Hybrid decision support system disaster management: application of lattice ordered q-rung linear Diophantine fuzzy hypersoft sets
- Published
- Accepted
- Received
- Academic Editor
- Elad Michael Schiller
- Subject Areas
- Adaptive and Self-Organizing Systems, Algorithms and Analysis of Algorithms, Autonomous Systems, Optimization Theory and Computation, Theory and Formal Methods
- Keywords
- Lattice, q-Rung linear diophantine fuzzy set, Hypersoft set, Multi-attribute decision making
- Copyright
- © 2025 Vimala et al.
- Licence
- This is an open access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, reproduction and adaptation in any medium and for any purpose provided that it is properly attributed. For attribution, the original author(s), title, publication source (PeerJ Computer Science) and either DOI or URL of the article must be cited.
- Cite this article
- 2025. Hybrid decision support system disaster management: application of lattice ordered q-rung linear Diophantine fuzzy hypersoft sets. PeerJ Computer Science 11:e2927 https://doi.org/10.7717/peerj-cs.2927
Abstract
The discovery of the lattice-ordered q-rung linear Diophantine fuzzy hypersoft set is a significant extension of fuzzy set theory. This study describes many of its fundamental algebraic operations, such as restricted union, extended union, restricted intersection, OR operation, and AND operation, along with examples. Further, an algorithm based on the proposed operations is presented in this study to handle multi-attributed decision-making problems extremely well, along with an illustrative multi-attribute decision-making example in the area of disaster management, which helps in choosing the most appropriate plan to tackle the known natural disaster by considering a greater number of attributes together. Further, the contribution of the method in the disaster management field is presented in the comparative analysis along with computational efficiency and scalability and an analysis of the comparison between the existing decision-making methods and the proposed one to express the superiority and advantages of the suggested approach over the existing methods.
Introduction
The frequent occurrence of uncertainty-related issues in multi-attribute decision-making (MADM) makes them difficult to foresee and manage due to the extensive modeling of these uncertainties. The fuzzy set (FS) theory introduced by Zadeh (1965) is very useful for handling the difficulties brought on by uncertainty. However, FS only has a limited ability to reflect impartial situations. To overcome these restrictions, Atanassov (1986) devised the notion of intuitionistic fuzzy sets (IFS). The IFS’s two indices are membership degree (MD) and non-membership degree (NMD), and their sum value should fall within [0,1]. To solve problems smoothly, Yager (2013) developed the Pythagorean fuzzy set (PFS) in which the total of the MD2 and NMD2 should fall within [0,1]. Yager (2016) also proposed the q-rung orthopair fuzzy sets (q-ROFS), where the MDq and the NMDq are summed together and fall inside the range [0,1]. Later, various information measures (Peng & Liu, 2019) were proposed for q-ROFS. However, each of these ideas has drawbacks of its own. To overcome these drawbacks, Riaz & Hashmi (2019) formulated the theory of the linear Diophantine fuzzy set (LDFS), which contains the notion of reference parameters (RPs). Owing to the usefulness of LDFS, several researchers from various scientific fields were interested in them, and numerous significant studies were produced as a result (Mahmood et al., 2021a, 2021b). Subsequently, the idea of quadratic diophantine fuzzy set was proposed by Zia et al. (2023). Later, Almagrabi et al. (2022) created the q-rung linear Diophantine fuzzy set (q-RLDFS), a particular extension of the IFS, q-ROFS, and LDFS. Further, many real-world decision-making studies such as company selection problem (Ali, 2025), urban planning (Petchimuthu et al., 2025), logistics (Kannan, Jayakumar & Pethaperumal, 2025) and emerging technologies (Kumar & Pamucar, 2025). However, because they are not parametrized, each theory has drawbacks. To overcome the limitations brought on by parametrization, Molodtsov (1999) developed the idea of soft set (SS) theory, which handles vagueness in a parametric manner. Later, by incorporating FS and SS, Roy & Maji (2007) provided the idea of the fuzzy soft set (FSS), which helps present fuzzy data with parametric information. Similar to this, SS theory was incorporated with other extensions of FS theory such as IFS, PFS, q-ROFS, and LDFS (Çağman & Karataş, 2013; Peng et al., 2015; Hussain et al., 2020; Riaz et al., 2020) respectively, to exhibit these fuzzy extension data with parametric information and obtained intuitionistic fuzzy soft set (IFSS), Pythagorean fuzzy soft set (PFSS), q-rung orthopair fuzzy soft set (q-ROFSS) and linear Diophantine fuzzy