Deniable ring signature scheme based on the ISRSAC digital signature algorithm
- Published
- Accepted
- Received
- Academic Editor
- Trang Do
- Subject Areas
- Algorithms and Analysis of Algorithms, Cryptography, Optimization Theory and Computation
- Keywords
- ISRSAC, Computer architecture, Ring signature, Privacy protection, Controllable supervision
- Copyright
- © 2024 Zhang et al.
- Licence
- This is an open access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, reproduction and adaptation in any medium and for any purpose provided that it is properly attributed. For attribution, the original author(s), title, publication source (PeerJ Computer Science) and either DOI or URL of the article must be cited.
- Cite this article
- 2024. Deniable ring signature scheme based on the ISRSAC digital signature algorithm. PeerJ Computer Science 10:e2190 https://doi.org/10.7717/peerj-cs.2190
Abstract
This article introduces a deniable ring signature scheme within the framework of a ring signature protocol, which allows a member of the ring to assert or deny their role as the signature’s originator without the involvement of a trusted third party. Deniable ring signatures find applications in various scenarios where balancing privacy protection with supervised oversight is crucial. In this work, we present a novel deniable ring signature scheme based on the ISRSAC digital signature, tailored for environments with regulatory requirements, empowering regulators to hold malicious signers accountable. We formally validate the scheme’s correctness, unforgeability, anonymity, traceability, and non-frameability through rigorous proofs. Additionally, we conduct a comparative analysis of the communication and computational overheads associated with our proposed scheme, demonstrating its superiority in practical scenarios such as electronic auctions and anonymous reporting mechanisms.
Introduction
A cryptographic notion called a ring signature is employed in digital signatures to safeguard signers’ identity and privacy. A typical digital signature uses the signer’s private key to certify the data, which the public key may confirm. Ring signatures, on the other hand, make it possible to sign a group of people without disclosing who each participant is. Every participant in a ring signature possesses a pair of keys, a public key and a private key. Members select a “ring” or group of members to sign with, then use their unique private keys to sign the data. The buyer can verify that the signature is genuine, but it is impossible to ascertain whose member signed it. One salient characteristic of ring signatures is the arbitrary selection of member sets; furthermore, it is impossible to identify the real signer of a member collection including many members at the same time. This makes ring signatures ideal for situations requiring privacy protection and anonymity, such anonymous authentication, anonymous voting, and so on. Rivest, Shamir & Tauman (2001) proposed ring signatures to achieve digital signatures that are anonymous to identity. Bresson, Stern & Szydlo (2002) proposed the first t-out-of-N gate ring signature. In order to make it possible for anyone to ascertain if two ring signatures were created by the same signer, Tsang et al. (2004) presented a separable linkability threshold ring signature system. In order to meet the safety criteria in real-world applications (Xuemin et al., 2024; Xie et al., 2024; Li et al., 2024), researchers have now carried out more research and created ring signature schemes with various features.
In order to validate who the true signer of the ring signature is, Komano et al. (2006) introduced a confirmation/denial algorithm to the standard ring signature and presented the idea of a negated ring signature. Deniable ring signatures are traceable and appropriate for application environments requiring supervision because they can trace the true signer without involving a third party, in contrast to the unconditional anonymity of general ring signatures, which prevents regulators from holding malicious signers accountable. Wu et al. (2006) used accumulators and knowledge signatures to generate self-organizing group signatures that were demonstrably safe and repudiable. Hu & Liu (2011) combined the concepts of “constant-size” and “deniable” to form an identity-based deniable ring signature with a constant-size signature. They proposed a new scheme with constant-size signature length based on an improved accumulator from bilinear pairings, which resolves the issue of anonymity abuse. Using the security paradigm put forth by Komano et al. (2006), Zeng, Jiang & Qin (2012) created a deniable ring signature based on bilinear pairings. This signature can demonstrate its security under the random oracle machine model, where the confirmation/denial mechanism operates in a non-interactive manner. According to the standard paradigm, Zeng et al. (2013) suggests a non-interactive deniable ring signature system that can demonstrate security.
