A structure-preserving linearly homomorphic signature scheme with designated combiner
- Published
- Accepted
- Received
- Academic Editor
- Shi Dong
- Subject Areas
- Algorithms and Analysis of Algorithms, Computer Networks and Communications, Cryptography, Theory and Formal Methods
- Keywords
- Homomorphic signature, Linearly homomorphic signature, Structure-preserving, Linearly homomorphic signature with designated combiner
- Copyright
- © 2024 Zhou et al.
- Licence
- This is an open access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, reproduction and adaptation in any medium and for any purpose provided that it is properly attributed. For attribution, the original author(s), title, publication source (PeerJ Computer Science) and either DOI or URL of the article must be cited.
- Cite this article
- 2024. A structure-preserving linearly homomorphic signature scheme with designated combiner. PeerJ Computer Science 10:e1978 https://doi.org/10.7717/peerj-cs.1978
Abstract
Linearly homomorphic signature (LHS) allows the acquisition of a new legal signature using the homomorphic operation of the original signatures. However, the public composability of LHS also prevents it from being used in some scenarios where the combiner needs to be designated. The LZZ22 scheme designates a combiner and preserves the signature structure by having the signer and the designated combiner share a secret. However, LZZ22 is not secure enough because the secret is constant. Here, we first prove that there is a polynomial time adversary that can crack the secret in LZZ22 through multiple signature queries. Then, we propose a new scheme, which realizes all the functions of LZZ22 and fixes the security problem by changing the secret with the message. The proposed scheme is shown to be secure against existential forgery on adaptively chosen subspace attacks under the random oracle model. Finally, we detail how to apply our scheme to the proxy signature and perform it on a personal computer, and the results show that our scheme is efficient.
Introduction
Linear network coding is an effective technique to improve network throughput. It allows nodes to combine multiple received data packets into one packet and forward it, so as to realize efficient data transmission. However, some malicious nodes in the network may inject forged packets into legitimate packets, and synthesize a corrupted packet that can be forwarded to other nodes. Other nodes in the network combine the corrupted packet with the legitimate packets to synthesize a new corrupted packet and forward it. Due to the nature of network coding, corrupted packets will pollute more legitimate packets, leaving the destination node unable to recover the original data. This type of attack is called a pollution attack. The digital signature (Diffie & Hellman, 1976) is one of the core technologies of cryptography, which can provide authenticity, integrity, and non-repudiation of information. However, the general digital signature scheme cannot be used to solve the pollution attack problem because the original signature becomes invalid once the message is changed. The homomorphic signature (HS) is a type of digital signature that allows any entity to obtain a new legal signature by homomorphic operation on the original signature. Among them, the linearly homomorphic signature (LHS) (Attrapadung, Libert & Peters, 2013) can well resist pollution attacks in network coding because it supports linear homomorphic operations on messages (Zhao et al., 2007; Charles, Jain & Lauter, 2006; Yu et al., 2008; Yun, Cheon & Kim, 2010). With the development of homomorphic signature technology, LHS has also been used in scenarios such as electronic health systems (Li, Zhang & Sun, 2021), blockchain (Lin et al., 2018), and the Internet of Things (IoT) (Li, Zhang & Liu, 2020).
According to the homomorphism of LHS, any entity can obtain the signature of the linear combination of the original messages using the homomorphism operation of the obtained signatures from a set of message/signature pairs with the same label. This is the public composability of LHS. However, in some scenarios such as proxy signing, the user will designate a server that has the unique authority to combine messages and generate a legitimate signature. This allows the designated server to sign instead of the user in special circumstances, such as when it is not convenient for the signer, or if there is too much data. General LHS cannot implement the function of designating a combiner due to its public composability. Designating a combiner means that the signature is homomorphic for the combiner but not for other entities in the system. The linearly homomorphic signature with designated combiner (LHSDC) (Lin, Xue & Huang, 2021) realizes the function of designating a combiner by key agreement. However, the signature structure generated by the combiner was changed (Lin, Xue & Huang, 2021), so that the combined signature cannot continue to be used as the input of the combination algorithm. Li, Zhang & Zhang (2022) proposed the formal definition and security model of structure-preserving linearly homomorphic signature scheme with a designated combiner (SPS-LHSDC) and constructed the first SPS-LHSDC scheme, LZZ22. LZZ22 modifies the signature algorithm based on Lin, Xue & Huang (2021) to make the combined signature structure consistent with the original signature structure. However, this scheme has a security problem.
Our contributions
In this article, we first prove that there is a polynomial time adversary that can crack the secret information in LZZ22 through multiple signature queries. Then, the adversary is able to forge the signature corresponding to any message.
Secondly, we propose a new scheme, which has all the functions of LZZ22 and fixes the security problem by changing the secret information with the message by adding one hash operation and one exponential operation to the signature algorithm. Meanwhile, we detail how to apply our scheme to the proxy signature.
Finally, we run the signature forgery program of LZZ22 through experiments, and the results show that the time required to forge a signature is inversely proportional to the message dimension. We run the proposed scheme in the same experimental environment and compare it with other LHS schemes. The experimental results show that the signature algorithm and the verification algorithm of our scheme are efficient, and that the usage of system resources by our algorithm is low.
