Indistinguishability under adaptive chosen-ciphertext attack secure double-NTRU-based key encapsulation mechanism
- Published
- Accepted
- Received
- Academic Editor
- Anwitaman Datta
- Subject Areas
- Cryptography, Security and Privacy, Theory and Formal Methods
- Keywords
- Post-quantum cryptography, Key encapsulation mechanism, NTRU, Lattice-based cryptography
- Copyright
- © 2023 Seyhan and Akleylek
- Licence
- This is an open access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, reproduction and adaptation in any medium and for any purpose provided that it is properly attributed. For attribution, the original author(s), title, publication source (PeerJ Computer Science) and either DOI or URL of the article must be cited.
- Cite this article
- 2023. Indistinguishability under adaptive chosen-ciphertext attack secure double-NTRU-based key encapsulation mechanism. PeerJ Computer Science 9:e1391 https://doi.org/10.7717/peerj-cs.1391
Abstract
In this article, we propose a double-NTRU (D-NTRU)-based key encapsulation mechanism (KEM) for the key agreement requirement of the post-quantum world. The proposed KEM is obtained by combining one-way D-NTRU encryption and Dent’s KEM design method. The main contribution of this article is to construct a D-NTRU-based KEM that provides indistinguishability under adaptive chosen-ciphertext attack (IND-CCA2) security. The IND-CCA2 analysis and primal/dual attack resistance of the proposed D-NTRU KEM are examined in detail. A comparison with similar protocols is provided regarding parameters, public/secret keys, and ciphertext sizes. The proposed scheme presents arithmetic simplicity and IND-CCA2 security that does not require any padding mechanism.
Introduction
Public-key cryptosystems (PKC) are commonly used for essential purposes such as key sharing, authentication, and data encryption. Today, Diffie-Hellman (DH) key exchange (KE) (Diffie & Hellman, 1976) and RSA encryption/key encapsulation mechanism (KEM) (Rivest, Shamir & Adleman, 1978) are some of the widely used PKC. Shor’s algorithm (Shor, 1994) proposed a polynomial-time solution to some computationally hard problems that guarantee the security assumptions of traditional PKC. It provides a solution to integer factorization (IF) and discrete logarithm problems (DLP) in polynomial time on a sufficiently large quantum computer. The requirement for constructing post-quantum secure PKC has emerged. While it will take time to build large-scale quantum computers, many initiatives exist to obtain post-quantum secure communication. In 2016, NIST started a standardization process (National Institute of Standards and Technology (NIST), 2023) to determine the standard PKC for the post-quantum era. One of the post-quantum secure cryptosystem families is the lattice-based constructions that provides worst-case assumptions, strong security guarantees, and relatively efficient applications. The lattice-based Number Theory Research Unit (NTRU) encryption scheme was proposed by Hoffstein-Pipher-Silverman (Hoffstein, Pipher & Silverman, 1998). The security of the NTRU is based on the shortest vector problem. It provides relatively short and easy to construct keys and needs low memory with a high-speed guarantee. Many NTRU-like protocols have been proposed for today and post-quantum secure communication. Some current literature based on the NTRU is examined as follows.
The non-commutative ring structure was used in the MaTRU cryptosystem (Coglianese & Goi, 2005). The linear transformation of MaTRU provided significant speed improvements compared to the NTRU. The comparison analysis shows that MaTRU has a larger public key size than the NTRU, while the secret key size is smaller. In Stehlé & Steinfeld (2011), the secret polynomial distribution of the NTRU was changed. The obtained construction provided efficient and flexible cryptographic structures. The hardness assumption of the proposed scheme was based on the ring learning with errors (RLWE) problem. The chosen-plaintext attack (CPA) resistance of this protocol was also presented. In 2013, ETRU encryption scheme was proposed by changing the algebraic structure of the NTRU (Jarvis & Nevins, 2015). The ring structure of ETRU was obtained by using Eisenstein integers. It is faster than the NTRU since it has smaller key sizes. The security analysis showed that ETRU is secure against chosen ciphertext attacks (CCA). In Karbasi & Atani (2015), ILNTRU was constructed as a modified version of ETRU. The hardness assumption was based on the ring short integer solution (RSIS) and RLWE problems. It also provided indistinguishability under CPA (IND-CPA) resistance. In 2018, IND-CPA secure D-NTRU scheme was proposed in Wang, Lei & Hu (2018). The security of the D-NTRU was explained based on the one-way assumption of the double-encrypted NTRU version. According to the comparison results, the D-NTRU was asymptotically faster than the NTRU. Many NTRU-based cryptosystems were also proposed in the NIST’s standardization project and none was selected as a standard (National Institute of Standards and Technology (NIST), 2023). One of the NTRU-based cryptosystems is Chen et al. (2022). It was designed as a KEM that guarantees IND-CCA2 security in the random oracle model (ROM). Applying the general transformation to the deterministic PKC provided a simple, fast, and compact structure.
