2, T1} to the SGi. | ||
|
CIDi,C2,Cnan,RIDs,T2,T1 −−−−−−−−−−−−−−−→ |
||
| Receives the request message and checks whether T3 − T2 ≤ δ T. | ||
| Computes the following: | ||
| w.Ppub = Cnan ⊕ Hn | ||
| bi = h1(w.Ppub|| T1) ⊕ CIDi | ||
| bj = h1(Cn|| Hn) ⊕ RIDs | ||
| C1 = h1(CIDi|| bi ||w.Ppub ) | ||
| C2 = h1(C1|| T2 ||Cnan ||bj ) | ||
| Checks C2 ? = C2 If both are equal then. | ||
| Generates y and computes | ||
| Cs = y.Ppub ⊕ h2(Hn) | ||
| SKs = h2(y.Ppub|| w.Ppub ||bi ||bj ) | ||
| C3 = h2(SKs|| t3 ||y.Ppub) | ||
| Sends M2 = {C3, Cs, T3}. | ||
| {M2 = C3,Cs,T3} ←−−−−−−−−−− |
||
| Receives M2 and computes | ||
| y.Ppub = Cs ⊕ h2(h0(Vn ||NIDi)) | ||
| RIDm = h2(Cm|| Hm ) ⊕ bj | ||
| Cm = Cs ⊕ Hm ⊕ h2(h0(Vn|| NIDi)) | ||
| SKN = h2(y.Ppub ||w.Ppub ||bi ||bj ) | ||
| C4 = h2(C3 ||T4 ||Cm ||bj) | ||
| Sends {Cs, T3, C4, Cm, T4, RIDm} to the SMi | ||
| {Cs,T3,C4,Cm,T4,RIDm} ←−−−−−−−−−−−−−− |
||
| Receives mutual authentication message and computes | ||
| y.Ppub = Cs ⊕ h0(Vm|| MIDi) | ||
| bj = h1(Cm|| h0(Vm|| MIDi)) ⊕ RIDm | ||
| SKM = h2(y.Ppub ||w.Ppub ||bi ||bj ) | ||
| C3 = h2(SKM ||T3 ||y.Ppub ) | ||
| C4 = h2(C3 ||T4 ||Cm ||bj) | ||
| Smart meter session key | NAN Gateway session key | Server session key |
| SKM = h2(y.Ppub ||w.Ppub ||bi ||bj ) | SKN = h2(y.Ppub ||w.Ppub ||bi ||bj ) | SKs = h2(y.Ppub ||w.Ppub ||bi ||bj ) |
Cryptanalysis of the proposed scheme
This section presents the cryptanalysis of the proposed multistage authentication scheme. This analysis helped us to prove the sensitivity of the obtained results where stored and communication parameters does not impact on the systems privacy and the security.
Resiliency against replay attack
Resiliency against replay attacks can be possible only when the server verifies the freshness of the login message before beginning the authentication. In the proposed scheme, a timestamp has been used to check the validity of the login request message. Suppose a participant receives the message contains timestamp T, then the participant takes its current timestamp T and checks the condition T′ - T ≤ δT. If this condition is satisfied, the next step would be to proceed else participant drops the session.
Let us assume that adversary steals the previous successfully authenticated login request message {Csm, CIDi, C1, T1} sent from SMi to NANGi and {CIDi, C2, Cnan, RIDs, T2, T1} sent from NANGi to SGi. Attacker trying perform replay attack by resending stolen login request message. Here, both NANGi and SGi first verifies the message freshness by checking the validity of the time stamp. To verify the freshness, NANGi takes its current timestamp T2 and checks whether T2 − T1 ≤ δ T or not. Also, NANGi confirms that there were no other requests with parameters have been received between the time (T1 + δ T) and (T1 − δ T). If the timestamp T1 is not modified in the login request message, the condition T2 − T1 ≤ δ T will definitely fails and NANGi drops the session. This procedure also happens when SGi receives login request message from NANGi. Therefore, the proposed scheme resists the replay attack.
Resiliency against insider attack
The proposed distributed multistage authentication scheme does not store all the information in a single system/server. The registration of SMi is with NANGi and the registration of NANGi will be done by SGi. This process distributes the necessary credentials to SMi, NANGi and SGi. To perform any attack, insider must know parameters stored in other two participants SMi and NANGi. Hence the proposed scheme ensures resiliency against insider attack.
Resiliency against impersonation attack
When the communication has taken place in an open channel, the attacker can intercept the sent/received messages and perform an impersonation attack. Assume that an attacker intercepts the login and authentication messages {Csm, CIDi, C1, T1}, {CIDi, C2, Cnan, RIDs, T2, T1}, {C3, Cs, T3}, and {Cs, T3, C4, Cm, T4, RIDm} to perform impersonation attack. In the proposed scheme, computation of the communication parameters are depending upon the random nonces w, y and the parameters {NIDi, bj, Vn} stored in SMi. Since the random nonce and stored parameters do not communicate in the open channel as plain text, attacker cannot get the knowledge of it. Therefore cannot modify the login request parameters to impersonate the user.