Related works
Desmedt (1993) introduced the concept of HS, and Johnson et al. (2002) introduced its formal definition and general framework in 2002. Afterward, many HS schemes appeared (Cheng et al., 2016; Li et al., 2018; SadrHaghighi & Khorsandi, 2016; Catalano, Fiore & Warinschi, 2014; Gorbunov, Vaikuntanathan & Wichs, 2015; Zhang, Jianping & Ting, 2012; Aranha & Pagnin, 2019), including one in which, LHS supports linear homomorphic operations on messages. However, the early LHS schemes lack strict security proof and are not practical. In 2009, Boneh et al. (2009) constructed the first provably secure LHS scheme under the random oracle model. In this scheme, each file is regarded as a linear vector subspace, and the source node signing the basis vectors of the subspace is equivalent to signing the whole file. Gennaro et al. (2010) proposed the first LHS scheme based on the RSA difficult problem. This scheme reduces the cost compared with the scheme in Boneh et al. (2009). To achieve the function of anti-quantum attacks, Boneh & Freeman (2011) proposed the first lattice-based LHS scheme in 2011. The security of the scheme is based on the SIS difficulty problem. The signature verification of the scheme is completed in the binary domain. Chen, Lei & Qi (2016) constructed the first LHS scheme based on the SIS difficulty problem under the standard model. This scheme can resist weak adversaries and provide weak context-hidden privacy. In 2018, Lin et al. (2018) constructed the first ID-based LHS scheme by introducing ID-based signature technology. This scheme uses the user’s identity ID as the public key, which avoids the disadvantage of difficult key management. Zhang et al. (2018) proposed a more efficient ID-based LHS scheme, Zhang18. However, their scheme does not augment the original vector, so it is not suitable for network coding. Moreover, ID-based LHS schemes suffer from key escrow problems. In 2021, Wu, Wang & Yao (2021) constructed a certificate-free LHS scheme Wu21 for network coding. Their scheme avoids both the certificate management problem and the key escrow problem.
Lin, Xue & Huang (2021) and Lin et al. (2017) proposed two LHSDC schemes to make the LHS scheme applicable in scenarios that need to designate a combiner or verifier, Lin17 and Lin21. The latter made up for the former’s lack of public verifiability. In both schemes, only the designated combiner has the right to combine the original signature. However, the combined signature structure in Lin, Xue & Huang (2021) and Lin et al. (2017) has changed, so that the combined signature can no longer be used as the input of the combination algorithm. In 2022, Li, Zhang & Zhang (2022) proposed the first SPS-LHSDC scheme LZZ22 based on the Lin21. In the SPS-LHSDC scheme, the combined signature has the same signature structure as the original signature, so it can still be used as the input of the combination algorithm. This function enables the SPS-LHSDC scheme to be used in certain scenarios. However, the scheme LZZ22 has a security problem.
Organization
The overall structure of the rest of this article is as follows. In the “Preliminaries” section, we introduce some preliminaries. In the “The Security Problem of LZZ22”, we analyze the security of LZZ22 and then construct a signature forgery algorithm for LZZ22. In “The proposed Scheme” section, we propose a new SPS-LHSDC scheme and prove the correctness and security of the scheme. In the “Application and Security Analysis” section, we first describe how to apply the scheme in this article to proxy signature, and then run the signature forgery experiment of LZZ22 and compared the efficiency of our scheme with four other LHS schemes. Finally, we summarize the full text and describe future research directions in the Conclusions.
Preliminaries
Here, we introduce some basics, including symmetric bilinear mapping, the augmented basis vector, and the formal definition of SPS-LHSDC.
Symmetric bilinear mapping
In 1991 Menezes, Vanstone & Okamoto (1991) proposed symmetric bilinear mapping which is defined as follows.
Let and be groups of order . If a mapping satisfies:
Calculability: , solving is efficient;
Bilinear: , , , all satisfy ;
Non-degenerate: , makes .
The mapping is called symmetric bilinear mapping.
Definition 1: (computational Diffie-Hellman problem (CDH)) (Boneh, 1998). Given a triple , where is the generator of , are two unknown elements, solve .
Definition 2: (CDH assumption) (Boneh, 1998). If for any probabilistic polynomial-time (PPT) algorithm , the probability of solving the CDH problem is negligible, then it is difficult to solve the CDH problem in .
The augmented basis vector
In an LHS scheme, a file is usually divided into a set of -dimensional original vectors , where , , is a large prime. To ensure that receivers in the network can recover this set of vectors, the set of original vectors will be augmented to ensure that they are linearly independent. The augmentation operation of this set of vectors is as follows (Boneh et al., 2009): For each , let
(1) where
(2)
Among them, , add a -dimensional unit vector (the -th bit of this unit vector is “ ”, and the rest bits are “ ”) after the basis vector . This set of vectors after the augmentation operation becomes a set of basis vectors of the subspace to which the original file belongs due to its linear-independent property.