In the literature, two methods were generally used to construct IND-CCA2 secure KEM: NAEP transformation (Howgrave-Graham et al., 2003) and Dent construction (Dent, 2003). A pseudo-trapdoor one-way function-based padding mechanism of NAEP provided the IND-CCA2 security (Howgrave-Graham et al., 2003). Dent’s generic KEM construction contains special hash functions to obtain key derivation and masking data based on a one-way CPA secure encryption scheme (Dent, 2003). In this article, we follow the idea of Dent to obtain IND-CCA2 secure KEM as it is simple and does not require any padding mechanism. In addition, the D-NTRU encryption (Wang, Lei & Hu, 2018) was constructed using one-way hash functions that provide one-wayness against CPA security. So, the adaptation of Dent’s approach will be more suitable and simple than NAEP for producing the D-NTRU-based IND-CCA2 secure KEM.
Motivation and contribution
The design of post-quantum secure KEM is one of the significant open problems in the literature. The main aim of this article is to provide an IND-CCA2 secure KEM for this requirement. The proposed KEM is obtained following the D-NTRU encryption (Wang, Lei & Hu, 2018) and Dent’s construction (Dent, 2003). The contributions of this article are summarized as follows:
– This is the first IND-CCA2 secure D-NTRU-based KEM scheme constructed with a one-way encryption function.
– The security analysis of the proposed KEM is given in the ROM. To provide IND-CCA2 security, the hybrid version of Dent (2003) and Shoup (2001) constructions are adapted.
– The proposed D-NTRU KEM is a solution to the IND-CCA2 security of the D-NTRU-based encryption specified as an open problem in Wang, Lei & Hu (2018).
– The constructed KEM provides IND-CCA2 security without any padding mechanism or complex arithmetic operations.
– According to the proposed parameter set, a comparison with similar protocols is also presented.
Organization
The rest of this article is organized as follows: In Section 2, some basic definitions and assumptions are recalled. In Section 3, the proposed D-NTRU-based KEM scheme and its correctness analysis are given. The security analysis against IND-CCA2 and primal/dual attacks are presented in Section 4. The comparisons are given in Section 5. Finally, Section 6 clarifies the conclusions.
Mathematical background
The notations are summarized in Table 1.
| N | : | Dimension |
| : | Polynomial ring. | |
| : | Modulo values. | |
| : | XOR operation. | |
| : | Multiplication in a polynomial ring. | |
| : | is chosen uniformly random from distribution X. | |
| : | For , . | |
| : | For , , where . | |
| : | The main security parameter. | |
| : | Error message. | |
| : | The parameter of polynomial spaces. | |
| For D-NTRU, . | ||
| : | The failure parameters. | |
| : | The inverse of the polynomial x in mod p. | |
| Let . Then, . | ||
| : | The complement of Z. | |
| : | Ternary polynomials. If , then coefficient of is equal to , coefficient of is equal to , and the others are equal to . | |
| Kdf | : | Key derivation function such that . |
| H | : | Hash function such that . |
In 2018, an NTRU variant double NTRU (D-NTRU) scheme was proposed in Wang, Lei & Hu (2018). To explain the main properties of the D-NTRU, the composite NTRU (C-NTRU) was also defined. The hardness assumptions of the C-NTRU and the D-NTRU were based on the traditional NTRU scheme. Since this article aims to obtain the IND-CCA2 version of the D-NTRU, the main properties of the C-NTRU and the D-NTRU are recalled in the following.