Resiliency against man-in-the-middle attack
A man-in-the-middle attack can be possible when the adversary successfully authenticates with the server or calculate the session key correctly by intercepting communication messages. In the proposed scheme, to mitigate this attack we have applied two types of mechanism. First and foremost the communication message parameters of the proposed scheme are computed depending upon the generated random nonces w, y. Usage of random nonce prevents the impersonation and preserves the secrecy of the session key. Secondly, a timestamp has been used to check the validity of the login request message in every session. As said in “Resiliency Against Replay Attack”, checking the message freshness resists the replay attack. Hence, the attacker cannot authenticate himself by intercepting the communication messages.
Provides perfect forward secrecy
In the proposed scheme, session key calculated by SK = h2(y.Ppub ||w.Ppub ||bi ||bj). An adversary cannot compute SK by intercepting the mutual authentication messages {C3, Cs, T3}, and {Cs, T3, C4, Cm, T4, RIDm}. An attacker must have the knowledge of random nonces w, y, bi and bj to calculate SK. The proposed scheme cannot share random nonce as plain text over the public channel. Therefore to calculate SK, an adversary has to guess all random nonces at the same time, which is not possible. Hence the proposed scheme provides perfect forward secrecy.
Provides device anonymity
In the proposed scheme, device anonymity is preserved while login into the system. A dynamic identity CIDi = h1(w.Ppub ||T1) ⊕ bi has been calculated every session. The computation of the CIDi is depending on the random nonce w. Therefore the dynamic identity is different at every login attempt. Hence the proposed scheme provides reveal the device identity MIDi.
Provides data confidentiality
In the proposed scheme, the confidentiality of the communicated messages has been preserved even after authentication. The secrecy of the message after authentication can be achieved by the session key. In the proposed scheme, if the attacker tries to steal any message communicated between SMi, NANGi and SGi cannot decrypt without SK. As explained in “Provides Perfect Forward Secrecy”, the session key cannot be compromised with the adversary. Moreover, during authentication, after successful verification of the login request SMi, NANGi and SGi will mutually authenticate each other and compute the session key. This creates a secure channel over an insecure environment. So, the communicated message remains confidential between SMi, NANGi and SGi.
From the cryptanalysis result of the proposed scheme it can be proved that the data confidentiality, sensitivity and the security has been achieved by resisting the possible attacks on the network.
Formal security proof
This section presents the formal security analysis to prove that the proposed scheme is secure against the adversary modeled in Odelu et al. (2016) and Tsai & Lo (2015) proposed by Canetti & Krawczyk (2001). According to this mode, adversary has full control over the transmission channel. Therefore can eavesdrop, intercept, alter the communication messages, and knows all the public parameters. The adversary cannot access the secret parameter directly but can construct queries to capture the information leakage.
Participants
A participant in the entity takes part in the authentication process. In the proposed scheme, there are three participants are involved in performing the authentication, which is named as SMi, NANGi, and SGi, where SMi is a smart meter, NANGi for the Neighborhood Area Network gateway, and SGi is the SCADA control center/Server. Each participant have multiple instances to run the scheme parallelly. The instances are represented as SMi, NANGi, and SGi, where ‘i’ represents the ith instance of the participants (Tsai & Lo, 2015).
Queries
In CK—model, adversary can construct the queries to perform the attacks. The possible queries made by , and the attacks committed with the constructed query are illustrated below:
-
Execute(SMi, NANGi, SGi): This oracle query construct the passive attacks by eavesdropping the successful execution done between the participants SMi, NANGi, SGi. Here, simulates the login and authentication phase and gets the messages communicated between the participants.
-
Send(SMi/NANGi/SGi, M): formulatess this query to perform active attacks. Adversary sends message to SMi/NANGi/SGi and receives the response from SMi/NANGi/SGi.Also, can intercept communication channel and modify the communicated messages and gets the reply in return.
-
EKeyReveal (SMi/SGi): This query allows adversary to obtain the session state ephemeral secret key information held by the instance SMi/NANGi/SGi.
-
SKReveal (SMi/SGi): This query allows adversary to get the session key held by the instance SMi/NANGi/SGi.
-
Corrupt (SMi/SGi): This query express the notion of perfect forward secrecy where long term secret key can be compromise with to get the session key on the oracle SMi/NANGi/SGi.
-
Test(SMi/SGi): This single query can be constructed by adversary at most once. It models the semantic security of the session. Here, returns the session key of SMi/NANGi/SGi or a random string with an equal bit length of the session key. This result is depending upon tossing a coin b. If b = 1, the adversary gets the original session key. Else gets a random string with the same length as the real session key.
Before presenting the security proof, it is necessary to describe some definitions, which are given below:
-
Partnering: Two entities are called to be partners when they are accepted and shared a commen session key. In the proposed scheme, SMi, NANGi and SGi are partners only if MIDi = NIDj = SIDk, and SKSMi = SKNANGi = SKSGi.
-
Freshness: It is related to the session key. Here, oracle constructs the session key. We can say that the constructed session key is fresh if the instance meets the following conditions.
-
When there is no Reveal query is done by SMi, NANGi and SGi, sission key SKi should not be null.