The formal definition of SPS-LHSDC
Definition 3: The SPS-LHSDC scheme consists of five PPT algorithms (Li, Zhang & Zhang, 2022):
Setup : The algorithm inputs the security parameter and the dimension N, outputs the system public parameter ;
KeyGen : The algorithm inputs and outputs a private key and the corresponding public key ;
Sign : The algorithm inputs , the signer’s private key , the combiner’s public key , file identifier and vector , and outputs the subspace label and signature ;
Combine : The algorithm inputs , , , and triples , where , outputs a message/signature pair ;
Verify : The algorithm inputs , , , , and . If is the legal signature of vector , the algorithm outputs 1; otherwise, the algorithm outputs 0.
Correctness
The SPS-LHSDC scheme is correct if it satisfies the following two conditions:
1. and , if Sign , then
(3)
2. and , if Verify holds for all , then
(4)
Security model
In the SPS-LHSDC scheme, the forgery of adversary is said to be successful if the forged message/signature pair can pass the verification algorithm, and the forgery conforms to one of the following types of forgery.
Type 1 Forgery: The adversary never queried the subspace V and generates a valid signature for , where .
Type 2 Forgery: The adversary has queried the subspace V labeled , and then uses the label to generate a valid signature for , where .
Type 3 Forgery: The adversary has queried the subspace V, and then generates a valid signature for without knowing the private key of the combiner, where the vector is composed of the basis vector of V and .
Definition 4: If the probability of any PPT adversary winning the following games is negligible, then the SPS-LHSDC scheme is safe.
Setup: The challenger selects the security parameter and a positive integer N and runs Setup , KeyGen in turn. Then sends to .
Combiner-key Generation Query: when initiates this query, runs KeyGen and sends to .
Combiner Corruption Query: When initiates this query, sends a combiner’s public key to , then returns the corresponding to .
Sign Query: When initiates this query, selects a subspace , where , then :
1) For each , augments to , then gets a new subspace .
2) Randomly selects the file identifier , then gets the subspace label for .
3) For each , runs Sign .
4) Returns and to .
Combine Query: When initiates this query, sends to , then runs Combine and returns to .
Forgery: outputs a signer’s public key , a combiner’s public key , a subspace label , a non-zero vector and a signature .
If Verify and one of the following three conditions is true, the adversary is considered to win the above game:
1. for any ;
2. for some but ;
3. for some , , and has not queried the combiner’s private key.
The security problem of lzz22
Here, we first analyze the security of LZZ22 and then perform signature forgery against its security problem.
Security analysis of the LZZ22
Li et al. used a similar method as Boneh et al. (2009) to prove that LZZ22 is secure against existential forgery on adaptively chosen subspace attacks under the random oracle model. However, the security model of the SPS-LHSDC scheme has one more type of forgery (Type 3 Forgery) than Boneh et al. (2009). Li, Zhang & Zhang (2022) actually only proves that the LZZ22 scheme can resist Type 1 Forgery and Type 2 Forgery. Type 3 Forgery exists in SPS-LHSDC because requires that no entity other than the designated combiner combine original signatures to generate a new signature. Type 3 Forgery without knowing the private key of the designated combiner, can obtain the signature of a new message. Below, we analyze the feasibility of Type 3 Forgery in LZZ22.
LZZ22 designates a combiner by binding the combiner’s public key to the signature algorithm. The signer then shares a secret information with the combiner through key negotiation. The secret information can make the signatures generated by the signer temporarily lose the homomorphic property. Therefore, other entities in the system cannot combine signatures, and the combiner who has the secret information can restore the homomorphic property of the signature, thereby obtaining the authority to combine signatures. Thus, the key to realizing the function of designating a combiner is that only the signer and the designated combiner have the secret information. An adversary that can decrypt the secret information in LZZ22 can pretend to be the designated combiner and make any combination of the original signatures to forge a new message/signature pair. Next, we explore a theoretical way to crack LZZ22’s secret information.
In LZZ22, the document will be divided into message vectors , where , , and the signer signs these message vectors, respectively. The signature corresponding to the -th message vector is , where are the generators of , is the subspace label, is a hash map: , is the public key of the designated combiner, is the private key of the signer. , so is the secret information shared by the signer and the designated combiner. However, is a fixed value and can be obtained by division between two different signatures. If the adversary finds out the value of , he obtains the authority to combine signatures, thereby forging a new message/signature pair.
Signature forgery
The specific requirements of Type 3 Forgery in the SPS-LHSDC security model (Li, Zhang & Zhang, 2022) are as follows:
The adversary does not know the private key of the combiner.
has queried the subspace V, that is, knows a set of basis vectors of subspace V and the corresponding signature .
generates a legal signature for a non-zero vector , and must be obtained by a linear combination of .
According to the requirements of Type 3 Forgery and the security vulnerability of the LZZ22 scheme, if the adversary wants to forge the signature of a vector , first needs to find the secret information shared by the signer and combiner by asking for two different signature values (Step 1). The adversary then represents the attempted forged vector with a set of basis vectors of subspace V (Step 2). Finally, the adversary, with the secret information , will be able to assume the identity of the combiner and run the Combine in LZZ22 to obtain the legal signature of the vector (Step 3). The specific steps are as follows:
Step 1: Queries the signature of any message and the signature of message ; get .