Better security performance under public-key cryptography is achieved via the ISRSAC algorithm, which is an enhancement of the classic RSA method. In addition, as it is the fundamental algorithm for creating digital signature schemes, digital signatures built using ISRSAC have more security than those built using RSA. Thangavel et al. (2015) suggested the ESRKGS method, which makes breaking apart big numbers more challenging. Yang et al. (2021) created a digital signature system based on ISRSAC, and they created a broadcast multi-signature scheme, an ordered multi-signature scheme, and a proxy signature scheme using this foundation. A sequential proxy multi-signature scheme based on ISRSAC and broadcast proxy multi-signature techniques was devised by Liu, Zhang & Ning (2022), building on Yang et al. (2021). They built a ring signature system using the ISRSAC algorithm and demonstrated several security features. An adaptor signature system based on ISRSAC was presented by Zhang et al. (2023) in 2023 and has a lot of potential applications in blockchain and other use cases. Since then, Liu, Yuan & Zhang (2023) have suggested a study review and carried out extensive research on the ISRSAC algorithm and the digital signature scheme created based on the method. These days, an increasing number of academics have built digital signature schemes based on ISRSAC that are appropriate for many circumstances, coupled digital signature technology with the security benefits of the algorithm, and researched and debated its applicability in numerous industries.
One disadvantage of ring signatures is that their ability to provide anonymity can be exploited by a malicious signer, which can then raise suspicions about the other members of the ring. Deniable ring signatures were created for this purpose. Initially, it can protect the person signing, enable other members of the group to deny their participation, and offer proof of the actual signer’s identity. These types of signatures have numerous practical applications.
Even though the deniable ring signature system is really helpful, there are still several issues with it as it is. It is clearly unfair to honest ring members for attackers to be able to forge denials on behalf of some of them due to specific restrictions in various schemes’ security models and failure to take non-frameability into consideration. Second, for the majority of schemes, the size of the rejections and signatures grows with the square of the ring membership. This implies that the size of signatures and rejections rises considerably with the number of ring members. Consequently, another pressing issue is how to create a sublinear deniable ring signature method. To further address the aforementioned issues, this article suggests a deniable ring signature scheme based on ISRSAC. This scheme effectively lowers traffic volume, enhances security at the signature algorithm level, improves security model-based security, and increases operation efficiency through better implementation.
Background
Difficult problem of factoring large integers
The decomposition of a large integer as the product of its prime factors, or the representation of a large integer as the product of two or more prime numbers, is known as the difficulty factoring large integers problem. The description of the problem can be simply expressed as: given a large integer n, find two prime numbers p, q such that n = p⋅q. In this problem, the size of n is usually very large, far beyond what a computer can solve in a reasonable amount of time. The problem cannot be solved efficiently using a polynomial algorithm. This means that extracting its prime factor from a large integer requires a considerable number of computational resources and time. Therefore, the problem is considered “difficult”.
The hard challenge of massive integer factorization serves as the foundation for the RSA encryption technique. The intricacy of factoring a big integer into the product of two prime integers forms the foundation of the security of the RSA encryption technique. A major concern to contemporary computer security is the possibility of cracking communication encrypted using RSA if someone can successfully solve the huge integer factorization problem.
Although the difficult problem of large integer factorization is theoretically considered a difficult problem, there are still algorithms that can be used to solve large integer factorization in some specific cases. For example, prime factorization algorithms, such as Pollard’s rho algorithm, the secondary sieving method, and the number field sieving method, can efficiently decompose large integers in certain situations. However, these algorithms typically only operate with a limited range of integers. For larger integers, they become time-consuming and impractical.
ISRSAC digital signature algorithm
This section briefly introduces the digital signature algorithm based on ISRSAC, which includes four PPT algorithms: System initialization (Setup), key generation algorithm (KeyGen), signature generation algorithm (Sign), and signature verification algorithm (Verify).
-
System initialization (Setup): given the safety parameters λ, randomly select two large prime numbers p and q, where p ≠ q, p > 3, q > 3, calculate n = p⋅q⋅(p − 1)⋅(q − 1), m = p⋅q. Randomly select an integer r, where this condition of r is met: p > 2r < q, and then calculate .
-
Key generation algorithm (KeyGen): Select the public key e, where 1 < e < α(n), gcd(e, α(n)) = 1. Calculate the private key d, where d⋅e ≡ 1(modα(n)). In summary, determine the public key (e, m) and private key (d, n).
-
Signature generation algorithm (Sign): Suppose the plaintext is M, the hash function is H, and the hash value is H(M). The private key is (d, n), calculated S ≡ H(M)d(modm) as the signature of H(M).
-
Signature verification algorithm (Verify): Verify the signature S on the message M, compute H(M) using the same hash function, and use public key (e, m) to verify if H(M) = Se(modm) is correct. If the equation is correct, then the signature is accepted.