soft set (LDFSS). Smarandache (2018) then transformed the function into a multi-attributed function to establish the idea of the hypersoft set (HSS) as an extension of SS. By incorporating HSS with FS and IFS, Smarandache (2018) also proposed the ideas of the fuzzy hypersoft set (FHSS) and intuitionistic fuzzy hypersoft set (IFHSS), which expresses FS and IFS data with multi-sub-parameter. Similarly, by incorporating q-ROFS with HSS, Khan, Gulistan & Wahab (2022) presented the q-rung orthopair fuzzy hypersoft set (q-ROFHSS), and by incorporating q-RLDFS with HSS, Surya et al. (2024) presented the q-rung linear Diophantine fuzzy hypersoft set (q-RLDFHSS). In many real-life problems, there is a ranking among the parameters to deal with such problems very effectively. Ali et al. (2015) proposed a lattice-ordered soft set (LOSS). Later, Aslam et al. (2019) discussed the notion of lattice-ordered fuzzy soft set (LOFSS), and Mahmood et al. (2018) discussed the notion of lattice-ordered intuitionistic fuzzy soft set (LOIFSS). Further, many researchers (Rajareega & Vimala, 2021; Pandipriya, Vimala & Begam, 2018; Mahmood, Rehman & Sezgin, 2018; Begam et al., 2020; Khan, Bakhat & Iftikhar, 2019; Sabeena Begam & Vimala, 2019) developed the concepts of lattice-ordered structure to various areas of FS theory and their extensions. Likewise, to discuss real-life q-RLDFHS problems when there is a ranking among the multi-sub-parameters the notion of lattice ordered q-rung linear Diophantine fuzzy hypersoft set (LOq-RLDFHSS) is essential.
Research gap
Listed below are the research gaps:
From the analysis of existing literature, we can see that in theoretical aspects, the existing literature does not cover many fundamental algebraic operations of LOq-RLDFHSS.
Further from the existing literature, we can see that while there are several parametric decision-making (DM) studies conducted under various fuzzy structures, it is challenging to demonstrate many MADM real-world problems under LOq-RLDFHS environment using the existing literature.
Motivation
The following are the study’s motivations:
The study aims to close these research gaps by developing fundamental algebraic operations and a MADM method based on LOq-RLDFHSS.
Another main motive of the study is to contribute to the disaster management field by the proposed MADM approach, since the existing DM methods in the disaster management field cannot handle multiple attributes simultaneously.
Objectives
The main objectives of this work are listed below:
To provide many fundamental algebraic operations of LOq-RLDFHSS.
To provide an effective MADM strategy based on LOq-RLDFHSS.
To provide an appropriate numerical illustration for the suggested MADM strategy in the field of disaster management.
Contribution
The core contributions of the work are as follows:
Many algebraic operators of LOq-RLDFHSS are proposed in this study, such as restricted union, restricted intersection, extended union, OR operation, AND operation, and complement.
A MADM algorithm based on the LOq-RLDFHSS is presented in the study.
Further, a real-world problem in the field of disaster management is depicted as a numerical example of the suggested MADM algorithm to show the efficacy of the proposed algorithm.
To demonstrate the potency and efficacy of the suggested concepts and the MADM approach, a comparative assessment that describes the theoretical improvement of the proposed study and its contribution to the field of disaster management is presented, along with the minor restrictions of the proposed concepts.
The list of most of the abbreviations used in this study is given as a table in “List of abbreviation used in the study”. The article is structured as follows:
“Background” contains the required introductory notations and definitions. “Algebraic operations of LOq-RLDFHSS” consists of fundamental algebraic operations of LOq-RLDFHSS. “MADM Approach Based on LOq-RLDFHSS” consists of a MADM algorithm based on LOq-RLDFHSS to successfully solve MADM challenges; a MADM problem in disaster management which demonstrates the efficiency of the proposed algorithm. To describe the superiority of the proposed idea to the existing ideas, a comparative assessment has been undertaken in “Comparative Assessment”. Finally, “Conclusion” provides the conclusion of the article.
Background
This section provides the requisite notations and definitions for this article.
A binary relation on a non-empty set is said to be a partial order on if it is antisymmetric, reflexive and transitive. Also, is said to be a total order on if , either or .
A partial order set L is said to be a lattice if the set has a greatest lower bound and least upper bound L. If L contains 1 and 0 such that L, 0 1, then L is called a bounded lattice.
Definition 2.1. Atanassov (1986): Let be the set of alternatives. A IFS is defined as
where and [0,1] are MD and NMD fulfilling 0 1.