Step 2: After querying the subspace V where the message is located, a set of basis vector/signature pairs of the subspace V is obtained, and can be decomposed into
(5)
Step 3: Calculates , respectively, and gets the signature corresponding to :
(6)
The correctness of the message/signature pair is obvious. The key to the successful forgery above is that the adversary finds out the secret information shared by the signer and the designated combiner. This type of forgery satisfies the condition of the Type 3 forgery.
In this section, we find that the root cause of the insecurity of the LZZ22 scheme is that the secret information shared by the signer and the specified combinator is a fixed value, and this fixed value can be easily separated from the signature. Our signature forgery approach can attack some digital signature schemes with the same characteristics: (1) some of the important information in the signature is a fixed value; (2) this fixed value can be derived by arithmetic among multiple signatures. In the next section, we propose a more secure scheme. Compared with the LZZ22 scheme, our scheme adds a hash function value of the message to the index part of the secret information . If the adversary wants to obtain the secret information, it will need to solve the discrete logarithm problem, so our scheme ensures the security of secret information.
The proposed scheme
Here, we first propose a new scheme by fixing the security problem of LZZ22, then we prove the correctness and security of our scheme.
Construction
The proposed scheme is composed of five algorithms, Setup is responsible for generating initialization parameters, KeyGen is responsible for generating public/private keys of the user and the designated combiner, Sign is run by the signer and is responsible for generating the original signature, Combine is run by the designated combiner and is responsible for generating the combined signature from the original signature. The Verify algorithm is responsible for verifying the legitimacy of all signatures. The details of each algorithm are as follows:
Setup : The algorithm inputs the security parameter and a positive integer N, then:
1) Two multiplicative cyclic groups and with large prime are randomly selected, where , a bilinear mapping .
2) The generators is randomly selected in the group .
3) Selects two hash function and .
4) Outputs system public parameter .
KeyGen : The algorithm inputs , when the signer runs the algorithm, randomly selects as the signer’s private key , and calculates as the signer’s public key ; when the designated combiner runs the algorithm, randomly selects as the designated combiner’s private key , calculates as the public key of the designated combiner.
Sign : The algorithm inputs , , , the file identifier and the vector , then outputs the subspace label and the signature
(7)
Combine : The algorithm inputs , , , , and triples , where . The designated combiner calculates and outputs:
(8) (9)
Verify : The algorithm inputs , , , the vector , and the signature . If holds, the algorithm outputs 1; otherwise, it outputs 0.
Correctness
The correctness of the proposed scheme consists of two parts, namely the correctness of the signature algorithm and the correctness of the combination algorithm.
The correctness of the signature algorithm
and , if Sign holds, then
(10)
The correctness of the combination algorithm
and , if Verify holds for all , Combine , where , then
(11)
Security analysis
In this section, we use a game to prove the security of the scheme. Our general idea is to assume that there exists a PPT adversary that can forge a message/signature pair of our scheme with a non-negligible probability . Then we will show that there exists another PPT algorithm , and that can crack the CDH problem by interacting with with another non-negligible probability . According to the CDH assumption that there exists no PPT algorithm that can crack the CDH problem with a non-negligible probability, therefore, we conclude that there exists no PPT adversary that can achieve forgery with a non-negligible probability, thus proving the security of this scheme. In our proof process, we first define the type of queries that adversary is able to make (capabilities of ) and the way replies, and find the probability that is able to successfully simulate the system based on the way replies (the probability that has not given up the simulation). Then, assuming that has output a valid forgery with probability , we find the probability that correctly outputs a solution to the CDH problem using the forgery of . Finally, if all of the above events hold true, we obtain the probability that cracks the CDH problem as . Since , , and are not negligible, is not negligible. By the converse method, we conclude that PPT adversary cannot crack our scheme with non-negligible probability . The specific proof process is as follows.
Theorem 1. If there is a PPT adversary who can break the proposed scheme with a non-negligible probability , then there is another PPT algorithm that can solve the CDH problem with a non-negligible probability , where and , respectively represent the number of Sign Query and Query.
Proof. Suppose there is an adversary that meets the above conditions, then we will construct another PPT algorithm , will call as a subroutine, and obtain from the known public parameters and , where .
Setup: Selects a large integer N, then:
1) Randomly selects , calculates for ;
2) Lets , publishes the parameter ;
3) Sends and to .
Combiner-Key Generation Query: will initiate multiple queries. denotes the -th query as , and guesses that the T-th query corresponds to the final forgery of . creates a list to record this query, and each record in is . When initiates this query, then :
1) If , selects as the private key , then calculates and returns the corresponding public key to ;
2) If , selects , lets the public key . Neither nor knows the private key corresponding to . stores into list and returns to .
Combiner Corruption Query: When initiates this query, sends a combiner’s public key to . If , gives up the simulation, otherwise, queries the list and returns to .
Query: builds a list to record the Query, and each record in is . When initiates this query, sends the subspace label to , then :
1) If has already been queried, queries the list and returns ;
2) Otherwise, selects and calculates for . stores into list and returns .