Security model
In this subsection, we describe the Oracle machines used in the security model. The following symbol descriptions are given in Table 1.
| Symbol | Description |
|---|---|
| List | A list of public keys published by PKI A list of malicious signers that have been compromised or registered by an attacker. |
| MList | We call signers honest signers who are not in MList a list of message signature pairs generated by the challenge oracle query CHb(.,.,.) |
| Gset | Note that an attacker cannot query the message signature pairs contained in GSet through the oracle machine C/D(.,.,.) to acknowledge/deny |
| the algorithm abort | |
| ∖ | the difference between two sets |
| 0̸ | empty set |
| λ | Security parameters |
| PPT | Probabilistic polynomial time |
| Γ | A group of elliptic curve points of order q |
| G | A generator of Γ |
| H1:{0, 1} | Hash algorithm |
| H2:{0, 1}n → G | Hash algorithm |
-
Join Oracle (Add(IDi) → pki): Call Join Oracle Machine in order to add the identification of the truthful signer IDi to the List. The oracle machine returns ϵ if there is already a signer with identification IDi. If not, a key-generating process is executed by the oracle machine, which appends the signer (together with its public key) to the List. At last, pki is returned by the oracle machine.
-
Register oracle machine (Reg(IDi, pki)): An attacker can register a new signer with the public key pki in the List by using a signer to register an oracle. Signers were also added to MList by the oracle machine.
-
Corrupt Oracle (Crpt(IDi, pki) → ski): Corrupting the signatories of the identity IDi by use of a corrupt oracle. The key ski of signer Pi can be extracted by an attacker from the oracle.
-
Signature oracle machine (DRSig(IDk; M, ID1, …, IDk−1, IDk+1, …, IDL′, List) → σ): The signature σ of the honest signer and the entity is output given the identity of the honest signer Pik, message M, and entity Pi1, …, Pik−1, Pik+1, …, PL′ of the signature oracle.
-
Challenge Oracle (Chb(ID0, ID1, M) → σ): Anonymity is defined as using a challenge machine. Given the identity (i0, i1) and message M, the oracle machine provides the target signature S(ski0, M, pki0, pki1) from Pi0 and Pi1 for M for a challenge bit b ∈ 0, 1. Keep in mind that attackers are not limited to weakening signers Pi0 and Pi1. Furthermore, the target’s signature would be protected against an attacker’s ability to execute the Pi0 and Pi1 confirmation/denial protocols. The attacker challenges the oracle machine to add the target signature to the GSet in the event that it is confirmed or denied.
-
Confirm/Deny Oracle (C/D(IDi, M, σ)): Given an identity IDi and a message signature pair (M, σ), a confirm/deny oracle verifies if Pi is an honest signer by executing the confirm/deny protocol and communicating with the attacker. An oracle does not execute the confirmation/denial procedure if an attacker inserts a target signature that questions the results.
On the basis of the mentioned above, we improve the security model mentioned above and provide the necessary characteristics of a deniable ring signature, which are traceability, non-frameability, accuracy, and anonymity.
Our proposed signature scheme
Deniable ring signature
Definition 1. Deniable Ring Signature Scheme
The member (victim) whose public key is used to create the ring signature in a deniable ring signature scheme may assert that false allegations were made against them. Without a group administrator, the scheme is a group signature scheme. To represent the quantity of signers in the system, we use L. According to the definition that follows, the signer Pik dynamically chooses L′ − 1 entities Pi1, …, Pik−1, Pik+1, …, PiL′ from the signer list that PKI publishes, and then performs the signature algorithm by entering their own private key and the entity’s public key collection.
The general construction algorithm for a deniable ring signature is as follows:
-
System initialization (Setup (λ) → params): Given the security parameters λ, output the system parameters params.
-
Key generation (KeyGen (params → (pki, ski))): Output the public–private key pair (pki, ski) of user Ai given the system parameters params.
-
Signing (Sign (m, ski, L) → σ): Given the message m, the user (1 ≤ i ≤ n) private key ski, and public key list L = {pk1, …, pki, …, pkn}, output the signature value. Among them, the public key list L is composed of randomly selecting the n − 1 users’ public key for the user, plus its own public key pki, that is L = {pk1, …, pki, …, pkn}.
-
Verification (Verify (m, σ, L) → accept/reject): given the message m, signature value σ, public key list L, if σ is a legal signature, output “accept”; otherwise, output “reject”.
-
Confirmation (Confirm: P⇔V): The interaction algorithm between the prover P (i.e., signer Ai) and the verifier V, the verifier V has a message m, signature value σ, public key list L, and the prover P proves that the ring signature was generated by it through the confirmation algorithm.