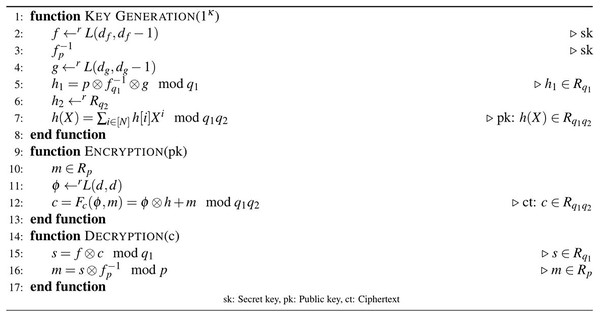
In Wang, Lei & Hu (2018), the C-NTRU was defined to explain the idea of the D-NTRU scheme. Let , , N, and be prime numbers such that gcd gcd . The C-NTRU scheme is recalled in Fig. 1.
Figure 1: Algorithm 1: C-NTRU encryption Wang, Lei & Hu (2018).
In Fig. 1, the composite integers are used as moduli to obtain the public key. In step 7, is computed with the Chinese remainder theorem (CRT), where and for . By following the steps of the key generation function, and are generated as the public and secret keys of the C-NTRU, respectively. The ciphertext of the C-NTRU is obtained by running the encryption procedure with input message . In the decryption phase, is decrypted to with the help of the private key .
Remark 1 If and , then the C-NTRU NTRU (Wang, Lei & Hu, 2018).
Based on the C-NTRU encryption, the C-NTRU one-way problem was defined in Wang, Lei & Hu (2018).
Definition 1 (The C-NTRU One-Way Problem (Wang, Lei & Hu, 2018)). Let be the public key and be the ciphertext of the C-NTRU scheme, where . The main purpose is to find another polynomial pair under the C-NTRU function that produces the ciphertext .
The C-NTRU one-way problem was obtained by following the NTRU one-way problem (Wang, Lei & Hu, 2018).
Definition 2 (The NTRU One-Way Problem (Hoffstein, Pipher & Silverman, 1998)). Let be the public key and be the ciphertext of the NTRU scheme, where . The main purpose is to find another polynomial pair under the NTRU encryption function F that produces the ciphertext .
The hardness assumption of the NTRU one-way problem is recalled in Definition 3.
Definition 3 (The Hardness Assumption of NTRU One-Way Problem). Any probabilistic polynomial time (PPT) algorithm that solves the NTRU one-way problem is negligible for . In other words, for sufficiently large , it is impossible to develop a PPT algorithm to solve the NTRU one-way problem with a non-negligible probability (Howgrave-Graham et al., 2003).
The relation between the NTRU and the C-NTRU one-way problems is given by Fact 1.
Fact 1 Let . Then, the C-NTRU one-way problem is reduced to the NTRU one-way problem in polynomial time (Wang, Lei & Hu, 2018, Theorem 4).
The C-NTRU ciphertext distribution problem is described in Definition 4.
Definition 4 (The C-NTRU Ciphertext Distribution Problem (Wang, Lei & Hu, 2018)). Let be the public key of the C-NTRU scheme. The main purpose is to distinguish the distributions of uniformly random chosen ciphertext and that is produced using the C-NTRU ciphertext function .
The relationship between the C-NTRU one-way problem and the ciphertext distribution is summarized Fact 2.
Fact 2 If , the C-NTRU ciphertext distribution problem is reduced to the C-NTRU one-way in polynomial time (Wang, Lei & Hu, 2018, Theorem 4).
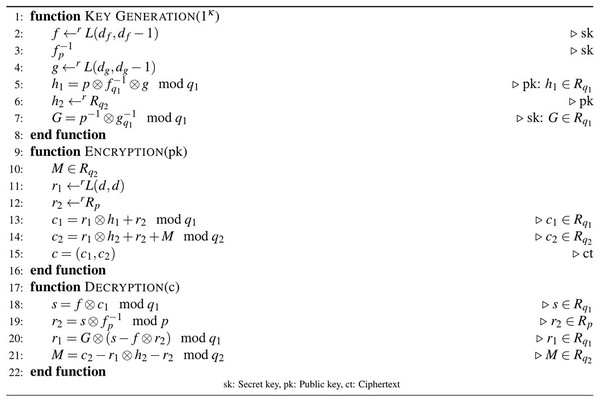
By showing reductions to the C-NTRU properties, the D-NTRU scheme was also constructed to obtain more efficient the NTRU-based public-key encryption (Wang, Lei & Hu, 2018). In the proposed scheme, double encryption is provided with the usage of twin primes. The main structure of the D-NTRU is remembered in Definition 5.
Definition 5 (The D-NTRU (Wang, Lei & Hu, 2018)). Let , N, and . Then, the D-NTRU encryption scheme, using and twin primes, is given in Fig. 2.