-
Send(SMi, M), Send(NANGi, M) or Send(SGi, M) should be asked after modelling the Currupt query
-
Semantic Security: The goal of semantic security is to guess the bit ′b′, which is involved in the Test(SMi/SGi) query. Consider an event S() that the adversary guess the bit b correctly. Let SMi, NANGi and SGi oracles are considered as partners when authenticating each other and share a common session key. The adversary’s goal is to differentiate the session key from a random key. can model many Test queries for SMi or SGi. Consider queries, for instance, SMi. Further, SMi toss a coin b. If b=1, the adversary gets the original session key. Else A gets a random string with the same length as the real session key.
Let Pr[S] denotes the game-winning probability of . The advantage of the Adversary A against breaking the semantic security of the proposed scheme is AdvAKEP (A) = |2Pr[Succ] − 1|.
Computational problem
It is essential to describe the details of the computational problem where the security proof relies upon.
-
Elliptic curve computational Diffie-Hellman problem (ECDH): Let P, xP, yP ∈ Ep where , then it is hard to compute xyP in polynomial time without knowledge of x or y.
-
Elliptic curve discrete logarithm problem (ECDLP): It says that when G ∈ Ep(x, y) of order n and G = kP ∈ Ep(x, y), it is computationally infeasible to compute k in polynomial-time.
-
Reversing One way Hash function: Let H(.) is a one way hash function, then it is computationally hard to get x from H(x). Also it is hard to find x where H(x) = H(x).
Security proof
Theorem 1 Let Ep over the finite field Fp with a large prime number p and be the finite set of password. Consider is a adversary running in a polynomial time to perfom security attack on the proposed scheme. Let AdvAKESC is the advantage of the against the proposed scheme and advantage of that solves ECDH in Ep. While performing the attackes over the proposed scheme makes qsend Send queries, qhsh hash oracles, and qexe Execute queries within the time t. The advantage of will be
Proof: The queries constructed by has been presented in Tables 5 and 6. Based on the queries build by , the proof is presented. The sequence of experiments from Experiment0 to Experiment4 defines the proof of the proposed authenticaion scheme. Let Succn denotes the event that occures after the Test query made by adversary while guessing the bit b correctly.
| For a hash oracle h(i, q) where i = 0, 1, 2 if (i, q, h) ∈ Lh Return h |
| Else, Choose h and add to Lh as (i, q, h) |
| For Execute (SMi, NANGi, SGi) query |
| Return (Csm, CIDi, C1, T1), (CIDi, C2, Cnan, RIDs, T2, T1), (C3, Cs, T3), (Cs, T3, C4, Cm, T4, RIDm) |
| For EKeyReveal (SMi/SGi) query return Ephermal Secret key w from SMi and y from SGi |
| For SKReveal (SMi/SGi) query return static private key s from SMi or SGi |
| For Test(SMi/NANGi/SGi) query |
| For Corrupt() query |
| If P = Pi |
| Return RPWi or Ai |
| Else if P = S |
| Return Ai |
| For Send (Pi, Start) query |
| Generate random number w and computes Csm = w.Ppub ⊕ h0(Vm|| MIDi), CIDi = h1(w.Ppub ||T1) ⊕ bi, |
| C1 = h1(CIDi ||bi ||w.Ppub), Return (Csm, CIDi, C1, T1). |
| For Send (Csm, CIDi, C1, T1) query |
| w.Ppub = Csm ⊕ Hm, bi’ = h1(w.Ppub ||T1) ⊕ CIDi Cnan = Csm ⊕ Hm ⊕ h0(Vn|| NIDi) |
| RIDs = h1(Cnan ||h0(Vn ||NIDi)) ⊕ bj C2 = h1(C1 ||T2 ||Cnan ||bj) Return (CIDi, C2, Cnan, RIDs, T2, T1) |
| For Send (CIDi, C2, Cnan, RIDs, T2, T1) query |
| w.Ppub’ = Cnan ⊕ Hn bi’ = h1(w.Ppub ||T1) ⊕ CIDi bj = h1(Cn ||Hn) ⊕ RIDs |
| C1’ = h1(CIDi ||bi’ ||w.Ppub) C2’ = h1(C1’||T2 ||Cnan ||bj) |
| If C2’ = C2 |
| Generate random number y and computes |
| Cs = y.Ppub ⊕ h2(Hn) SKs = h2(y.Ppub ||w.Ppub’ ||bi‘||bj’) C3 = h2(SKs t3 y.Ppub) |
| Return (C3, Cs, T3) |
| For Send (C3, Cs, T3) query |
| y.Ppub = Cs ⊕ h2(h0(Vn ||NIDi)) RIDm = h2(Cm ||Hm ) ⊕ bj Cm = Cs ⊕ Hm ⊕ h2(h0(Vn ||NIDi)) |
| SKN = h2(y.Ppub ||w.Ppub’ ||bi’|| bj’ ) C4 = h2(C3 ||T4 ||Cm ||bj) |
| Return (Cs, T3, C4, Cm, T4, RIDm) |
| For Send (C3, Cs, T3) query |