Sign Query: queries for the signatures of the subspace , then :
1) Selects and let the label of the vector subspace V be . If has already been queried, then aborts the simulation;
2) Lets , calculates for ;
3) Selects a value , lets ;
4) Calculates ;
5) Outputs label and signature .
Combine Query: sends to , if , then gives up this simulation. Otherwise, then :
1) Calculates ;
2) Calculates ;
3) Outputs label and message/signature pair .
Output: In the above process, if does not give up the simulation, the successful forgery of means outputting a quadruple , where , and Verify . If has not appeared in the signature query, computes and outputs , where .
Below we prove that successfully simulates the Setup, KeyGen, and Sign algorithm, and hash function without giving up the simulation. Since the Combine algorithm simulated by runs completely according to the real algorithm, its correctness proof is ignored here.
Since are randomly selected values, are also random values, so successfully simulates the algorithm Setup and KeyGen; and because are randomly selected values, the output of is also a random value, so successfully simulates the hash function . Below, we prove that successfully simulates the Sign algorithm:
For the Sign algorithm, when the input parameter is , where , the corresponding real signature value is:
(12)
Substituting the query value into the above formula, the result of the Sign Query is:
(13)
According to the construction of in the Sign Query, can be known, so the last equal sign in the above formula is established. It can be found that the output of the real signature algorithm Sign is consistent with the output of , so successfully simulates the algorithm Sign.
Below we analyze the probability that does not give up the simulation. Let denote the query number of Combiner-Key Generation Query, Combiner Corruption Query, Query, Sign Query, and Combine Query, respectively. If does not abandon the simulation, the following conditions need to be met during all queries:
The combiner public key corresponding to the final forged result of was not used in times of Combiner Corruption Query initiated by , and this probability is ;
In the Sign Queries initiated by , none of the vector subspace labels used by has been queried by in Query and this probability is ;
In the Combine Queries initiated by , the public key of the combiner corresponding to the final forged result of is not used, and the probability is .
So the probability that does not abandon the simulation is . Below we prove the correctness of the output of when does not give up on the simulation. Let finally outputs the quadruple , and Verify , then
(14)
Substituting the query value into the above formula, we get
(15)
Therefore , if , then . If , will not output the value of correctly. Event occurs in the following three situations:
When the forgery of belongs to the Type 1 Forgery. Since all values of are randomly selected numbers in the space , and , so is uniformly distributed in , then
When the forgery of belongs to the Type 2 Forgery. Since all values of are randomly selected numbers in the space , then in the same way.
When the forgery of belongs to the Type 3 Forgery. All values of are randomly selected numbers in space , and , so the value of is uniformly distributed in , then . Because of , at this time is close to
In summary, the probability of event is We set the probability that successfully outputs a valid signature as , then can correctly output the value of with probability .
Since the CDH assumption is established, the probability of correctly outputting is negligible, so the probability is negligible.
Application and experiment analysis
Here, we illustrate how the proposed scheme works when it is applied to proxy signatures, and then theoretically analyzed the efficiency of our scheme. Finally, the signature forgery experiments on LZZ22 and our scheme are respectively run in the same experimental environment, and the efficiency of our scheme is compared with other schemes.
Application
Digital signature technology can provide authenticity and integrity certification to users. In real life, a large number of signature activities are often required in some departments (e.g., governments and hospitals). Ordinary digital signature schemes do not allow entities other than a specific user to have signing privileges, so users have to accomplish a large number of signing tasks on their own. The linearly homomorphic signature scheme with a designated combiner can improve the efficiency of signing by transferring the user’s large number of computational tasks to a server with high computational power. Consider the following specific scenario:
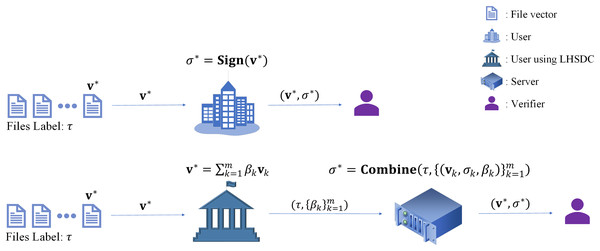
Suppose the user has partitioned the file set labeled into -dimensional vectors , and augmented into a set of basis vectors in the subspace V according to the method in “Preliminaries”. The user has computed the signatures of respectively. At this time, if the user needs to generate the signatures of the data vectors , the user can only re-compute the signature on his own in the ordinary digital signature scheme. In contrast, in the LHSDC scheme, the user only needs to send the label and the combination coefficients to the specified server, and the specified server will complete the signature instead of the user (as shown in Fig. 1). We call this application scenario proxy signing.
Figure 1: The advantage of LHSDC in proxy signing.