Definition 2.2. Almagrabi et al. (2022): Let be the set of alternatives. A q-RLDFS is defined as
where and [0,1] are MD, NMD and their corresponding RPs respectively, fulfilling 0 1 and 0 1 , q 1.
Definition 2.3. Molodtsov (1999): Let be the set of alternatives, be the set of attributes, and . Then SS is a pair defined by the mapping
where P is the power set of .
Definition 2.4. Ali et al. (2015): Let be a SS over , where
Then is said to be a LOSS if .
Definition 2.5. Çağman & Karataş (2013): Let be the set of alternatives, be the set of attributes, and . Then IFSS is a pair defined by the mapping
where IFP is the IF power set of .
Definition 2.6. Mahmood et al. (2018): Let be a IFSS over , where
Then is said to be a LOIFSS if .
Definition 2.7. Smarandache (2018): Let be the set of alternatives and denote the Power set of . Let with for and be the attribute values of n distinct attributes respectively and for each , be non empty subset of and . Then HSS over is the pair defined by the map
This can be represented as .
Definition 2.8. Surya et al. (2024): Let be the set of alternatives and q-RLDFP ( ) denote the q-RLDF Power set of . Let with for and be the attribute values of n distinct attributes respectively and for each , be non empty subset of and . Then, the q-Rung Linear Diophantine Fuzzy Hypersoft Set over (q-RLDFHSS ( )) is the pair defined by the map
This can be represented as and the q-RLDFHS Number (q-RLDFHSN)
= can be express as = .
Definition 2.9. Surya et al. (2024): Let q-RLDFHSS ( ), then is said to be q-RLDFHS subset of , if
(i)
(ii)
(i.e.,) and .
Algebraic operations of loq-rldfhss
In this section, the fundamental algebraic operations of LOq-RLDFHSS are presented.
Definition 3.1. A is said to be lattice ordered q-RLDFHSS over (LOq-RLDFHSS ( )) if for mapping ,
(i.e.,)
, ,
and
where and for .
Also, each is defined by its corresponding binary relation and forms a relation defined by in for .
The following example clarifies the definition above.
EXAMPLE 1. Let be the set of hotels for accommodation, consider the attributes = {charges}, food}, service} and = {extra charges , room rent , = {taste , hygiene , = {customer service be their corresponding attribute values respectively.
Suppose that,
For each i = 1, 2, 3, =
The elements in each set have an order among them, they are
The elements in set are in the order
The elements in set are in the order
has only one element and
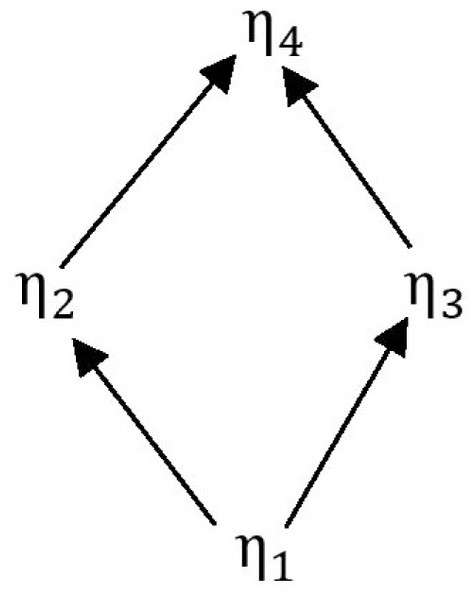
Then the order of elements in set is shown in Fig. 1.
Figure 1: The order among elements in .
Further, the following is how the attributes are categorized
The attribute “charges” and its attribute values indicates whether the alternative is cheap or not cheap
The attribute “food” and its attribute values indicates whether the alternative is good or not good
The attribute “service” and its attribute values indicates whether the alternative satisfies or dissatisfies
Then, the Cartesian product of attribute values exemplifies that the alternative is (cheap, good, satisfies) altogether or (not cheap, not good, dissatisfies) altogether.
Then, q-RLDFHSS ( ) may be expressed as
We will assume that q = 3.
The characteristic of this q-RLDFHSS is MD, NMD (cheap, good, satisfies), (not cheap, not good, dissatisfies) .
Clearly and , therefore, is a LOq-RLDFHSS .
Definition 3.2. Let be the set of alternatives and LOq-RLDFHSS . Their Restricted union is defined by where and we have .
,
,
and
.
Proposition 3.3. Let LOq-RLDFHSS . Then LOq-RLDFHSS .
Proof. See “Proof of Proposition 3.2”. □
Definition 3.4. Let be the set of alternatives and LOq-RLDFHSS . Their Restricted intersection is defined by where and we have .