Figure 2: Algorithm 2: D-NTRU encryption scheme.
The proposed D-NTRU was designed as a double version of the NTRU that provide one-time pad encryption. The ct component allows some parameters, such as and , to be shared and recovered, while provides one-time pad-like encryption. The D-NTRU encryption scheme using and twin primes is given in Fig. 2.
The relation between secret polynomials and components of the D-NTRU is recalled in Corollary 1.
Corollary 1 Let and be secret polynomials of the D-NTRU. If and , the decryption of the D-NTRU scheme will not fail (Wang, Lei & Hu, 2018, Fact 1).
The conditions to prevent possible errors during the decryption phase of the D-NTRU are explained with Theorem 1.
Theorem 1 Let . If , there is no decryption failure in the D-NTRU (Wang, Lei & Hu, 2018, Theorem 1).
Proof 1 In the D-NTRU algorithm, the decryption parameter must be computed correctly to recover the message. Since , Eq. (1) is satisfied.
(1)
Based on Theorem 1, the relation between the ciphertext and the parameters of the D-NTRU is explained with Theorem 2. Please see the detailed proof of Theorem 2 in Wang, Lei & Hu (2018).
Theorem 2. Let and . Then, there is at most one pair that satisfies for any (Wang, Lei & Hu, 2018).
The invalid ciphertext of the D-NTRU is examined in Theorem 3. Please see the detailed proof of Theorem 3 in Wang, Lei & Hu (2018).
Theorem 3. Let and be the encrypted version of the message M for . For any , and are the invalid ciphertexts of the D-NTRU cryptosystem, where and , respectively (Wang, Lei & Hu, 2018).
The distribution problem of the D-NTRU is recalled in Definition 6.
Definition 6 (The Distribution Problem of the D-NTRU (Wang, Lei & Hu, 2018)). Let be the public key pair of the D-NTRU scheme. The main purpose is to distinguish the distribution of uniformly random chosen ciphertext and the distribution of the D-NTRU ciphertext function .
The relation between Definitions 4 and 6 is summarized with Fact 3.
Fact 3 The D-NTRU distribution problem is reduced to the C-NTRU ciphertext distribution problem in polynomial time (Wang, Lei & Hu, 2018, Theorem 6).
The one-way property of the D-NTRU scheme is explained in Corollary 2.
Corollary 2 Let the D-NTRU distribution problem is reduced to the C-NTRU ciphertext distribution problem in polynomial time. Then, since the C-NTRU scheme provides the one-way property, the D-NTRU scheme also has the one-way property (Wang, Lei & Hu, 2018).
The main properties of the D-NTRU encryption scheme are defined by explaining its relationship with the C-NTRU and the NTRU. In this section, the relations between hard problems and their main properties are expressed to show the one-wayness property of the D-NTRU encryption. Based on Corollary 2 and Dent’s KEM construction (Dent, 2003), the proposed KEM is explained in Section 3.
Proposed scheme
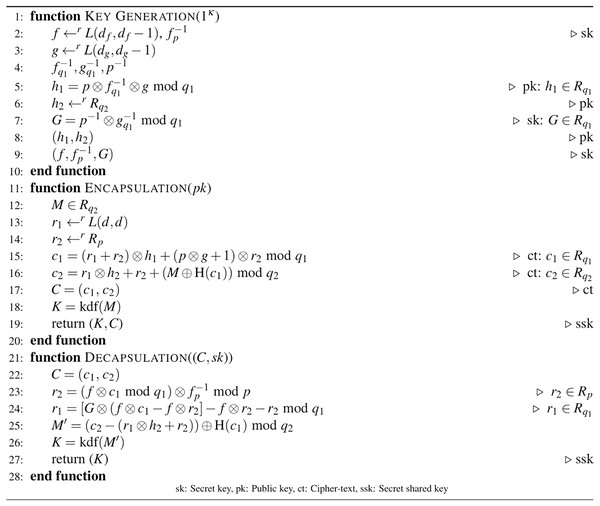
In this section, the proposed D-NTRU based IND-CCA2 secure KEM is detailed. Due to the one-way structure of the D-NTRU encryption function, to obtain IND-CCA2 security, Dent’s one-way KEM construction (Dent, 2003) is added. The basic idea of obtaining the D-NTRU-based IND-CCA2 KEM is based on the modified D-NTRU encryption and Dent’s KEM components. The proposed IND-CCA2 secure D-NTRU-based KEM scheme is given in Fig. 3.