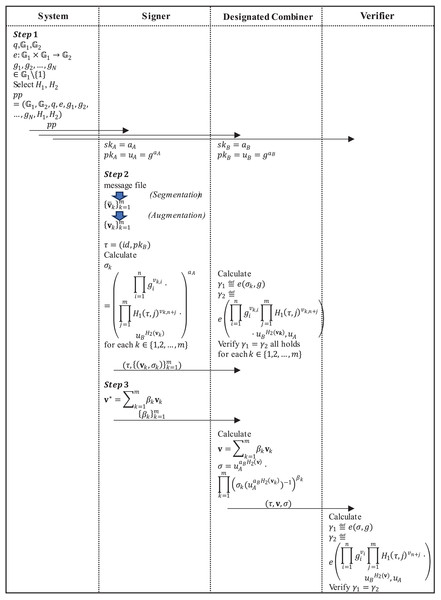
The proposed scheme contains three types of participants when applied to proxy signing, namely the signer (user), the designated combiner (server) and the verifier (Fig. 2). The specific application process is as follows:
Figure 2: The application process of the proposed scheme.
Step 1: The system runs the algorithm Setup to generate the system public parameter and publish to all participants. The signer and the designated combiner run the algorithm KeyGen respectively to generate the private/public key pair of the signer and the private/public key pair of the designated combiner.
Step 2: The signer first divides the message file needing a signature into -dimensional message vectors , and uses the vector augmentation method in “Preliminaries” section to augment each -dimensional message vector into an N-dimensional subspace basis vector . Then, the label of the vector subspace is generated according to the file identifier . Finally, the signer runs the algorithm Sign to sign to obtain , send to the designated combiner, which runs the algorithm Verify to verify the legitimacy of respectively. If are all valid, the designated combiner will store them.
Step 3: When the signer wants to generate the signature of the new message under this subspace, he only needs to express as , and then send the combination coefficient to the designated combiner. The designated combiner runs the algorithm Combine to get , and sends to the verifier. The verifier runs the algorithm Verify to verify the legitimacy of the combined signature .
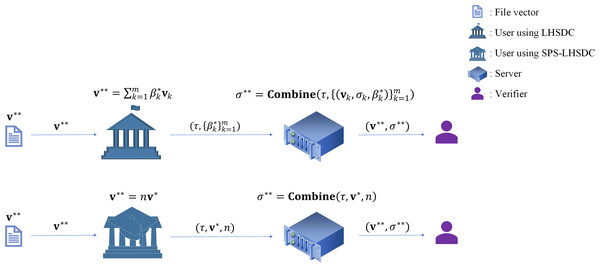
In proxy signing, let us consider another case. After the designated combiner has derived the signature of a certain message by the algorithm Combine, the signer expects the combiner to continue generating the signature of the message . At this point, cannot be used as an input to the algorithm Combine because the signature generated by the combiner is structurally altered compared to the original signature generated by the signer in the LHSDC. The signer must first decompose into , and then the combiner inputs into the algorithm Combine to obtain the signature . Boneh et al. (2009) determined that the process requires pairing operations, exponentiation operations, inverse operations, multiplication operations, and hash operations. In contrast, SPS-LHSDC maintains the signature structure on top of the function of designating a combiner. Therefore, does not need to be decomposed into the form of multiple basis vector representations, and can be directly used as the input to the algorithm Combine. Using our scheme, , the process requires only three exponential operations, one inverse operation, four multiplication operations, and two hash operations. The SPS-LHSDC scheme can significantly reduce the computation of proxy signing as shown in Fig. 3.
Figure 3: The advantage of SPS-LHSDC in proxy signing.
In summary, SPS-LHSDC can reduce the calculation of the signer and improve the efficiency of signing compared with ordinary digital signature schemes and LHSDC schemes. However, since the designated combiner (server) in SPS-LHSDC also has the authority to generate signatures, the server must be under the management of the most authoritative department of the organization. Meanwhile, the SPS-LHSDC scheme does not apply to some departments with high confidentiality due to the irreplaceable nature of the signatures of these departments.
Theoretical analysis
Table 1 illustrates the meanings of the notations used in this section. Table 2 compares our scheme with the other four schemes in Lin, Xue & Huang (2021), Li, Zhang & Zhang (2022), Zhang et al. (2018) and Wu, Wang & Yao (2021) in terms of efficiency and functionality.
| Notation | Operation |
|---|---|
| H | Map-to-point hash operation |
| Exponential operation in | |
| Exponential operation in | |
| Multiplicative operation in | |
| Multiplicative operation in | |
| P | Bilinear pairing operation |
| The size of elements in | |
| The size of elements in , |
| Scheme | Sig.cost | Verify.cost | Signature size | Characteristic |
|---|---|---|---|---|
| Lin21 | LHSDC | |||
| LZZ22 | SPS-LHSDC | |||
| Zhang18 | ID-based | |||
| Wu21 | Certificateless | |||
| Our | SPS-LHSDC |
By comparing with other four schemes theoretically, we find that only our scheme and LZZ22 are able to realize both functions of designating a combiner and maintaining the signature structure. In “The Security Problem of LZZ22”, the LZZ22 scheme was shown to have a security vulnerability, and our scheme was the only secure SPS-LHSDC scheme. Our scheme has the lowest computational overhead for both the signature algorithm and the verification algorithm, thus our scheme is efficient.
Experiment analysis
In this section, we run the signature forgery program of LZZ22 through experiments, so as to obtain the probability and time required for an adversary to successfully forge a signature. Then, under the same experimental environment, we run our scheme and evaluate its efficiency.