| y.Ppub’ = Cs ⊕ h0(Vm ||MIDi) bj’ = h1(Cm ||h0(Vm ||MIDi)) ⊕ RIDm SKM = h2(y.Ppub’|| w.Ppub ||bi ||bj’ ) |
| C3’ = h2(SKM ||T3 ||y.Ppub’) C4’ = h2(C3’|| T4 ||Cm ||bj) |
| If C4 = C4 SMi, NANGi and SGi Else Terminated |
Experiment 0: This experiment corresponds to the real experiment in the random oracle model. By the definition, we have
Experiment 1: This experiment simulates H0, H1, H2 by maintaining two hash list Lh and Lh. Here, Lh stores the oracle for H0, H1, H2 and Lh is for queries asked by . The simulation queries are presented in Table 5. From the simulation, it is observed that the transcript distribution of Experiment 0 and Experiment 1 are indistinguishable. Hence we have
Experiment 2: This experiment simulates the oracle of Experiment 1 except the collisions occurs in the transcripts and hash queries by the adversary. In other words, the experiment aims to avoid the collision occurring in C1, C3, Csm and Cs. The Experiment 1 and Experiment 2 are indistinguishable until the collision takes place. Since, w and y are randomly chosen, according to the birthday paradox, probability of the collision occurrence is at most (qsend + qexe)2/2n. Also, the probability of the occurrence of the collision in the output of the hash oracle is at most (qhsh)2/2k. Hence we have
(1)
Experiment 3: This experiment aborts the scheme if the adversary succeeds in guessing the authentication value C1 and C3 without making the hash query. Since, Experiment 3 and Experiment 2 are indistinguishable unless smart grid SGi rejects C1 or smart meter SMi rejects the authentic value C3. Hence we have
(2)
Experiment 4: This experiment considers the session key security. cannot obtain the previous session key when has {w, y, s, P} but not (w, s, P) and (y, s, P). The aim of is to compute the session key SKi = h2(y.s.P w.s.P bi bj) by asking Execute(SMi, NANGi, SGi) queries and corresponding hash queries in the four cases.
case 1: queries Corrupt (SMi) and Corrupt (SGi) to get static private key s to compute the session key SKi. To derive the session key should get w and y.
case 2: queries EKeyReveal (SMi) and EKeyReveal (SGi) to get ephermal private key w and y. But will not get the static key s.
case 3: queries EKeyReveal (SMi) and Corrupt (SGi) and returns w and s. But will not get y.
case 4: queries Corrupt (SMi) and EKeyReveal (SGi) and returns y and s. But will not get x.
In all the above four cases, will get insufficient information to compute SKi without solving the ECDH. The Experiment 3 and Experiment 4 are indistinguishable until the ECDH assumption is true. Hence we have
(3)
Now, has to guess b to achieve the experiment by the Test query. It is clear that Pr[Succ4] = 1/2.
Result of formal security verification using avispa tool
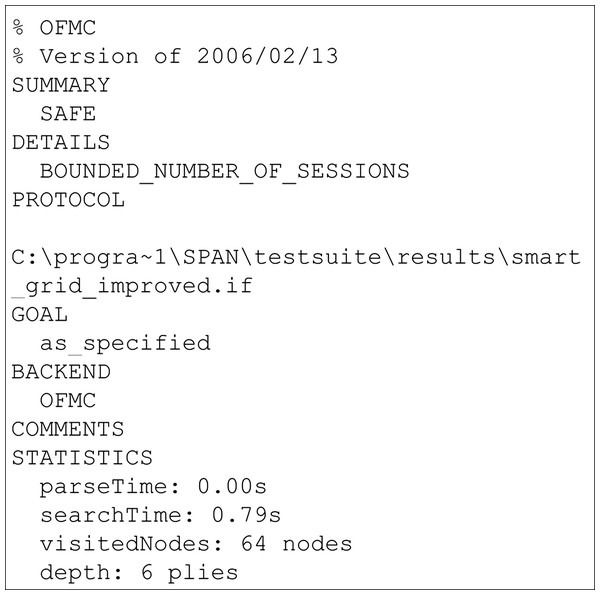
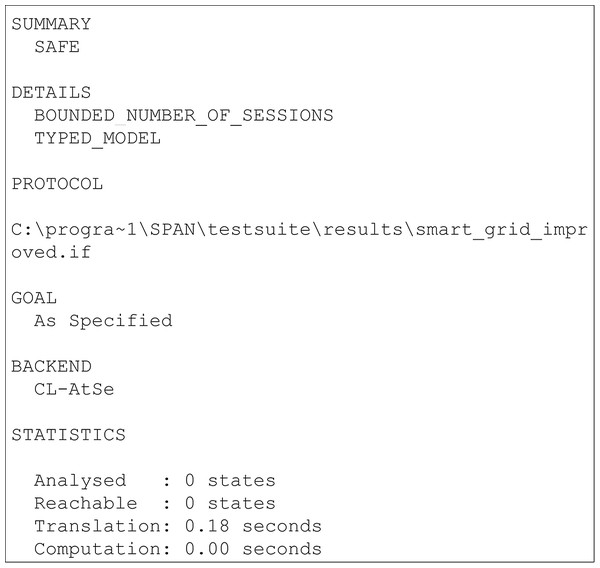
The results of the security verification using the AVISPA tool are presented in this section. AVISPA is a protocol analysis tool that provides a platform to implement the schemes and verify its security. To implement schemes, AVISPA uses High-Level Protocol Specification Language (HLPSL). It is a role-based language where every participant in the network plays a role during the execution. In HLPSL, the Doley-Yao model has been used to build the intruder. During the execution of schemes, the HLPSL code is converted into an Intermediate Format (IF) through a translator called hlpsl2if. Further, the translated IF is read by backends and analyses security goals. There are four backends are used in AVISPA used for security analysis known as On-the-fly Model-Checker (OFMC) (Basin, Mödersheim & Vigano, 2005), CL-AtSe (Constraint Logic-based Attack Searcher) (Turuani, 2006), SAT-based Model checker (Armando & Compagna, 2004) and Tree Automata based on Automatic Approximations for the Analysis of Security Protocols (TA4SP) (Boichut et al., 2004). If the scheme achieves all defined goals, then the output is given as SAFE else, the output will be UNSAFE.