,
,
and
.
Proposition 3.5. Let LOq-RLDFHSS . Then LOq-RLDFHSS .
Proof. See “Proof of Proposition 3.4”. □
Definition 3.6. Let be the set of alternatives and LOq-RLDFHSS . Their extended union is defined by where
Proposition 3.7. Let LOq-RLDFHSS . Then LOq-RLDFHSS , if one of them is a LOq-RLDFHSS subset of other.
Proof. See “Proof of Proposition 3.6”. □
Definition 3.8. Let . Then partial order on is defined as for any and .
Definition 3.9. Let be the set of alternatives and LOq-RLDFHSS . Their “AND” operation is defined by
where
and
.
Proposition 3.10. Let be the set of alternatives and LOq-RLDFHSS . Then LOq-RLDFHSS .
Proof. See “Proof of Proposition 3.9”. □
Definition 3.11. Let be the set of alternatives and LOq-RLDFHSS . Then their “OR” operation is defined by
where
and
Proposition 3.12. Let be the set of alternatives and LOq-RLDFHSS . Then LOq-RLDFHSS .
Proof. See “Proof of Proposition 3.11”. □
Definition 3.13. Let LOq-RLDFHSS .
If = = 0, = = 1 and , Then, is called the relative null LOq-RLDFHSS and is denoted by .
Definition 3.14. Let LOq-RLDFHSS .
If = = 1, = = 0 and , Then, is called the relative universal LOq-RLDFHSS and is denoted by .
Proposition 3.15. Let LOq-RLDFHSS . Then
1. =
2. =
3. =
4. =
5. =
6. =
Proof. Straightforward. □
Definition 3.16. Let LOq-RLDFHSS . Then complement of denoted by and is defined as follows
= and .
Proposition 3.17. Let LOq-RLDFHSS . Then
Proof. Let LOq-RLDFHSS . Then complement of is
= and ,
Now complement of is
= and = . □
EXAMPLE 2. Let be a set of alternatives, be a set of parameters with an order defined by and be another set of parameters with an order defined by . Then, let
be a q-RLDFHSS with q as 3, and since , this implies is a LOq-RLDFHSS. Also, let
be another q-RLDFHSS with q as 3, and since , this implies is a LOq-RLDFHSS.
The following operations are then derived:
Madm approach based on loq-rldfhss
In this section, the comparison matrix of LOq-RLDFHSS and a MADM algorithm based on LOq-RLDFHSS are described and a MADM problem in the field of disaster management is discussed as a numerical illustration for the proposed MADM algorithm.
Definition 4.1. The comparison matrix of LOq-RLDFHSS is a matrix in which rows represent the alternatives such as and columns represent the parameters . The entries are and computed as , where is the integer computed as number of times greater than or equal to , for is the integer computed as number of times greater than or equal to , for is the integer computed as number of times greater than or equal to , for and is the integer computed as number of times greater than or equal to , for . Further, the range of lies within .
Definition 4.2. The score of an alternative is and calculated as
where the range lies within .
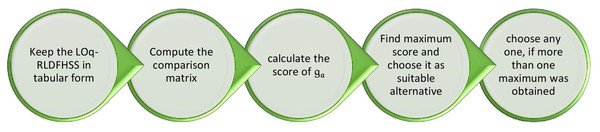
Algorithm
The following steps describe the algorithm for selecting the most suitable alternative
Step 1: Consider the LOq-RLDFHSS ( ) and keep it in tabular form
Step 2: Compute the comparison matrix of LOq-RLDFHSS.
Step 3: Calculate the score of a
Step 4: Find = Max and choose it as the suitable alternative
Step 5: If multiple alternatives share the maximum score, select any one of them.
Figure 2 shows the proposed algorithm as a flowchart.
Figure 2: Flowchart showing the steps of the proposed LOq-RLDFHSS-based MADM algorithm.
Numerical illustration
A general study about disaster management
Disaster management or emergency management is the administrative responsibility for creating the framework that assists societies in reducing their vulnerability to hazards and coping with calamities. Contrary to its name, disaster management does not focus on handling crises, which are typically regarded as minor occurrences with little consequences that are dealt with through regular community activities. The main goal of emergency management is the management of disasters, which are occurrences with more consequences than a community can manage on its own. A mix of efforts by individuals, households, businesses, local governments, and/or higher levels of government is typically required for disaster management. Even though the discipline of emergency management uses a variety of terminologies, operations can generally be broken down into four categories: preparedness, response, mitigation, and recovery. In other words, mitigation of disaster risks and prevention are also frequently used.
