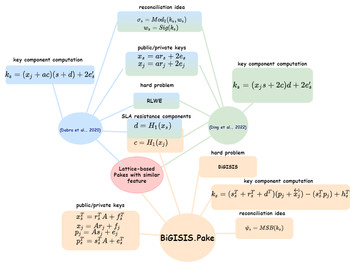
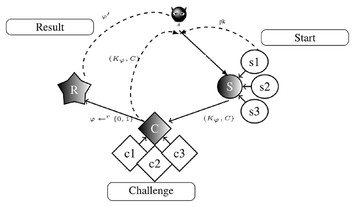
A new lattice-based password authenticated key exchange scheme with anonymity and reusable key
Kübra Seyhan,
Sedat Akleylek
1,467 views · 142 downloads
Modified graph-based algorithm to analyze security threats in IoT
Ferhat Arat,
Sedat Akleylek
1,244 views · 78 downloads
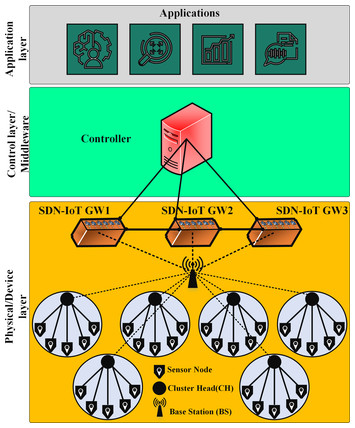
SDN-IoT: SDN-based efficient clustering scheme for IoT using improved Sailfish optimization algorithm
Ramin Mohammadi,
Sedat Akleylek,
Ali Ghaffari
1,511 views · 157 downloads
Indistinguishability under adaptive chosen-ciphertext attack secure double-NTRU-based key encapsulation mechanism
Kübra Seyhan,
Sedat Akleylek
1,075 views · 185 downloads