-
Disavowal (Disavow: P⇔V): An algorithm for the interaction between the prover P (non-signer Aj, j ≠ i) and the verifier V, the verifier V has a message m, signature value σ, public key list L, and the prover P denies that the ring signature was generated by the disavowal algorithm.
Security properties
The security model proposed in Komano et al. (2006) gives the required properties of a deniable ring signature: correctness, unforgeability, anonymity, traceability, and non-frameability.
Definition 2. Correctness: We argue that the disavowal ring signature is correct, and the confirmation/disavowal algorithm may identify the signer of the signature if the signature generated by the right signature algorithm is approved by the verification method. With respect to adversary A, safety parameters k, and experiment , we formally characterize the correctness of the deniable ring signature as follows:
-
Initialize the list: List←0̸, MList←0̸, GSet←0̸.
-
Adversary A inquires the oracle machine: (IDk; M; ID1, …, IDL′)←A(1k, Add(⋅), Reg(⋅, ⋅), Crpt(⋅), C/D(⋅, ⋅, ⋅), DRSign(⋅; ⋅, ⋅)).
-
If {ID1, ID2, …, IDi, …, IDn}⁄ ∈ List \MList, then return 1.
-
Simulator calculations , if verified , then return 1.
-
If the returned disavowal algorithm from C/D(IDk, M, σ) executed successfully, then return 1.
-
If the returned confirmation algorithm from C/D(IDj ≠ IDi, M, σ) executed successfully, then return 1.
-
In other cases, return 0.
The definition of adversary A’s advantage is as follows: . The deniable ring signature strategy is correct if the advantage is small compared to any PPT opponent A.
Definition 3. Unforgeability: Through the experiments between simulator S and PPT adversary A to formally define unforgeability. First, the simulator S generates the system parameter and sends it to the adversary, then initializes each list, A adaptive query oracle, output message, public key list, and forged signatures, and then passes through the verification function to verify.
Formal definition: For a deniable ring signature, an arbitrary adversary A, define the experiment as follows:
-
Initialize the list: List←0̸, MList←0̸, GSet←0̸.
-
Adversary A asks the oracle for messages, public keys, and forged signatures: and σ∗ is not obtained by querying the signature oracle machine DRSign(⋅; ⋅, ⋅).
-
For all i ∈ [1, n], the identity IDi⁄ ∈ List \MList corresponding to pki.
-
If , then return 1; otherwise, return 0.
The opponent A’s advantage is defined as follows: . For every PPT opponent A, the deniable ring signature method is unforgeable if the advantage is insignificant.
Definition 4. Anonymity: Through the experiments between simulator S and PPT adversary A to formally define unforgeability. The simulator S generates the system parameter and sends it to the adversary, then initializes each list, A adaptive query oracle, outputs a bit d.
Formal definition: We describe the experiment for a deniable ring signature, an arbitrary adversary A , a bit b ∈ 0, 1, and a security parameter k as follows:
-
Initialize the list: List←0̸, MList←0̸, GSet←0̸.
-
Adversary A inquires the oracle machine, outputs a bit d ∈ 0, 1, return d: d←A(1k, Chb(⋅, ⋅, ⋅), Add(⋅), Reg(⋅, ⋅), Crpt(⋅), C/D(⋅, ⋅, ⋅), DRSign(⋅; ⋅, ⋅)).
Defining the advantages of an adversary A:
.
When the deniable ring signature technique is anonymous, it means that the advantage is negligible in comparison to any PPT opponent A.
Definition 5. Traceability: Traceability means that a real signer of a deniable ring signature can be traced by a confirmation/denial algorithm, through the experiments between simulator S and PPT adversary A to formally define unforgeability. The simulator S generates the system parameter and sends it to the adversary, then initializes each list, A adaptive query oracle, output message, public key list and signatures, and then passes through the verification function to verify.
Formal definition: For a deniable ring signature, arbitrary adversary A, and security parameters k, define the experiment shown as follows:
-
Initialize the list: List←0̸, MList←0̸, GSet←0̸.
-
Adversary A inquires the oracle machine, outputs messages, public key lists, and signatures: .
-
If , then return 0.
-
If users can deny (M, σ), then return 1; otherwise, return 0.
Define the advantage of the adversary A: . If the advantage is negligible against any PPT adversary A, then the deniable ring signature scheme is traceable.