Figure 3: Algorithm 3: D-NTRU-based IND-CCA2 secure KEM scheme.
In Fig. 3, the public and secret keys are generated using the key generation procedure of Algorithm 3. To construct IND-CCA2 secure KEM, Dent’s KEM design idea, based on a one-way function, is used. In the encapsulation procedure of Algorithm 3, the ct components of Algorithm 2 are reevaluated in the following way.
-
is modified as to prevent a IND-CCA2 based attack that is explained in Remark 3.
is changed as to provide one of IND-CCA2 components of Dent (2003).
The encapsulation steps are completed by computing the shared key using Kdf. To decapsulate C, and are recovered using secret keys . Then, the recovered message M′ is used to obtain shared key K under Kdf.
In Fig. 3, Kdf and H functions are used to ensure IND-CCA2 security (Dent, 2003; Shoup, 2001).
-
Kdf: It is a cryptographic algorithm that derives one or more secret keys from various values using a pseudo-random function. It is modeled as ROM based on hash function properties. In the proposed KEM, Shoup (2001)’s Kdf1 function ( ) is chosen as Kdf.
H: : It is a hash function that provides entropy smoothing regarding security properties. For high-entropy input ciphertext byte sequences, the output is computationally indistinguishable from a random byte sequence with the same length. In the proposed scheme, SHA series hash function family and National Institute of Standards and Technology (NIST) (2022) and Shoup (2001)’s Kdf1 functions can be used depending on the choice of .
Correctness
The equality of keys obtained by encapsulation and decapsulation is examined in the correctness analysis of the D-NTRU KEM. In Fig. 3, if step 23 does not work correctly, the decapsulation failure consists. So, the parameters should be chosen according to Theorem 4.
Theorem 4. If , the decapsulation failure does not occur in the proposed D-NTRU KEM.
Proof 2. If the first component of the step 23 in Fig. 3 is rewritten, Eq. (2) is derived.
(2)
Based on Theorems 1 and 2, if is satisfied in the parameter selection, there will be no problem in the correctness.
Let is rewritten with Eq. (3) to show the correctness of the D-NTRU KEM.
(3)
By using Eq. (3), to recover the message M, the running process of the decapsulation procedure is explained with Eqs. (4) and (5). If the step 23 of Fig. 3 is rewritten, Eq. (4) is obtained.
(4)
To decapsulate and , the step 24 of Fig. 3 is reevaluated with Eq. (5).
(5)
The relationship between modulo and distribution parameter is explained in Corollary 3.
Corollary 3 Let and (Wang, Lei & Hu, 2018). Based on Theorems 3 and 4, since , is obtained. To prevent decapsulation failures and invalid ciphertext, must be satisfied. Then, .
Security analysis of d-ntru kem
In this section, the IND-CCA2 security analysis of the proposed KEM and its resistance to some lattice-based attacks are examined.
The IND-CCA2 security of the proposed KEM
In the security analysis, the idea of IND-CCA2 secure KEM from Dent’s one-way IND-CPA secure encryption scheme (Dent, 2003) is followed. The model of IND-CCA2 security is constructed by adapting (Bogdanov, 2005; Dent, 2003; Shoup, 2001) to the D-NTRU problem. The attacker’s behaviors in the IND-CCA2 security are examined based on the game-based security analysis.
In this model, an Attacker (A), modeled as a PPT Turing machine, has the authority to run all algorithms and can obtain all communication-related media. A can also access the decapsulation oracle to decapsulate any capsulated pair. According to Dent’s KEM structure, the proposed KEM is secure unless A has a significant advantage over the Game1 against a mythical challenger.
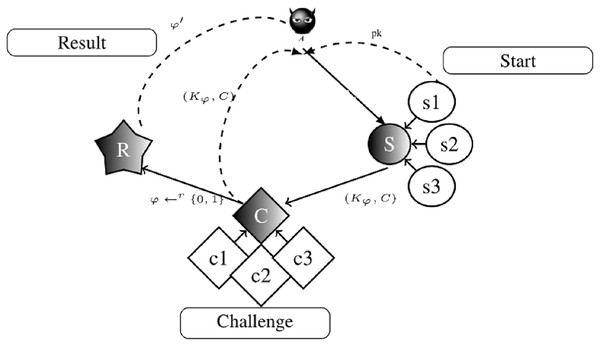
Game1: There are three consecutive operations, such as start, challenge, and result, in the Game1. A aims to gain an advantage in the basic IND game by performing these operations. The visualization sub-steps of Game1 is given in Fig. 4. Figure 4 shows the parameters obtained during the Game1 based on the action of A. The summarized reactions of Fig. 4 are defined as follows.