The guiding principle of disaster management is disaster mitigation. The continuous work aims to reduce disasters’ harm to both persons and property. Mitigation measures include avoiding constructing near floodplains, designing bridges to resist earthquakes, developing and enforcing hurricane-proof building regulations, and more. Mitigation refers to sustained actions that minimize or prevent long-term danger to individuals and assets from environmental risks and their effects.” Disaster consequences are continuously being lessened by federal, state, municipal, and individual actions.
Authorities and organizations on a national or international scale may provide this assistance during disaster. Effective coordination of disaster assistance is frequently crucial when numerous organizations contribute to the response, but competence has been degraded by the disaster or overwhelmed by demand. The US government released an article called the National Response Framework (Federal Emergency Management Agency, 2023) that outlines the responsibilities of authorities of the state, local, national, and tribal governments. It offers guidance on how to fully or partially implement disaster support services to aid in the response and recovery process.
The recovery phase begins once there is no immediate danger to human life. Getting the afflicted area back to normal as soon as possible is the urgent goal of the recovery phase. Trained laypeople give psychological first aid in the early wake of a disaster to help the affected populace cope and recover. In addition to providing practical support and assisting with procuring necessities like food and water, trained staff can also provide links to important resources. Similar to medical first aid, psychological first aid does not require therapists to be licensed clinicians. It is not debriefing, counseling, or psychotherapy.
Numerous research such as disaster management cycle of natural disaster (Arifah, Tariq & Juni, 2019), large scale group decision making in disaster management (Wan et al., 2020), post-disaster reconstruction projects (Mohammadnazari et al., 2022), use of indicators in vulnerability assessment (Papathoma-Köhle et al., 2019) in decision-making have been carried out in disaster management. Now, we show the utilization of proposed conceptions and algorithms in real life by a MADM problem in the field of disaster management, which helps to choose the most appropriate plan to tackle the known upcoming natural disaster by considering more attributes together. The problem is presented below, and its contribution to the disaster management field is discussed in detail in the comparative assessment section.
Problem
Suppose disaster management wants to choose the most appropriate plan from a set of plans , , to tackle some of the known upcoming natural disasters as a precautionary measure and a team of decision makers was appointed to analyze the plans, the decision makers are considering the attributes = {mitigation}, response}, recovery} and their sub attributes are education and awareness programs , regulation and infrastructure projects , maintaining regular services and activities , protecting life and psychological recovery respectively. Also, the order of preference of elements in each set , and by decision-makers is given as follows
The elements in set are in the order
The elements in set are in the order
has only one element and
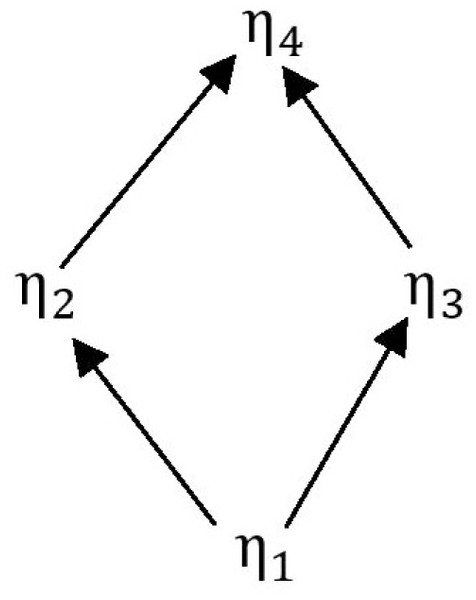
Then the order of elements in set is shown in the Fig. 3.
Figure 3: The order among elements in .
Further, decision-makers categorize the attributes as follows:
The attribute “mitigation” and its attribute values indicates whether the plan is high or low
The attribute “response” and its attribute values indicates whether the plan is good or not good
The attribute “recovery” and its attribute values indicates whether the plan is effective or not effective
Then, the Cartesian product of attribute values exemplifies that the plan is (high, good, effective) all together or (low, not good, not effective) all together.
The opinions and data observed by the decision makers are constructed and expressed as a q-RLDFHSS .
The characteristic of this q-RLDFHSS is MD, NMD (high, good, effective), (low, not good, not effective) .
We will assume that q = 3.
Clearly and , therefore, is a LOq-RLDFHSS .