Definition 6. Non-frameability: Non-frameability means that adversary A enables non-signers to deny signatures and ensures that adversary A cannot frame real signers, through the experiments between simulator S and PPT adversary A to formally define unforgeability. The simulator S generates the system parameter and sends it to the adversary, then initialize each list, A adaptive query oracle, output message, public key list and signatures, and then through the verification function to verify.
Formal definition: For a deniable ring signature, arbitrary adversary A, and security parameters k, define the experiment shown as follows:
-
Initialize the list: List←0̸, MList←0̸, GSet←0̸.
-
Adversary A inquires the oracle machine, outputs messages, public key lists, and signatures: .
-
If V(M, σ, pki1, …, pkiL′) = 0, then return 0.
-
If the following conditions are met, return 1; otherwise, return 0.
-
The existence of user Pit cannot be denied (M, σ), t ∈ [1, L]′, i.e., user Pit is not the signer.
-
Adversary A has not been queried Crpt(IDt), or DRSign(IDt; M, ID1, …, IDt−1, IDt+1, .., IDL).
-
Define the advantage of the adversary A: . If the advantage is negligible against any PPT adversary A, then the deniable ring signature scheme is not defamatory.
Scenario description
This section will introduce the design of a deniable ring signature scheme based on ISRSAC, which consists of six PPT algorithms.
-
System initialization (Setup (λ) → params): Given the security parameters λ, output the system parameter params.
-
Key generation (KeyGen (params) → (pk; sk)): Given the system parameter params, the user in the ring performs the following steps:
-
Select two large integers p and q, where p > 3, q > 3, generate n = p⋅q⋅(p − 1)⋅(q − 1), m = p⋅q.
-
Randomly select an integer r that meets the conditions p > 2r < q and generate α(n) = ((p − 1)(q − 1)(p − 2r)(q − 2r))/2r.
-
Select the public key index e to satisfy 1 < e < α(n) and gcd(e, α(n)) = 1.
-
Calculate the private key index d, meet the condition: e⋅d ≡ 1(modα(n)).
-
Output the public–private key pair pk = (e, n), sk = (d, m).
-
-
Signature generation (Sign (m; ski; L) → sig): Given the message M, the private key ski of the signer Ai, the signer forms a list L = pk1, …, pkn of public keys through n − 1 random users’ public keys and their own private keys, hash function H(M):[0, 1]∗ → Zm, perform the following steps:
-
User Ai calculates .
-
The other ring members calculate Sj = H(M)eiej(modn), where j = 1, 2, …, i, …, n.
-
Output (S1, S2, …, Sn) about the ring signature of M.
-
-
Verification (Verify (m; sig; L) → (accept/reject): The verifier receives the message M′ and the ring signature value , and execute the following steps:
-
Calculate the value of H(M′).
-
Calculate the value of .
-
Determine whether there is . If satisfied, output “accept”; otherwise, output “reject”.
-
-
Confirmation (Confirm: (P⇔V): An interaction algorithm between the prover P (i.e., signer) and the verifier V that the prover P can use to prove that it generated the corresponding ring signature. The verifier V has a message M, signature value , and public key list L, and the prover P proves through a confirmation algorithm that the ring signature was generated by it. The confirmation steps are as follows:
-
P → V: The prover selects randomly, calculate R = H(M)t(modn), and sent R to the verifier.
-
V←P: The validator picks at random and sends u to the prover.
-
P → V: The prover calculates w = t − u⋅di(modn) and sends w to the verifier, where . The verifier verifies whether is valid, and if so, determines that the signature is signed by the prover.
-
-
Disavowal (Disavow: (P⇔V): The disavowal algorithm is an interactive algorithm between the prover P(non − signerAj, j ≠ i) and the verifier V, which the prover P can use to deny that a ring signature has ever been generated. The algorithm requires the participation of three parties, three transmissions, and is implemented using the public key system. The unique identity of the user Aj is IAj transformed by the hash function to obtain the corresponding hash value JAj = H(IAj), and the trusted arbitrator T assigns the key function SAj = (HAj)−dj(modn) to Aj. The negative steps as follows:
-
P → V: The prover P chooses a random number r, 1 ≤ r ≤ n − 1, calculates x = re(modn), where r is the secret random number chosen by P, P sends (IAj, x) to V.
-
V←P: The verifier V selects the random number u, 1 ≤ u ≤ e, and sends u to P.
-
P → V: The prover P calculate , send to the verifier V, after V receives y, V calculates IAj from JAj = H(IAj) and , if the result is not equal to x, then the signature is considered not signed by the prover.
-
Proof of security
This section provides proof of the properties of the deniable ring signature based on ISRSAC.