The following illustrates experimental environment and parameter selection. We build the simulator in Python and use a 2.6 GHz single-core twelve-thread processor. The parameter params we used in LZZ22’s, Wu21’s and our simulations are from pypbc (Maas, 2004) library’s A-type curve. The parameter params we used in Lin’s and Zhang18’s simulations are from pypbc library’s F-type curve. The security parameter length is 80 bits, and the element lengths in and are 320 and 160 bits respectively. In our experiment, in order to meet the needs of simulating multiple scenarios, the size of the test file we choose is 3.2 KB (3,279 bytes). The file will be divided into blocks, each block contains elements, and each element length is 160 bits, which means that the test file is represented by -dimensional vectors, and the values of and need to meet: . According to the load of the network, we set the packet size as 1,460 bytes. Thus, each packet can hold elements. Therefore, the augmented data packet length N should satisfy: .
Signature forgery experiment of LZZ22
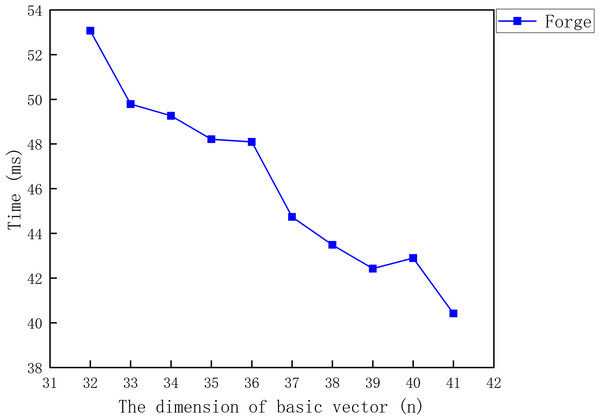
The signature forgery of LZZ22 includes two processes, namely the signature query and the signature forgery. Since the adversary can obtain the signatures , and from the signatures generated by the signer in the past, we ignore the cost of the signature query. The cost of the signature forgery process is consistent with the formula . Figure 4 shows the relationship between the cost required for the signature forgery and the message vector dimension .
Figure 4: The cost of the signature forgery for LZZ22.
From Fig. 4, it can be found that the adversary can forge the signature of LZZ22 in a very small amount of time after the Sign Query. The time required for forging the signature decreases with the increase of the dimension . This is because an increase in is accompanied by a decrease in .
Efficiency analysis experiment of the proposed scheme
Figures 5 and 6 show a comparison between our scheme and the schemes in Lin, Xue & Huang (2021), Li, Zhang & Zhang (2022), Zhang et al. (2018) and Wu, Wang & Yao (2021) from the cost of the signature algorithm and verification algorithm, respectively. Figure 7 shows the CPU and RAM occupancy of each scheme, and Fig. 8 shows the specific usage of RAM for each scheme.
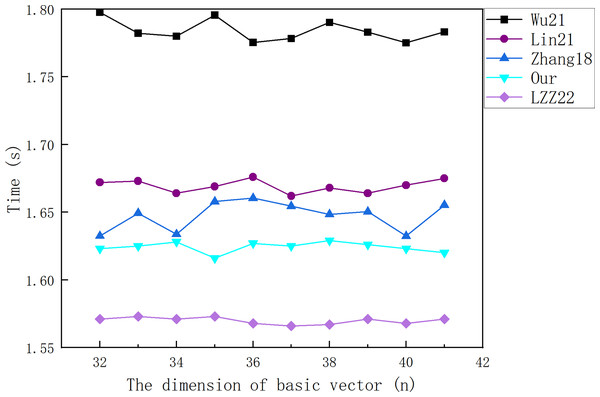
Figure 5: The cost of signing a 3.2 KB file.
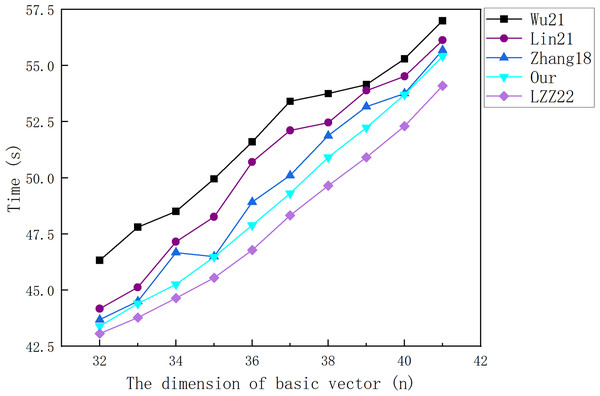
Figure 6: The cost of verifying a message vector.
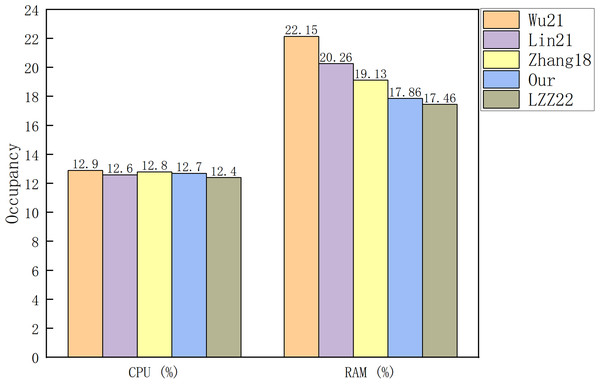
Figure 7: Occupancy of CPU and RAM.