The results of the security verification obtained from the AVISPA tool are presented in Figs. 2 and 3. The presented results are obtained through OFMC, and CLAtSe back ends. The other two backends SATMC and TA4SP, do not support the XOR feature. Hence the results were received as “Inconclusive”. Therefore the OFMC and CLAtSe results are considered and claimed that the obtained result is SAFE against the intruder. Hence, we can clearly say that the proposed scheme achieves all the specified goals and remains secure against all the attacks.
Figure 2: OFMC simulation result of proposed scheme.
Figure 3: CLAtSe simulation result of proposed scheme.
Efficiency analysis
This section focuses on the efficiency analysis of the proposed scheme. The analysis mainly focuses on calculating the computation and communication costs and comparing the result with related authentication schemes like Tsai & Lo (2015), Wazid et al. (2017), Odelu et al. (2016), Gope & Sikdar (2018), Kumar et al. (2018), Zhang et al. (2019), Ma et al. (2019), Wu et al. (2019), Li et al. (2019) and Khan, Kumar & Ahmad (2019).
Computation cost analysis
The proposed scheme’s computation cost has been calculated and compared with the other schemes. We have presented the required computation cost and estimated execution time of the proposed scheme in Smart meter, NAN gateway, and SCADA control center/Server. To measure the execution time, we have taken the results obtained by Gope & Sikdar (2018). According to the results presented by Gope & Sikdar (2018), the required execution time for one computational parameter on Smart meter, NAN gateway, and SCADA control center/Server is given in Table 7. The computational parameters are defined as follows: Th: The time for executing a one-way hash operation, Ts: The time for symmetric key encryption/decryption execution operation, Tmp: scalar multiplication operation of an elliptic curve, Ta: Point addition operation of an elliptic curve, Tb: The time to perform one bilinear pairing operation, Te: The time to complete the modular exponential operation, Tfe: The time to perform fuzzy extractor Gen(·)/Rep(·) operation, TPUF: The time to perform Operation of PUF circuit.
| Operation | SM i & NANG i | SG i |
|---|---|---|
| Th | 0.026 ms | 0.011 ms |
| Ts | 0.079 ms | 0.041 ms |
| Tmp | 5.9 ms | 2.6 ms |
| Te | 7.86 ms | 2.34 ms |
| Tb | 9.23 ms | 3.78 ms |
| TPUF | 0.12 ms | – |
| Tfe | 3.28 ms | 1.17 ms |
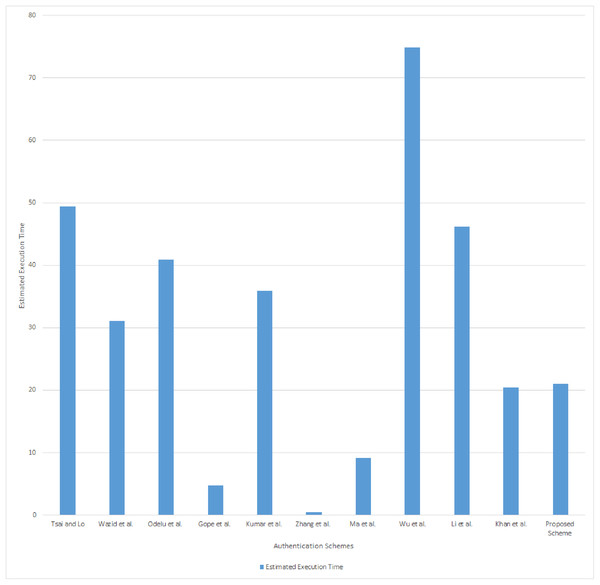
The computation cost analysis results are given in the Table 8 and the estimated execution time analysis is presented Fig. 4. The computation cost of the proposed scheme is the sum of the costs of SMi, NANGi, and SGi, which is 2Tmp + 12Th, 1Tmp + 12Th, and 1Tmp + 7Th, respectively. The total computation cost of the proposed scheme is 4Tmp + 32Th. Estimated execution time of the proposed scheme in the SMi and NANGi is (3 × 5.9 ms) + (24 × 0.026 ms) = 18.324 ms. The estimated execution time in the SGi side is (1 × 2.6 ms) + (7 × 0.011 ms) = 2.677 ms. The total estimated execution time of the proposed scheme is 21.001 ms.