Figure 4: The basic IND security game steps.
Start: There are three sub-steps.
s1: Based on the security parameter , the key pair is generated by the challenger. is sent to A and is held by the challenger.
s2: A runs until the challenger receives the capsulated key pair. Then, it queries the decapsulation oracle to find the key that is associated with the capsulated key. It is ready to take on a challenge when A made enough queries.
s3: The following steps are taken by the A when generating the encapsulated key pair for the challenger. A submits two different capsulated keys:
Challenge: It is completed when the following sub-steps are done.
c1: The challenger chooses bit and sends the capsulated key to A.
c2: A can perform any number of additional capsulation and computations. According to the number of queries that A can do, the obtained security properties are defined as follows.
In the non-adaptive IND-CCA, A cannot make further requests to the decapsulation oracle before estimating .
In IND-CCA2, A can make further requests to the decapsulation oracle before the prediction, while the challenger ciphertext C cannot be submitted.
c3: A works until he/she generates the guess bit . Then, A queries the decapsulation oracle to find the ciphertext C, which is associated with the capsulated key pair.
Result:
If , A wins the game.
Let be the advantage of A in Game0. In Eq. (6), if is a negligible function of , then the D-NTRU KEM is said to be IND-CCA2 secure.
(6)
Let’s prove that Eq. (6) is negligible in the proposed KEM with Game2.
Game2: In the IND-CCA2 KEM scheme, A can query the decapsulation oracle more than once. Following the idea of Theorem 4 in Dent (2003), the IND-CCA2 analysis of the D-NTRU KEM is examined with Theorem 5. Let;
|H| be the output length of .
T be the execution time of encryption process.
|M| be the space size of .
and be the maximum number of the decapsulation, hash and Kdf oracles queries in the ROM, respectively.
Theorem 5 Let the D-NTRU-(Key Generation, Encryption, Decryption), given in Fig. 2, be a one-way encryption scheme and the D-NTRU KEM be the KEM obtained from this encryption by following Dent’s construction. Suppose that there is an A in the ROM that can break the IND-CCA2 security with probability in time . Then, there is also an algorithm that inverts the underlying one-way encryption function with probability − and in time .
Proof 3 It is shown that if there is an A that breaks the proposed scheme with a non-negligible probability, there will be an algorithm that reverses the underlying one-way encryption scheme with a non-negligible probability. Note that it is assumed that A can query the oracle at any time in the IND-CCA2 security. The following changes are done in Game2.
• The challenger selects the challenge key pair at the beginning.
– If A queries the decapsulation oracle with input , it produces the error term at any time. The only difference compared with Game0 is that A queries the decapsulation oracle with ciphertext C before obtaining . To analyze the effects of this difference on the advantage of A, adapted Lemmas 1 and 2 are used.
Lemma 1 Let and Z be an events such that Pr = Pr . Then,
(7) where |M| and |H| be the message space size and the output length of H, respectively.
Proof Let and be the events that A wins in Game1 and Game2, respectively. Note that if A wins the games, he/she can correctly guess from , where is initially selected at just . Let Z be the event that A asks to decapsulation of C before the challenge is done. If Z does not occur, A can only get the same information when querying oracles. Since, Pr = Pr , is obtained. In the IND-CCA2, the challenge ciphertext is chosen uniformly random from the possible ciphertext distribution. Since and , where in the proposed KEM, decapsulation and hash oracles are queried in the event Z.
The probability that A guesses C with an decapsulation oracle query is and hash oracle is . Since A can make multiple queries, A can obtain and with a total probability , if event Z occurs. So, is only negligibly smaller than since and are negligible in the one-way function.
Lemma 2 Let A has a non-negligible advantage in the Game1. Then, there will also be an A′ with a non-negligible advantage in Game2.
Proof 2 Suppose that there is an A′ who breaks KEM with probability in Game2. He/She runs the algorithm, given in Fig. 5, to reverse the one-way D-NTRU function. At the end of Algorithm 4, the winning probability of A′ is computed. This value is equal to A′’s success in reversing the challenge ciphertext . Let consider Step 3.b.iii in Fig. 5. The probability of obtaining the plaintext that creates the challenging ciphertext is equivalent to the probability that A′ wins Game2. The derivation of includes operation steps based on Kdf and H functions. Let V be the event of querying the Kdf function with at any time. The probability of outputting , which is the plaintext of , is computed with Eq. (8).