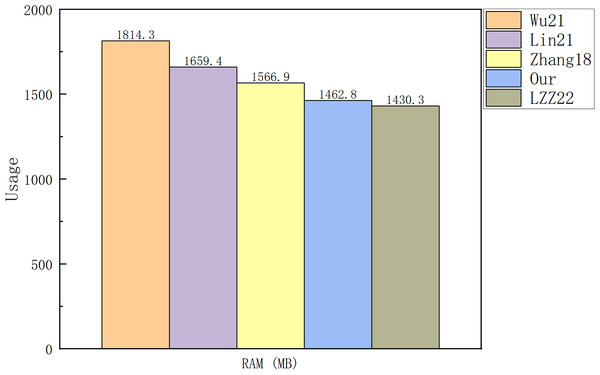
Figure 8: RAM usage.
Figure 5 illustrates that the cost of each scheme in the signature algorithm does not change greatly with the increase of the dimension value of the base vector. This is because an increase in is accompanied by a decrease in , that is, although the length of each data packet increases, a file can be represented using fewer data packets. Figure 6 shows that the cost of each scheme in the verification algorithm increases with the increase of the dimension of the base vector. This is because the verification of each vector needs to add one multiplication operation and one exponent operation due to the increase of .
By comparing our scheme with the experimental results of other schemes, we find that whether signing a 3.2 KB file or verifying a single message vector, the time overhead of the LZZ22 scheme is the smallest, and our scheme is the second smallest. However, we have proved in “The Security Problem of LZZ22” that the LZZ22 scheme has a security vulnerability. Therefore, our scheme has the highest efficiency among the remaining schemes. When the amount of valid data in the packet reaches the maximum value of 41 (n = 41), our scheme takes 1.620 s to sign a 3.2 KB file and 55.406 ms to verify a single data vector under that file.
Figures 7 and 8 illustrate that there is no major difference between the schemes in terms of CPU occupancy. In terms of RAM occupancy, LZZ22 has the smallest memory usage, followed by our scheme. Since the LZZ22 scheme is insecure, our scheme has the smallest usage on RAM among the remaining schemes. When the file size is 3.2 KB, running our scheme will consume of CPU and of system memory. Overall, our scheme has a low computational overhead and system resource usage on top of the simultaneous functionality of designating a combiner and maintaining the signature structure.
Conclusion
Here, we prove that there is a polynomial time adversary that can crack the secret information in LZZ22 through multiple signature queries, which will allow the adversary to forge the signature corresponding to any message. We proposed a new scheme, which has all the functions of LZZ22 and fixed the security problem by adding one hash operation and one exponential operation to the signature algorithm. Our scheme proved secure against existential forgery on adaptively chosen subspace attacks under the random oracle model. We also detailed the application of our scheme to the proxy signature. Finally, we ran the signature forgery program of LZZ22 through experiments, and the results showed that the time required to forge a signature was inversely proportional to the message dimension. The proposed scheme was run in the same experimental environment and compared with other similar schemes. The experimental results show that the signature algorithm and the verification algorithm of our scheme are efficient, and efficiently use the system resources.
It should be noted that in proxy signing because our scheme allows the designated combiner (server) to generate legal signatures, the server must be managed at the highest level in the department. Meanwhile, the SPS-LHSDC scheme does not apply to some departments with high confidentiality due to the irreplaceable nature of the signatures of these departments. In addition, in this article, we only explore the application of SPS-LHSDC scheme in proxy signatures, and some other application scenarios that need to specify servers for calculating such as federated learning, cloud auditing, and so on deserve more in-depth research. Although the proposed scheme is more efficient than the existing LHSDC scheme and is the only secure SPS-LHSDC scheme, there is still room for improving the efficiency of the signature algorithm. Two directions deserve further research to improve the efficiency of the signature algorithm. One of them is to optimize the homomorphic hash function, which can significantly improve the efficiency of the scheme. The other is to optimize the way to bind combiners, that is, to find a way to bind combiners other than key exchange, which can improve the efficiency of the scheme by a small margin.
Supplemental Information
Raw data on time cost obtained after repeated experiments for 50 times.
The time cost of LZZ22's forgery algorithm (forge), the time cost of our scheme and other schemes' signature algorithm (sig), the time cost of our scheme and other schemes' verification algorithm (ver), the percentage of system resources occupied by our scheme compared with other schemes (prop), and the RAM usage of our scheme and other schemes (num).
Code.
The code of scheme Lin21 (LIN21), the code of scheme LZZ22 (LZZ22), the code of our scheme (OUR), the code of Wu21 (Wu21), and the code of Zhang18 (Zhang18). Each part contains a signature algorithm and a verification algorithm. Among them, the code of our scheme (OUR) also includes the algorithm of forging LZZ22 signature. The output of all the code is the average time cost obtained by repeating 50 experiments.