| Schemes | SM i | NANG i | SG | Total | Expected time |
|---|---|---|---|---|---|
| Tsai & Lo (2015) | 4Tmp + Te + Th | – | 2Tb + 3Tmp + 1Te + 5Th | 2Tb + 4Tmp + 2Te + 6Th | 49.421 ms |
| Wazid et al. (2017) | 4Tmp + 2Teca + 5Th | – | 2Tmp + 1Tfe + 8Th | 6Tmp + 2Teca + 1Tfe + 13Th | 31.088 ms |
| Odelu et al. (2016) | 3Tmp + 1Te + 6Th | – | 2Tmp + 2Tb + 1Te + 6Th | 5Tmp + 2Te + 1Tb + 12Th | 40.882 ms |
| Gope & Sikdar (2018) | 1Tfe + 5Th + 1TPUF | – | 1Tfe + 6Th | 2Tfe + 11Th + 1TPUF | 4.766 ms |
| Kumar et al. (2018) | 3Tmp + 2Ts + 4Th | 3Tmp + 2Ts + 5Th | – | 6Tmp + 4Ts + 9Th | 35.875 ms |
| Zhang et al. (2019) | 1Ts + 7Th | – | 3Ts + 9Th | 4Ts + 16Th | 0.483 ms |
| Ma et al. (2019) | 1Tmp + 2Ts + 7Th | – | 1Tmp + 4Ts + 14Th | 2Tmp + 6Ts + 21Th | 9.158 ms |
| Wu et al. (2019) | 3Te + Tmp + 4Th | 5Te + Tmp + 4Th | – | 8Te + 2Tmp + 8Th | 74.888 ms |
| Li et al. (2019) | 2Te + Ts + 4Th | 3Te + Tmp + 4Th | – | 5Te + Ts + Tmp + 4Th | 46.198 ms |
| Khan, Kumar & Ahmad (2019) | 2Tmp + 1Tfe + 4Th | – | 2Tmp + 3Th | 4Tmp + 1Tfe + 7Th | 20.417 ms |
| Proposed | 2Tmp + 12Th | 1Tmp + 12Th | 1Tmp + 7Th | 4Tmp + 31Th | 21.001 ms |
Figure 4: Computation cost analysis.
Comparing the proposed scheme’s results with the other schemes presented in Table 8, we can observe that the proposed scheme’s computational cost and estimated execution time is higher than Gope & Sikdar (2018), Zhang et al. (2019), Ma et al. (2019), Khan, Kumar & Ahmad (2019) schemes and lesser than all other schemes. Unlike the proposed scheme, Gope & Sikdar (2018), Zhang et al. (2019), Ma et al. (2019) schemes will not mutually authenticates every participants involved in the communication. There are some architectural limitations where the scheme can be applied only when the smart meter is directly communicates with the smart grid. As discussed in “Introduction”, smart grid topology is split into several networks which contains several smart meters, NAN gateways, and SG. Therefore, the schemes of Gope & Sikdar (2018), Zhang et al. (2019), Ma et al. (2019) are not efficient for hierarchical model of smart grid communications. The estimated execution time of Khan, Kumar & Ahmad’s (2019) scheme also less than the proposed scheme. But the khan2019elliptic scheme was limited to authenticate smart meters and NAN gateway only. The proposed scheme computation cost and estimated execution time include the mutual authentication of a smart meter, NAN gateway, and smart grid. Also, the authentication of the proposed scheme has been achieved without involvement of any third party. Therefore the computation cost looks higher than the schemes of Gope & Sikdar (2018), Zhang et al. (2019), Ma et al. (2019), Khan, Kumar & Ahmad (2019). However, the proposed scheme overcomes all the security barriers presented in “Functional Analysis”, and achieves fully distributed multistage authentication.