In this LOq-RLDFHSS, the plan and the parameter = (education and awareness programs, maintaining regular services and activities, psychological recovery) has the numeric value . This value expresses that for the parameter the plan has 33 truth value and false value. The pair (0.31,0.82) indicates the RP of the truth and false values, respectively, where we can observe that for (high at education and awareness programs, good at maintaining regular services and activities, effective in psychological recovery) all together the plan expresses and for (low at education and awareness programs, not good at maintaining regular services and activities, not effective in psychological recovery) all together the plan expresses . Similarly, all other numeric values are expressed in this LOq-RLDFHSS.
Step 1: Tabular form of LOq-RLDFHSS is shown in Table 1.
| ( ) | |||
|---|---|---|---|
| (0.33, 0.87), (0.31, 0.82) | (0.29, 0.76), (0.33, 0.81) | (0.38, 0.63), (0.17, 0.72) | |
| (0.4, 0.65), (0.38, 0.71) | (0.32, 0.57), (0.43, 0.66) | (0.53, 0.61), (0.39, 0.51) | |
| (0.55, 0.66), (0.57, 0.72) | (0.35, 0.53), (0.52, 0.81) | (0.46, 0.54), (0.24, 0.57) | |
| (0.63, 0.58), (0.65, 0.69) | (0.63, 0.49), (0.74, 0.48) | (0.83, 0.41), (0.72, 0.28) |
Step 2: Comparision matrix of LOq-RLDFHSS is shown in Table 2.
Step 3: The scores of the alternatives are shown in Table 3.
| ( ) | |||
|---|---|---|---|
| Score |
From the obtained scores, we observed that is the most appropriate plan to tackle the disaster, and we got the ranking of plans as .
Comparative assessment
Validity test
The effectiveness of a MADM strategy depends on the coherence of the qualities, the relationship between the alternatives, and the decision-maker’s objective evaluations. Wang & Triantaphyllou (2008) created three effective validity test criteria, which must be completed for a MADM approach to be considered legitimate.
Test criteria 1: The optimal choice remains the same if one selects a non-ideal alternative over a non-optimal one without changing the weight of any attribute.
Test criteria 2: The transitive nature is necessary for a decision-making approach to be effective.
Test criteria 3: If the decision-making problem is broken down into smaller subproblems, the smaller subproblem’s order has to correspond with the original problem’s order.
An examination of the suggested method’s validity is provided below:
Test criteria 1: Consider the same disaster management problem by replacing the non-ideal alternative with a worse alternative , whose numeric values according to the parameters are
Then, after analyzing these three alternatives by the proposed method, we obtain ranking as . The result makes it clear that the best solution remains constant. Therefore, test criteria 1 is satisfied for the proposed methodology.
Test criteria 2 and 3: We divide the considered problem into sub-problems as and . Then using the proposed method we obtain , and as the ranking of sub-problems respectively. Therefore, we can see that the overall ranking remains constant as . For the suggested approach, test criteria 2 and 3 are therefore valid.
Comparative analysis
To analyze the superiority of the proposed DM method, the advantages and restrictions of existing and proposed DM methods are described in Table 4.
| DM methods | Advantages | Restrictions |
|---|---|---|
| FS (Zadeh, 1965) | Addresses uncertainty by (MD) | Unable to deal with (NMD) and parametrization |
| IFS (Atanassov, 1986) | Addresses uncertainty by and | Restricted in handling uncertainty by the condition [0,1], also unable to deal with parametrization |
| PFS (Yager, 2013) | Addresses uncertainty by and even if [0,1] | Restricted in handling uncertainty by the condition [0,1], also unable to deal with parametrization |
| q-ROFS (Yager, 2016) | Addresses uncertainty by and even if [0,1] | Restricted in handling uncertainty by the condition [0,1], also unable to deal with parametrization |
| LDFS (Riaz & Hashmi, 2019) | Addresses uncertainty by , , (RP corresponding to MD) and (RP corresponding to NMD) even if [0,1] | Restricted in handling uncertainty by the conditions [0,1] and [0,1], also unable to deal with parametrization |
| q-RLDFS (Almagrabi et al., 2022) | Addresses uncertainty by , , and even if [0,1] and [0,1] | Restricted in handling uncertainty by the conditions [0,1] and [0,1] also unable to deal with parametrization |
| SS (Molodtsov, 1999) | Able to deal with parametrization | Unable to address uncertainty by parameterization |
| FSS (Roy & Maji, 2007) | Addresses FS with parameterized values | Unable to address uncertainty exceeding FS’s restriction by parameterized values and also unable to address FS by multi-sub-parameterized values |