Theorem 1. The deniable ring signature based on ISRSAC satisfies correctness
Proof: Assuming that the disavowal ring signature value of the generated message M is σ = (S1, …, Sn), the correctness of the verification, confirmation and disavowal algorithms of the signature scheme were discussed below.
The correctness of the verification algorithm: Suppose the received message is M′, whose ring signature is composed of the through the H1(⋅) operation in the signature generation algorithm, according to the equation , where and . Then we have: . Therefore, the signature verification algorithm satisfies the correctness.
The correctness of the confirmation algorithm: The signer indicates that the message M has been signed by the confirmation algorithm, and the final verifier needs to verify whether the following equation is established . Because the interaction phase has been calculated: and , it is possible to verify the correctness of the algorithm, that is, to verify the equation. A non-signer cannot indicate that a message M was signed by an confirmation algorithm, because the non-signer does not know di and cannot generate w that satisfies the equation w = t − u⋅di(modn), i.e., a non-signer can only make the equation established by guessing the value of di, , then the probability that the non-signer indicates that the message was signed by the confirmation algorithm is 1/q, which can be ignored.
Theorem 2. If the probability of an adversary A winning in any polynomial time is negligible, then the deniable ring signature based on ISRSAC satisfies unforgeability
Proof: A simulator S can be built to solve the big integer factorization problem with a non-negligible advantage, assuming that there exists a PPT opponent A that is capable of forging signatures.
-
System establishment stage:
-
The simulator S generates system parameters params and sends them to the adversary A;
-
The simulator S initialize the lists: List←0̸, MList←0̸, GSet←0̸;
-
The simulator S sets n ring members , so that each member’s public key is , i = 1, 2, …, n, and sends it to the adversary A.
-
-
Inquiry stage:
-
The adversary A adaptively queries the oracle machine Add(⋅) and returns the user’s public key pki;
-
The adversary A adaptively queries the corrupt oracle machine Crpt(⋅) and returns the user’s private key ski;
-
The adversary A adaptively queries the signature oracle DRSign(⋅) to return the signature value σ = Sign(m, ski, pk1, …, pkn);
-
The adversary A adaptive inquiry confirmation/denial oracle machine C/D(⋅, ⋅, ⋅).
-
-
Challenge stage: The adversary A returns a forged signature σ∗, and for the same signed message and signer identity, if the adversary A successfully forges an unqueried signature σ∗, the ring signature value Si in the ring signature (S1, …, Sn) is generated by in the deniable ring signature scheme based on ISRSAC, and obviously the private key di is required for the signing process. In the event that the adversary A is successful in forging the ring signature, it will be imperative to ascertain the private key di of the ring member Ai. Since the adversary A relies on the challenging task of breaking large integers to crack private keys, the probability σ∗ of the adversary’s successful forgery is small, meaning that the scheme satisfies the unforgeability requirement.
Theorem 3. The deniable ring signature based on ISRSAC satisfies anonymity
Proof: The simulator S generates system parameters params and sends them to the adversary A. The adversary A adaptively queries each oracle machine, and sends the signed message M∗ and the public key ring L∗ = {pk1, …, pkn} to the simulator S. The simulator randomly selects one π(1 ≤ π ≤ n), calculates σπ←RSign(M∗, n, L∗, skπ), and sends σπ to the adversary A.A guesses the corresponding value π′. If π′ ≡ π , then the simulation succeeds; otherwise, the simulation fails.
Assuming that the adversary A’s computing power is unlimited and all publicly available parameter information in the scheme is known, adaptive access to all oracle machines is available. The simulator S randomly selects a ring member w to sign the message m. It can be seen Sj = H(M)eiej(modn) from the deniable ring signature based on ISRSAC algorithm that when w constructing each ring signature value, it is necessary to first randomly generate a public–private key pair that is distinguishable from the existing member, that is, the probability of the ring member generating all Si is 1/n, 1/n, …, 1/n (n in total), that is, the probability of any ring member generating the value of the ring signature is 1/n, 1/n, …, 1/n (n in total). Therefore, the probability that the adversary A can successfully distinguish the real signer among the members in the ring is not greater than 1/n, and the probability of simulation success is negligible, that is, is negligible, so it is proved that the deniable ring signature scheme based on ISRSAC satisfies anonymity.