Communication cost
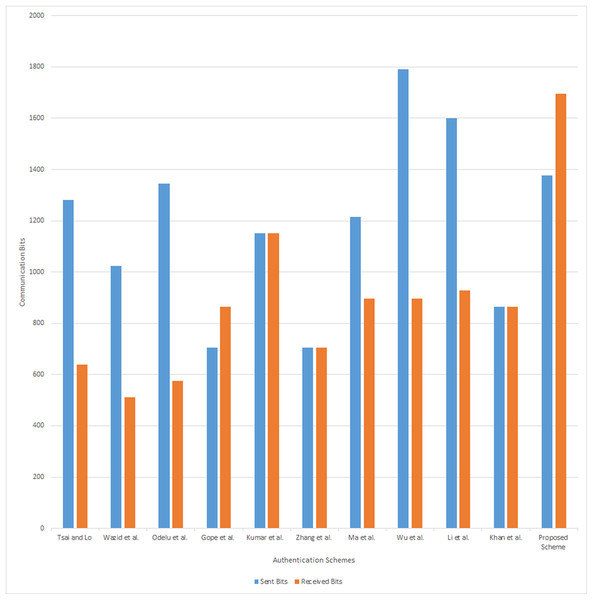
The communication cost of the proposed scheme is compared with the Tsai & Lo (2015), Wazid et al. (2017), Odelu et al. (2016), Gope & Sikdar (2018), Kumar et al. (2018), Zhang et al. (2019), Ma et al. (2019), Wu et al. (2019), Li et al. (2019) and Khan, Kumar & Ahmad (2019) schemes and presented in Table 9. It includes the cost of the communication parameters, transmitted in one complete session of the authentication phase. For consistency purpose, we assume that the length of the identity IDi and random number is 128 bits, the output size of hash functions H0 (.), H1 (), and H2 () is 160 bits, size of an elliptic curve point is 320 bits, the block size of symmetric encryption/decryption is 256 bits, size of bilinear pairing is bits, bits and a Timestamp is 32 bits. The authentication phase of the proposed scheme requires 320 + 160 + 160 + 32 = 672 bits, 160 + 160 + 160 + 160 + 32 + 32 = 704 bits, 160 + 320 + 160 + 32 = 672 bits, and 320 + 160 + 160 + 160 + 160 + 32 + 32 = 1074 bits, for the messages {Csm, CIDi, C1, T1}, {CIDi, C2, Cnan, RIDs, T1, T2}, {C3, Cs, T3}, and {Cs, T3, C4, Cm, T4, RIDm}. Hence, the total communication cost required for the proposed scheme to achieve the one session is 3072 bits. The communication cost analysis result is presented in Fig. 5.
| Schemes | Send | Receive | Total | |||
|---|---|---|---|---|---|---|
| Comm. bits | Energy cost (μJ) | Comm. bits | Energy cost (μJ) | Comm. bits | Energy cost (μJ) | |
| Tsai & Lo (2015) | 1,280 | 921.6 | 640 | 518.4 | 1,920 | 1,440 |
| Wazid et al. (2017) | 1,024 | 737.28 | 512 | 414.72 | 1,536 | 1,152 |
| Odelu et al. (2016) | 1,344 | 967.68 | 576 | 466.56 | 1,920 | 1,434.24 |
| Gope & Sikdar (2018) | 704 | 506.88 | 864 | 699.84 | 1,568 | 1,206.72 |
| Kumar et al. (2018) | 1,152 | 829.44 | 1,152 | 933.12 | 2,304 | 1,762.56 |
| Zhang et al. (2019) | 704 | 506.88 | 704 | 570.24 | 1,408 | 1,077.12 |
| Ma et al. (2019) | 1,216 | 875.52 | 896 | 725.76 | 2,112 | 1,601.28 |
| Wu et al. (2019) | 1,792 | 1290.24 | 896 | 725.76 | 2,688 | 2,016 |
| Li et al. (2019) | 1,600 | 1152 | 928 | 751.68 | 2,528 | 1,903.68 |
| Khan, Kumar & Ahmad (2019) | 864 | 622.08 | 864 | 699.84 | 1,728 | 1,321.92 |
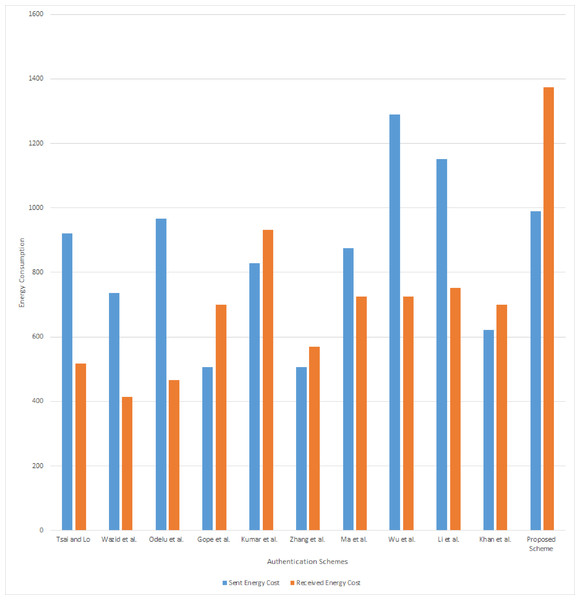
| Proposed Scheme | 1,376 | 990.72 | 1,696 | 1,373.76 | 3,072 | 2,364.48 |
Figure 5: Communication analysis.
We have also calculated the energy cost of the proposed scheme and compared the result with other schemes. The energy cost gives the expected energy required to communicate the data in the communication channel. We have used De Meulenaer et al. (2008) model to compute the energy cost. According to this model, the energy required to send and receive 1 bit of data is 0.72 μJ and 0.81 μJ, respectively. The communication cost of the sent message is 1,376 bits and received message is 1,696 bits, respectively. Hence, the energy cost of the proposed scheme for send and receive messages are 1,376 × 0.72 = 990.72 μJ and 1,696 × 0.81 = 1,373.76 μJ. The total expected energy cost of the proposed scheme is 2,364.48 μJ. The result of energy cost analysis has been presented in Table 9 and also shown in Fig. 6.