| IFSS (Çağman & Karataş, 2013) | Addresses IFS with parameterized values | Unable to address uncertainty exceeding IFS’s restriction by parameterized values and also unable to address IFS by multi-sub-parameterized values |
| q-ROFSS (Hussain et al., 2020) | Addresses q-ROFS with parameterized values | Unable to address uncertainty exceeding q-ROFS’s restriction by parameterized values and also unable to address q-ROFS by multi-sub-parameterized values |
| LDFSS (Riaz et al., 2020) | Addresses LDFS with parameterized values | Unable to address uncertainty exceeding LDFS’s restriction by parameterized values and also unable to address LDFS by multi-sub-parameterized values |
| LOSS (Ali et al., 2015) | Addresses SS effectively when there is a ranking among parameters | Unable to address uncertainty by parameterization |
| LOFSS (Aslam et al., 2019) | Addresses FSS effectively when there is a ranking among parameters | Unable to address uncertainty exceeding FS’s restriction by parameterized values and also unable to address FS by multi-sub-parameterized values |
| LOIFSS (Mahmood et al., 2018) | Addresses IFSS effectively when there is a ranking among parameters | Unable to address uncertainty exceeding IFS’s restriction by parameterized values and also unable to address IFS by multi-sub-parameterized values |
| HSS (Smarandache, 2018) | Able to deal with multi-sub-parametrization | Unable to address uncertainty by multi-sub-parameterization |
| FHSS (Smarandache, 2018) | Addresses FS with multi-sub-parameterized values | Unable to address uncertainty exceeding FS’s restriction by multi-sub-parameterized values |
| IFHSS (Smarandache, 2018) | Addresses IFS with multi-sub-parameterized values | Unable to address uncertainty exceeding IFS’s restriction by multi-sub-parameterized values |
| q-ROFHSS (Khan, Gulistan & Wahab, 2022) | Addresses q-ROFS with multi-sub-parameterized values | Unable to address uncertainty exceeding q-ROFS’s restriction by multi-sub-parameterized values |
| q-RLDFHSS (Surya et al., 2024) | Addresses q-RLDFS with multi-sub-parameterized values | Unable to address uncertainty exceeding q-RLDFS’s restriction by multi-sub-parameterized values |
| LOq-RLDFHSS (proposed) | Addresses q-RLDFHSS effectively even when there is a ranking among multi-sub-parameters | Unable to address uncertainty exceeding q-RLDFS’s restriction by multi-sub-parameterized values |
Discussion
Superiority of the proposed MADM method
In Table 4, the comparison analysis brings to light the exceptional superiority of the innovatively proposed MADM method when juxtaposed with the array of existing MADM methodologies rooted in fuzzy theories such as FS, IFS, PFS, q-ROFS, LDFS, q-RLDFS, SS, FSS, IFSS, q-ROFSS, LDFSS, HSS, FHSS, IFHSS, q-ROFHSS, LOSS, LOFSS and LOIFSS. The distinguished LOq-RLDFHSS based DM method, in its unmatched prowess, showcases its ability to effectively manage q-RLDFS even within the intricate complexities of multi-sub-attributed scenarios that entail the prioritization and ordering of these multi-sub-attributes. This distinctive characteristic proves to be more suitable in navigating through a wide spectrum of real-world MADM situations with finesse.
Computational effiency and scalability
The proposed MADM is highly efficient in terms of scalability since, it is capable of handling real-world problems with large data. Further, the proposed MADM methodology is capable of handling problems with large number of alternatives and parameters, but to understand the methodology clearly, the disaster management problem given in Section “MADM Approach Based on LOq-RLDFHSS” considers three alternatives and four parameters. Also, it is suitable to implement the proposed MADM method in various large-scale real-world applications such as medical diagnosis, supply chain optimization and more. In this study it is contributed to the field of disaster management. Also, the results obtained by the proposed method is more reliable and accurate since it considers more parameters and data, to handle the problem than the existing fuzzy MADM methods.
Contribution in the disaster management field
Even though various decision-making approaches and case studies (Arifah, Tariq & Juni, 2019; Wan et al., 2020; Mohammadnazari et al., 2022; Papathoma-Köhle et al., 2019) contribute to disaster management, those studies became inadequate when the disaster situation needed to incorporate more attributes together simultaneously to obtain the most appropriate solution. Further, the presented case study is a unique case in disaster management, which is not yet and unable to be described by the existing MADM approaches in the disaster management field. From this it becomes clear that conventional MADM strategies are inadequate when confronted with scenarios teeming with many intricate data, unlike our proposed method, which adeptly converts intricate parameter data into streamlined numerical formats.