Analysis of efficiency
The deniable ring signature scheme proposed by Komano et al. (2006), the lattice-based deniable ring signature scheme proposed by Gao et al. (2018), the deniable ring signature scheme based on the elliptic curve discrete logarithmic assumption (EC-DL) proposed by Zeng, Jiang & Qin (2012), and the proposed scheme of semi-trusted third-party anonymous identity authentication mechanism of VANETs (Vehicular Ad Hoc Network), a unique kind of wireless self-organizing network designed to provide communication between vehicles and between vehicles and infrastructure based on blockchain by Jiang et al. (2021), are compared and analyzed below, which further illustrates the benefits of the proposed scheme.
Analysis of communication overhead
We employ the following symbols in our experiments: The symbols p, c, e, m, n, and k represent paring, elliptic curves, exponentiation, and scalar multiplications, respectively. The variables |q|, |z|, and |G| represent the number of bits of the prime numbers q, z and the number of bits of the components in group G.
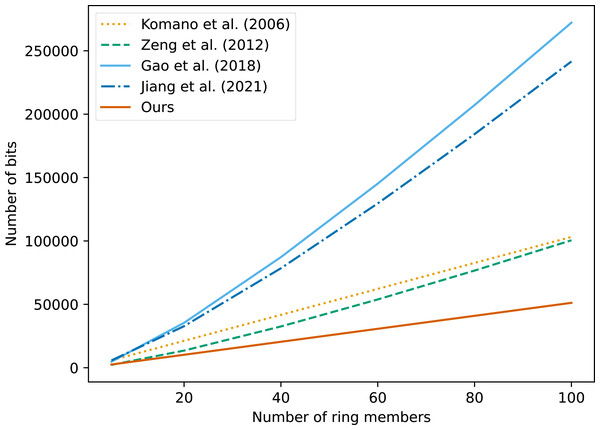
Komano et al. (2006) first put up the idea of deniable ring signature, which is similar to a group signature scheme without the need for a group manager. However, the computational expense of signing and verifying is more than that of group signatures, and the signature algorithm’s communication overhead is (2n + 1)|q| + |G|.
Compared with the scheme of Komano et al. (2006), the deniable ring signature scheme designed based on the SM2 national secret algorithm has less communication overhead in the signature algorithm; that is (n + 2)|q| + |G|, which is more practical.
The deniable ring signature scheme designed by Gao et al. (2018) based on the lattice leads to a larger signature size due to the addition of repudiation, and the scheme can resist quantum attacks, so it has a certain price in terms of signature size, and has non-interaction and repudiation.
The conditional anonymous ring signature scheme proposed by Zeng, Jiang & Qin (2012) under the security model of Komano et al. (2006) is four times faster in the signing and verification stages, and has a constant cost because the scheme confirms and denies the protocol as non-interactive.
In order to significantly reduce the amount of time needed for communication, Jiang et al. (2021) introduced a lightweight anonymous authentication mechanism for VANETs based on the combination of ring signature and blockchain technology. User authentication simply needs to confirm whether the identity information is stored on the blockchain. The blockchain consensus technology simultaneously places the onus of privacy protection on users.
In the deniable ring signature based on ISRSAC algorithm proposed in this study, the output signature value is σ = (S1, S2, …, Sn), where . The communication cost of the signature algorithm is n|q|, that is, the communication cost of the signature algorithm has a linear relationship with the ring member. In the confirmation algorithm, the communication content is t, R, u, w, where , that is, the confirmation algorithm communication overhead is 4|q|. In a disavowal algorithm, the communication content is x, u, y, where , that is, the disavowal algorithm communication overhead is 3|q|. A comparative analysis of the above programs is shown in Table 2.
| Scheme | Algorithm | Sign | Confirm | Disavowal | Interactivity |
|---|---|---|---|---|---|
| Komano et al. (2006) | Zero-knowledge proofs | (2n + 1)|q| + |G| | 3|q| + 3|G| | (4|q| + |z| + 2|G|)v | Yes |
| Gao et al. (2018) | Lattice | 2lnmlogp + 2ln + (m + 1)nlogp | nmlogp | 2mn | No |
| Zeng, Jiang & Qin (2012) | EC-DL | 1p + 4e + nm | 3p + 3e + nm | 3p + 6e | No |
| Jiang et al. (2021) | Bilinear pairs | 3p + 4e + 3nm | 2p + 3e + nm | 6p + e + 3m | No |
| Ours | ISRSAC | n|q| | 4|q| | 3|q| | Yes |
For visual comparison, we set |q| = 512 bits, |G| = 256 bits. The comparison of the signing communication overhead of each scheme is shown in Fig. 1.
Figure 1: Comparison of communication costs between different algorithms.