Figure 6: Energy consumption in communication.
According to the analysis result presented in Table 9, the communication and energy costs of the proposed scheme are higher than all other schemes. Unlike other schemes the proposed scheme cost includes the communication done between smart meter, NAN gateway, and smart grid during the authentication. In Table 9, Tsai & Lo (2015), Wazid et al. (2017), Odelu et al. (2016), Gope & Sikdar (2018), Zhang et al. (2019), Ma et al. (2019), and Khan, Kumar & Ahmad (2019) schemes, have no communication with NAN gateway during authentication. Therefore, during communication cost comparison, if we neglect the proposed scheme communication messages done with NAN gateway, the total communication cost of the messages {Csm, CIDi, C1, T1}, {C3, Cs, T3} is 1,344 bits and the energy cost is 1,028.16 μJ which is less than other schemes. Similarly, Kumar et al. (2018), Wu et al. (2019), and Li et al. (2019) schemes have no communication between NAN gateway and smart grid, we neglect those communication done in the proposed scheme to do the comparison. Therefore the total communication cost of the messages {Csm, CIDi, C1, T1}, {Cs, T3, C4, Cm, T4, RIDm} is 1,746 bits and the energy cost is 1,353.78 μJ which is lesser than other compared schemes. Hence, we claim that the proposed scheme is efficient than other schemes and robust in the multistage architecture.
Functional analysis
Table 10 presents the functional analysis of the proposed scheme done with other schemes. The features and the functionalities represented in Table 8 are as follows: F1—Multistage authentication, F2—Provide perfect forward secrecy, F3—Prevents replay attack, F4— Prevents insider attack, F5—Prevents man in middle attack, F6—Prevents impersonate attack, F7—Provide mutual authentication, F8— Provide smart meter credentials privacy, F9—Provides session key security. From Table 10, it is clear that the proposed scheme meets all the functional requirements. It also achieves multistage authentication where one smart grid can authenticate the smart meter through the NAN gateway.
| Schemes | F1 | F2 | F3 | F4 | F5 | F6 | F7 | F8 | F9 |
|---|---|---|---|---|---|---|---|---|---|
| Tsai & Lo (2015) | × | ✓ | × | × | ✓ | ✓ | ✓ | × | × |
| Wazid et al. (2017) | × | × | ✓ | × | ✓ | ✓ | ✓ | ✓ | ✓ |
| Odelu et al. (2016) | × | ✓ | × | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Gope & Sikdar (2018) | × | ✓ | × | ✓ | ✓ | ✓ | × | ✓ | ✓ |
| Kumar et al. (2018) | × | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | × | ✓ |
| Zhang et al. (2019) | × | ✓ | × | × | ✓ | ✓ | ✓ | × | ✓ |
| Ma et al. (2019) | × | ✓ | × | ✓ | × | ✓ | ✓ | × | ✓ |
| Wu et al. (2019) | × | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | × | ✓ |
| Li et al. (2019) | × | ✓ | ✓ | ✓ | × | ✓ | ✓ | × | ✓ |
| Khan, Kumar & Ahmad (2019) | × | × | ✓ | ✓ | × | ✓ | ✓ | ✓ | ✓ |
| Proposed | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
Conclusions
The security of smart meter communication is critical for reliable, efficient and stable operation of a contemporary smart grid. This paper addresses the security issues by considering a novel authentication scheme for smart meter communication with the energy control center. The proposed method is based on a novel formulation, where the authentication scheme is dynamic, multi-stage and distributed in nature. The formal proves presented in this paper validate that the proposed model can establish a secure authentication path between a smart meter, NAN gateway, and a SCADA energy center in a distributed manner. We also verified the effectiveness of the proposed authentication scheme against adversarial attacks using a simulation tool AVISPA. Considering the computation, communication and functional costs, this article also presented the efficiency analysis of the proposed authentication scheme. Based on comparative analyses, we can conclude that the proposed scheme is robust and secure as compared to the existing related schemes. Hence, the proposed authentication scheme has the potential to secure smart meter communication between the energy consumers and utility control centers to foster an attack resilient sustainable energy grid.
Appendix
The implementation of the proposed scheme in AVISPA includes the registration phase and the login and authentication phase. Here, three leading roles are named as meter, gateway, and server, represented as SMi, NANGi and Sj. The role specification of the meter is presented in Fig. 7. Here, the process begins by receiving a start signal. The gateway and server roles implementations are given in Figs. 8 and 9. SMi, NANGi and Sj use symmetric key SKuisj for the communication in the channel. The send and receive channels required for communication between meter, gateway, and server are represented by Snd() and Rcv() functions.
Figure 7: Role specification for the SMi of the proposed scheme.
Figure 8: Role specification for the NANGi of the proposed scheme.
Figure 9: Role specification for the SGi of the proposed scheme.
Figures 10 and 11 present the session and environment roles. The session role includes the primary roles for composition and the channels of all roles involved in communication. The environment role specifies the global constants and sessions for an adversary to play as legitimate user roles. It also defines the goals of the proposed scheme.