Also, it is crucial to recognize that while the proposed method undeniably offers substantial benefits, it is not devoid of its own set of limitations, such as limitations mentioned in Table 4. Further, the algorithm shows a limitation in the case of ties.
Conclusion
For addressing a wide range of uncertain challenges, the q-RLDFHSS and LOq-RLDFHSS stand out as innovative extensions of FS theory. Throughout this research, numerous fundamental algebraic operations of LOq-RLDFHSS have been identified, emphasizing the development of an algorithm specifically designed to solve MADM problems leveraging the concepts of LOq-RLDFHSS. By exploring a unique MADM scenario within the domain of disaster management, which helps to choose the most appropriate plan to tackle the known upcoming natural disaster by considering more attributes together, the use of the suggested method in practice is thoroughly examined. The comparative analysis showcases the superiority and effectiveness of the novel MADM method against existing approaches, underscoring its value in real-world applications. In the comparative analysis, the study’s contribution to the disaster management field is also discussed in detail.
Future direction
In future, it will focus on developing advanced information measures and aggregation operators tailored for the LOq-RLDFHSS. Further, it will be focused on overcoming the limitations of the proposed study by utilizing the concept of hesitancy function described in Zia et al. (2024). Also, it is aimed to discuss various real-world problems in different domains such as medical, cybersecurity and pattern recognition.
Appendix
List of abbreviation used in the study
The list of most of the abbreviations used in this study is described in Table 5.
| Abbreviation | Description |
|---|---|
| FS | Fuzzy set |
| MADM | Multi-attributed decision-making |
| MD | Membership degree |
| IFS | Intuitionistic fuzzy set |
| NMG | Non-membership Degree |
| PFS | Pythagorean fuzzy set |
| q-ROFS | q-Rung orthopair fuzzy set |
| LDFS | Linear Diophantine fuzzy set |
| RPs | Reference parameters |
| q-RLDFS | q-Rung linear Diophantine fuzzy set |
| SS | Soft set |
| FSS | Fuzzy soft set |
| IFSS | Intuitonistic fuzzy soft set |
| q-ROFSS | q-Rung orthopair fuzzy soft set |
| LDFSS | Linear Diophantine fuzzy soft set |
| HSS | Hypersoft set |
| FHSS | Fuzzy hypersoft set |
| IFHSS | Intuitionistic fuzzy hypersoft set |
| q-ROFHSS | q-Rung orthopair fuzzy hypersoft set |
| q-RLDFHSS | q-Rung linear diophantine fuzzy hypersoft set |
| LOSS | Lattice ordered soft set |
| LOFSS | Lattice ordered fuzzy soft set |
| LOIFSS | Lattice ordered intuitionistic fuzzy soft set |
| LOq-RLDFSS | Lattice ordered q-rung linear Diophantine fuzzy hypersoft set |
Proof of proposition 3.2
Proof. Let LOq-RLDFHSS ( . Then by Definition 3.2
, where .
If , then result is trivial.
Now for , since
Therefore for any we have
and for any we have
Now for any and
and
and whenever
Max Max
Min Min
Max Max
Min Min
for
LOq-RLDFHSS . □
Proof of proposition 3.4
Proof. Let LOq-RLDFHSS ( . Then by Definition 3.4
, where .
If , then result is trivial.
Now for , since
Therefore for any we have
and for any we have
Now for any and
and
and whenever
Min Min
Max Max
Min Min
Max Max
for
LOq-RLDFHSS . □
Proof of proposition 3.6
Proof. Let LOq-RLDFHSS . Then by Definition 3.6
where
suppose,
. Then and
, for every and
since
Therefore for any we have
and for any we have
Now for any and
or and because
now take
and
and whenever
Max Max
Min Min
Max Max
Min Min
for
Thus LOq-RLDFHSS if
Now suppose for any and
whenever
LOq-RLDFHSS
Hence LOq-RLDFHSS in both cases
LOq-RLDFHSS , if one of them is a LOq-RLDFHS subset of other. □
Proof of proposition 3.9
Proof. Let LOq-RLDFHSS . Then by Definition 3.9
also
For any we have
and for any we have
Now for any . Then by Definition 3.8
The order on is and
and
Min Min
Max Max
Min Min
Max Max
for
Therefore, LOq-RLDFHSS . □
Proof of proposition 3.11
Proof. Let LOq-RLDFHSS . Then by Definition 3.11
also
For any we have
and for any we have
Now for any . Then by Definition 3.8
Now for any . Then by Definition 3.8
The order on is and
and
Max Max
Min Min
Max Max
Min Min
for
Therefore, LOq-RLDFHSS . □