Figure 5: Algorithm 4: Possible queries for the security analysis.
(8) when the event V does not occur, A cannot obtain anything about So, . is obtained with Eq. (7). If Eq. (8) is rewritten, Eq. (9) is obtained.
(9)
Since Kdf is modeled as a ROM and the D-NTRU provides one-wayness property, the total number of queries as a function of is negligible. Since Eq. (6) is hold, there is no an algorithm that can reverse the given ciphertext is obtained with a negligible. So, the proposed D-NTRU-based KEM is IND-CCA2 secure.
Basic lattice-based attacks
The security of the NTRU-based protocols is related to the shortest vector problem (SVP). The primal and dual attacks can be carried out for the NTRU-like protocols, such as the D-NTRU encryption and KEM, to find the short vectors in a lattice. Therefore, the parameter set should be chosen so that it is impossible to find short vectors (Elverdi, Akleylek & Kirlar, 2022). The primal and dual attack resistance of the D-NTRU KEM is examined as follows.
Primal attack aims to estimate the hardness of the learning with errors (LWE)-based crptosystems. By constructing an integer embedded lattice, it tries to solve the unique short vector problem (u-SVP). In other words, it reduces the LWE problem to the unique SVP by using the embedding technique. Then, it uses Block Korkin-Zolotarev (BKZ) lattice reduction to find the shortest vector. The hardness of the core-SVP estimates the complexity of the primal attack as , where is the block size of the BKZ algorithm (Liang et al., 2022). So, in the primal attack resistance of the D-NTRU-KEM algorithm, the reduced base is computed with the BKZ-b. In the BKZ-b algorithm, is selected as independent of parameters for bit security level in the local model (Liang et al., 2022; Hoffstein, Pipher & Silverman, 1998). Therefore, the core-SVP cost of primal attack is estimated as for . Similarly, the estimations can be made with or for and for .
A dual attack aims to solve the decisional-LWE problem, which provides the obtaining secret key by recovering part of the secret. This attack is made by using the BKZ algorithm in dual lattices. In the concrete hardness assumptions of NIST’s PQC standard Kyber (National Institute of Standards and Technology (NIST), 2023), dual attacks were not considered since it seems less realistic than the primal attack. Therefore, in the D-NTRU KEM algorithm, the dual attack is not considered since it is much more expensive and impracticable than the primal attack (Albrecht et al., 2018; Liang et al., 2022).
Remark 2 The man-in-the-middle (MITM) attack examination of the D-NTRU KEM is done regarding the distribution parameter of the key generation procedure. In the proposed the D-NTRU KEM, the key polynomials are chosen , and , where . Since in the D-NTRU-based schemes (Wang, Lei & Hu, 2018), MITM analysis is performed according to the key and message security calculations, presented in Table 2. The main security parameter is obtained by selecting the minimum key and message results.
| Primitives | Properties and Components | ||
|---|---|---|---|
| Dimension | : | N | Prime, |
| Mod | : | Twin primes |
|
| Polynomial coefficients | : | ||
| Message security | : | ms bit | |
| Key security | : | ks bit | |
| Security parameter | : | ||
| Public key size | : | pk = byte |
|
| Private key size | : | sk = byte |
|
| Packaged key pair size | : | ct = byte |
|
Remark 3 In the IND-CCA2 security game, when a ciphertext and key K is given, it is wanted to determine whether K is generated uniformly random or ciphertext distribution by using decapsulation oracle. A possible attack scenario in checking IND-CCA2 security is as follows:
Let the ciphertext of the message M be C and . Assume that the first coefficient of was not , so that is still a ternary noise (this happens with probability at least ). Then is an encryption of M′, with noise terms and . Although , the term is unpredictable for the attacker as it contains the component belonging to the secret key. Then, even if and are known, M cannot be obtained from M′ since .
