Modified graph-based algorithm to analyze security threats in IoT
Ferhat Arat,
Sedat Akleylek
1,244 views · 78 downloads
Modelling and verification of post-quantum key encapsulation mechanisms using Maude
Víctor García,
Santiago Escobar,
Kazuhiro Ogata,
Sedat Akleylek,
Ayoub Otmani
1,943 views · 76 downloads
A new hybrid method combining search and direct based construction ideas to generate all 4 × 4 involutory maximum distance separable (MDS) matrices over binary field extensions
Gökhan Tuncay,
Fatma Büyüksaraçoğlu Sakallı,
Meltem Kurt Pehlivanoğlu,
Gülsüm Gözde Yılmazgüç,
Sedat Akleylek,
Muharrem Tolga Sakallı
834 views · 41 downloads
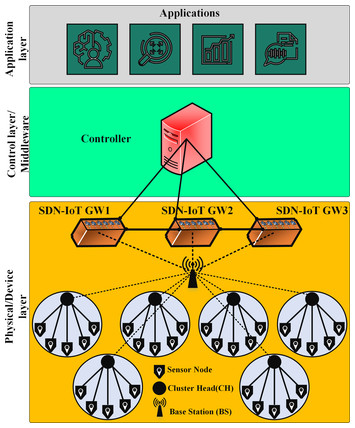
SDN-IoT: SDN-based efficient clustering scheme for IoT using improved Sailfish optimization algorithm
Ramin Mohammadi,
Sedat Akleylek,
Ali Ghaffari
1,511 views · 157 downloads