Analysis of computational overhead
In the analysis of computational overhead, three schemes of interactive confirmation/denial algorithms are selected for comparison. We use Tmul to represent the point multiplication of elements on G; Tadd to represent the addition of dots of elements on G; TH1 means to execute the hash function ; TH2 means to execute the hash function H2:{0, 1}n → G; Tinv represents the inverse operation performed on . The deny phase is set to round v = 1. The comparison of the computational overhead of the deniable ring signature scheme based on ISRSAC, the deniable ring signature based on SM2 and scheme Komano et al. (2006) is shown in Table 3.
| Scheme | Algorithm | Tmul | Tadd | TH1 | TH2 | Tinv |
|---|---|---|---|---|---|---|
| ISRSAC-based | Sign | n + 1 | – | n | – | – |
| Verify | n | – | 1 | – | – | |
| Confirm | n + 2 | 1 | 2 | – | – | |
| Deny (v = 1) | 2 + e/2 | – | 1 | – | – | |
| SM2-based | Sign | 4n − 1 | 2n − 2 | n | 1 | 1 |
| Verify | 4n | 2n | n | 1 | 0 | |
| Confirm | 10 | 4 | – | – | – | |
| Deny (v = 1) | 10 + z/2 | 6 | 2 | – | – | |
| Komano et al. (2006) | Sign | 4n − 2 | 2n − 2 | 1 | – | – |
| Verify | 4n | 2n | 1 | – | – | |
| Confirm | 10 | 4 | – | – | – | |
| Deny (v = 1) | 10 + z/2 | 6 | 2 | – | – |
In summary, the deniable ring signature based on ISRSAC has good practicality and is suitable for scenarios such as the anonymous authentication system. It can be used to implement an anonymous authentication system in which users can provide a ring signature to prove that they have an identity or authority while still being able to deny their own signature and protect personal privacy.
In digital asset transactions, anonymity and non-repudiation of transaction behavior are ensured. Trading participants can use a deniable ring signature to prove that they have sufficient funds to trade while also denying their own signature, preventing others from tracking the flow of their funds.
In secure communication, it can be used to ensure the confidentiality and non-repudiation of communications. The sender can sign messages using a deniable ring signature while denying its own signature, protecting the confidentiality of the communication and avoiding denial signatures by third parties.
In digital proof of stake, it can be applied to digital proof of stake, such as digital copyright protection. Copyright owners can use a deniable ring signature to prove that they own copyright to digital content while also being able to deny their own signature to prevent others from denying copyright attribution.
In summary, the deniable ring signature based on ISRSAC demonstrates good practicality and is suitable for scenarios such as anonymous authentication systems. It can be employed to establish an anonymous authentication system wherein users can furnish a ring signature to authenticate their identity or authority yet retain the ability to repudiate their own signature, thus safeguarding personal privacy.
Conclusions
This article proposes a deniable ring signature scheme based on ISRSAC, which combines the anonymity and repudiation characteristics of ring signatures, which can provide privacy protection in scenarios such as electronic voting and regulatory blockchain and meet the needs of signer tracking at the same time. This technology allows individuals to vote or conduct transactions without revealing their identity. At the same time, it includes methods for identifying the actual participants if needed. This feature addresses the need for privacy protection and tracking of actual participants, especially in electronic voting and regulated blockchains. This article describes the specific algorithm process of the scheme implementation, proves the security of the deniable ring signature, compares and analyzes the communication cost and computational overhead of the proposed scheme and the current deniable ring signature scheme, and the results show that the proposed scheme has obvious advantages in communication overhead and computational overhead, which is applicable to practical scenarios.
In terms of specific implementation, the scheme is based on the ISRSAC signature algorithm, which has higher security than an improved RSA algorithm. The scheme makes full use of the features of ISRSAC and combines the mechanism of deniable ring signatures to achieve the goal of satisfying both privacy protection and signer tracking.
From the practical point of view, the communication overhead and computing overhead are analyzed, and the results show that the proposed scheme has relatively low communication cost, which is beneficial for resource-constrained environments, and the low computational overhead of the scheme can have good practicability in practical applications.
Future research directions could include further optimizing the performance of deniable ring signature schemes, particularly in handling large-scale data and improving signature efficiency. Additionally, exploration could focus on extending this technology to scenarios involving multiple parties and further investigating its potential applications in privacy protection and identity verification to meet the growing demands in electronic voting and regulated blockchain domains. These studies will help further emphasize the importance and practicality of deniable ring signatures in information security and privacy protection.