Comparison
In this section, the proposed parameter set and the comparison analysis of the D-NTRU KEM are presented. The parameter set, given in Table 3, is obtained by adapting the NTRU parameters according to the correctness and security analysis. To compare with the NTRU-based schemes, we developed a python script (Seyhan, Akleylek & Dursun, 2023) based on the D-NTRU KEM bounds and the default values of Chen et al. (2022). Table 3 presents the lattice size, modulo, distribution, and the security parameters of proposed the D-NTRU KEM for , , and -bit security levels.
| Parameter set | |||
|---|---|---|---|
| 128 | 192 | 256 | |
| Key security (KS) | 128 | 192 | 256 |
| Message security (MS) | 130 | 193 | 257 |
| N | 509 | 677 | 821 |
| 2,027 | 2,027 | 4,091 | |
| 2,029 | 2,029 | 4,093 | |
| 3 | 3 | 3 | |
| 23 | 35 | 48 | |
| 364 | 470 or 496 | 612 | |
Note:
N, lattice dimension; , moduli values; d, sample distribution parameter; b, primal attack component.
The theoretical basis of the proposed KEM is explained in Table 2. Based on Table 2, the developed script (Seyhan, Akleylek & Dursun, 2023) was used to determine the suitable parameters and sizes. By following the message and key security computation, the values N and are determined for each security level. The twin primes and are chosen to satisfy failure condition , where . The ntruhps (Chen et al., 2022) values were selected as a reference for comparison.
By using Tables 2 and 3, the computed components of the D-NTRU KEM are presented in Table 4. In Table 4, the public/secret keys and ciphertext sizes are obtained in bytes using script (Seyhan, Akleylek & Dursun, 2023). Since no other D-NTRU-based IND-CCA2 KEM exists in the literature, the comparison can be made with the NTRU-based ones such as ntruhps (Chen et al., 2022). According to Table 4, the proposed KEM provides relatively larger key and ciphertext sizes for the same security level. The main parameters such as lattice size, moduli value, error bounds, parameter/message distributions, and security components that cause the differences of compared schemes are expressed in Table 5. Different hard problems and special requirements cause these differences. According to comparison analysis, the proposed method is characterized by the absence of any padding mechanism and arithmetically simple operations.
| Security level | Parameters | N | q | pk | sk | ct |
|---|---|---|---|---|---|---|
| Schemes | ||||||
| 128 | ntruhps2048509 | 509 | 2,048 | 699 | 935 | 699 |
| Ours |
= 2,027 = 2,029 |
1,397 | 1,599 | 1,461 | ||
| 192 | ntruhps2048677 | 677 | 2,048 | 930 | 1,234 | 930 |
| Ours |
= 2,027 = 2,029 |
1,859 | 2,127 | 1,943 | ||
| 256 | ntruhps4096821 | 821 | 4,096 | 1,230 | 1,590 | 1,230 |
| Ours |
= 4,091 = 4,093 |
2,462 | 2,787 | 2,565 |
| ntruhps (Chen et al., 2022) | Ours | |
|---|---|---|
| Assumption | NTRU | D-NTRU |
| Lattice dimension (N) | Prime | Prime |
| Modulo value (q) | gcd(
) = 1 gcd( ) = 1 prime |
|
| Error bound | ||
| SPD ( ) | T | |
| RPD ( ) | ||
| RPD ( ) | T | |
| Message distribution | T | |
| IND-CCA2 structure | NAEP padding | One-way encryption function |
Note:
SPD, secret polynomial distribution; RPD, random polynomial distribution; T, ternary polynomials; , the subset of . coefficient of is equal to 1, the remaining coefficient is equal to −1.
Conclusion
In this article, we construct a novel D-NTRU-based KEM scheme. It provides a solution to define IND-CCA2 security of the D-NTRU-based encryption, an open problem in Wang, Lei & Hu (2018). The security of the proposed KEM relies on the hardness assumption of the D-NTRU problem. Based on the one-way D-NTRU IND-CPA encryption scheme, IND-CCA2 secure D-NTRU KEM is constructed by following Dent’s KEM architecture (Dent, 2003). The detailed security analysis is done in the ROM according to modified Dent assumptions for the D-NTRU-based structures. The basic lattice-based attack evaluations are also presented. The proposed KEM is the first IND-CCA2 secure D-NTRU-based KEM in the literature. It has a simple design and the fact that it does not involve any padding mechanisms. The D-NTRU KEM trivializes the large key and ciphertext sizes. As a future work, we will focus on the D-NTRU-based KEM schemes, including methods such as NAEP padding and their security analysis in the quantum random oracle (QROM) model.
Supplemental Information
Parameter generation.
This script is used to generate the parameter set.